Nowadays, more and more people are using VPN (virtual private network) for different purposes. For one of them that’s a good stuff to hide their internet activities, others use VPN for evading blocking particular web-sites, the least just wants to build common virtual LAN to communicate with their devices. Despite the end purposes, VPN can help to reach all of that aims.
In spite of the human nature or material status, free applications as well as VPN sources are more attractive to people. But is it safe enough to use free virtual private network in day-to-day activity or at least during particular cases? Let’s consider that.
0. Software
Before we dig deeper, we have to negotiate what applications we will use during our experiment.
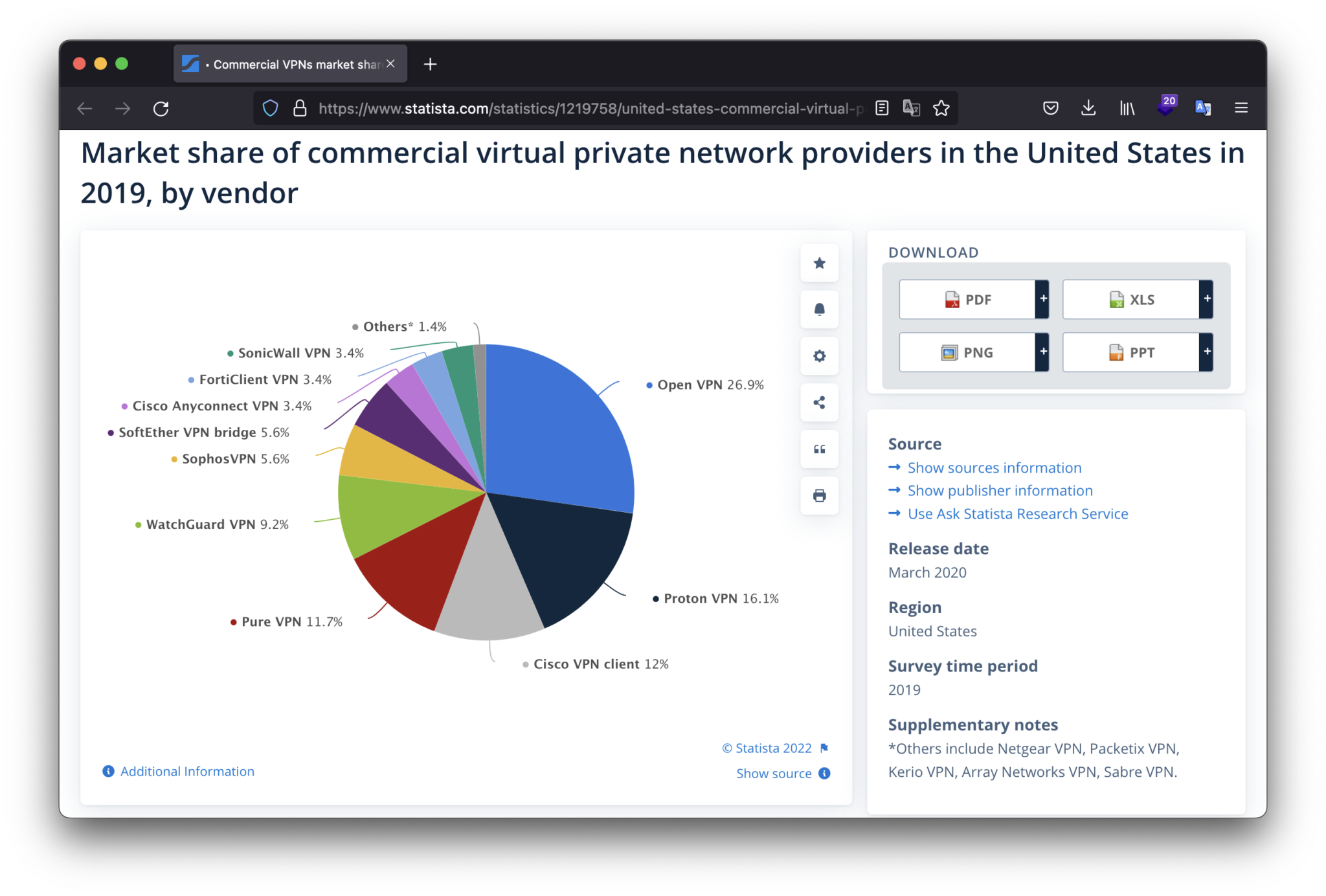
According to Statista.com web-site, the most popular virtual private network provider in the United States in 2019 is Open VPN, which has more than a quarter of the market share.
So, what is Open VPN?
Open VPN is a virtual private network (VPN) system that implements techniques to create secure point-to-point or site-to-site connections in routed or bridged configurations and remote access facilities. Open VPN allows peers to authenticate each other using pre-shared secret keys, certificates or username/password. It uses the OpenSSL encryption library extensively, as well as the TLS protocol, and contains many security and control features. It was written by James Yonan (https://www.linkedin.com/in/james-yonan-626b6251/) and is free software, released under the terms of the GNU General Public License version 2 (GPLv2). © Wikipedia – https://en.wikipedia.org/wiki/OpenVPN
Interesting. Due to its widespread and popularity, I would suggest to use Open VPN as our main application during the test.
For properly using Open VPN, we have to go to its official web-site (https://openvpn.net/vpn-client/) and download the OpenVPN Connect client based on your preinstall operation system.
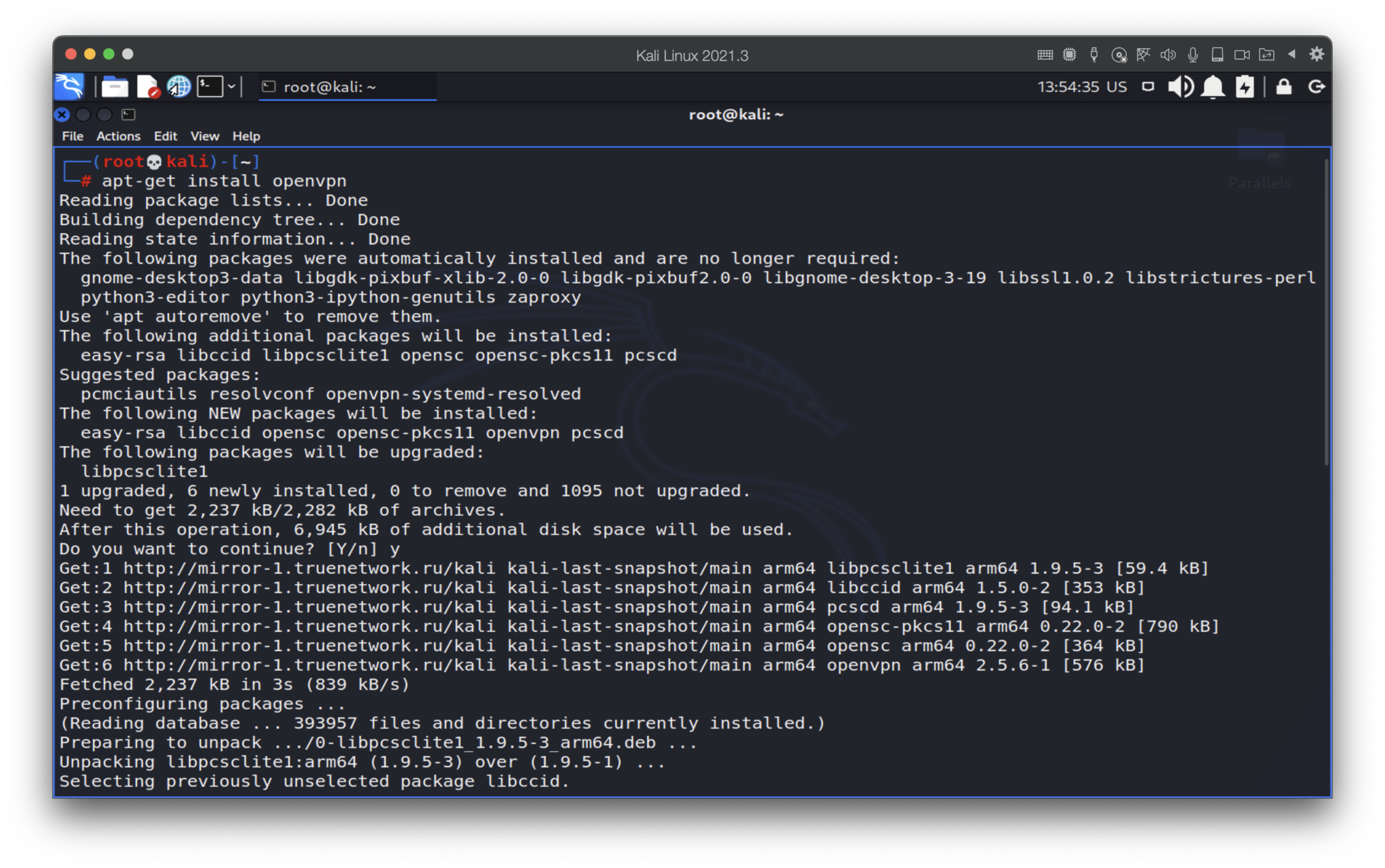
For the test, we are using Kali Linux which has already preinstalled client. But, if you accidentally deleted the last one or using other Debian-based OS, you may freely download that by the following command:
apt-get install openvpn
Now, let’s try it out:
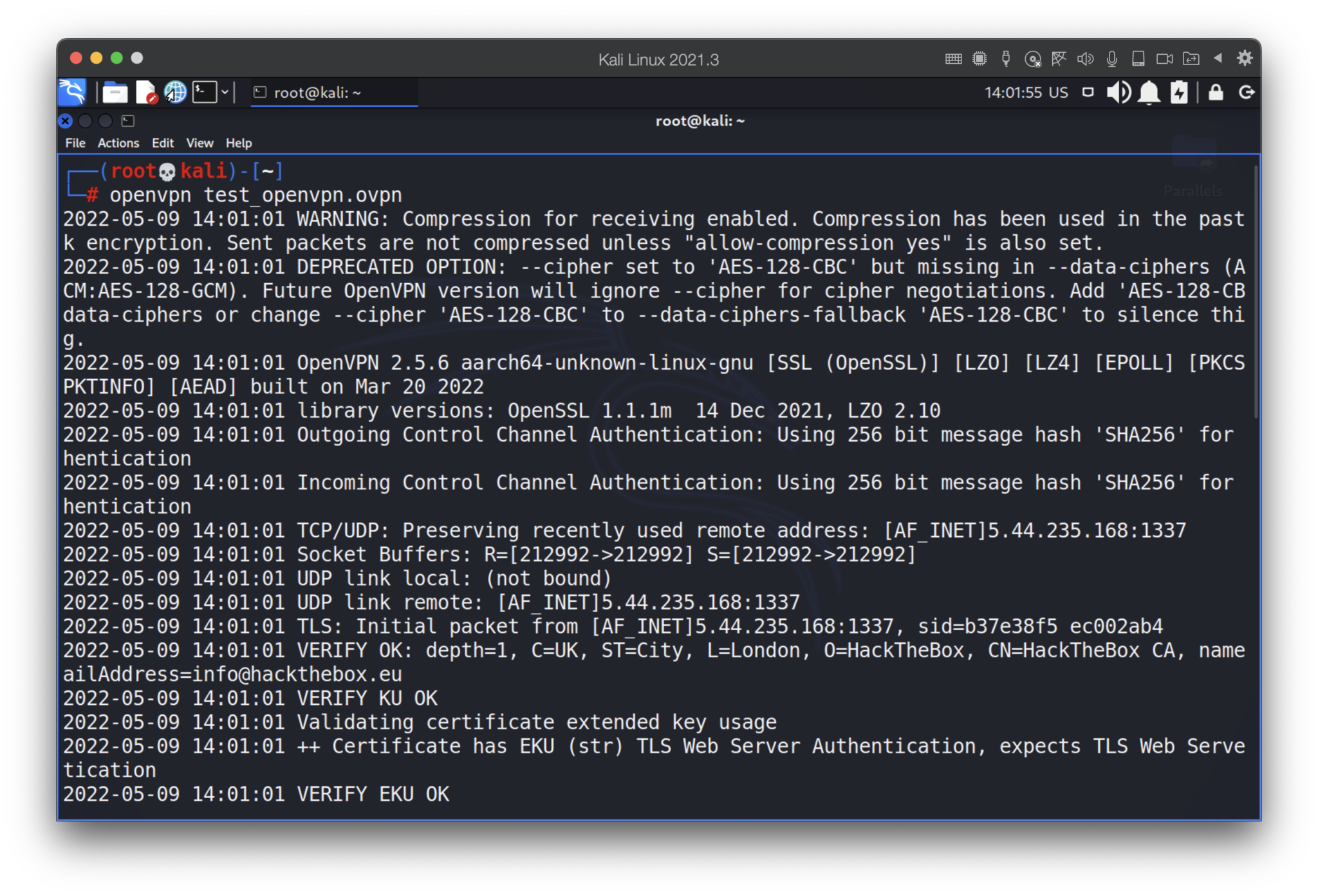
“Initialization Sequence Completed” message notify us the connection has been established. The final step is to check that by “ip a” command.
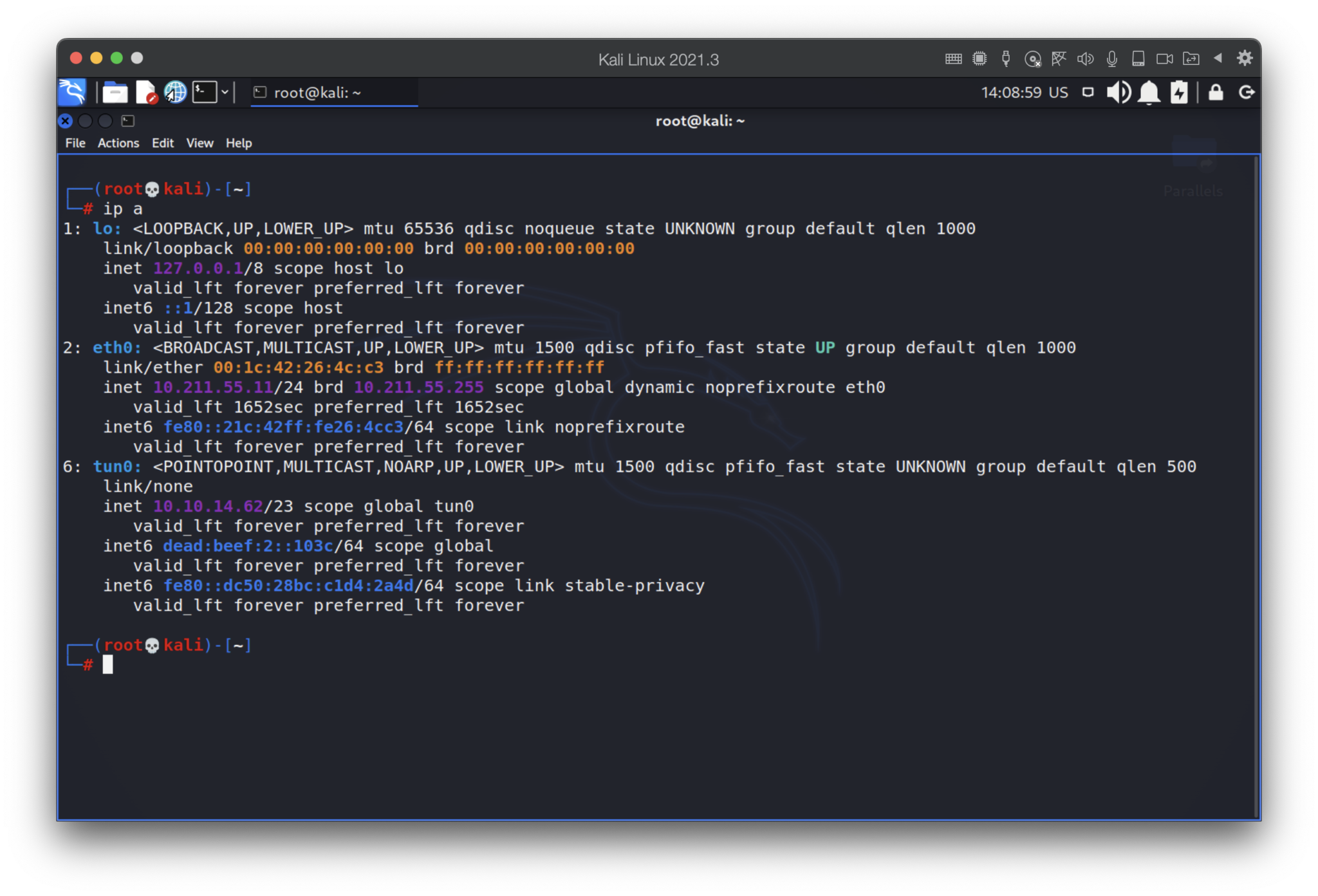
Perfect, the connection is up: tun0 is working as intended. Now, let’s consider some free OpenVPN connections 🙂
1. FreeOpenVPN
We will start with one of the famous services on the internet – freeopenvpn.org. The web-site states you “stay anonymous on the Internet, have a secure connection…” and other attractive functionality. But is it exactly as it mentioned? Let’s check it out.
To test it we are going to download a Netherlands UDP ovpn file and then launch it.
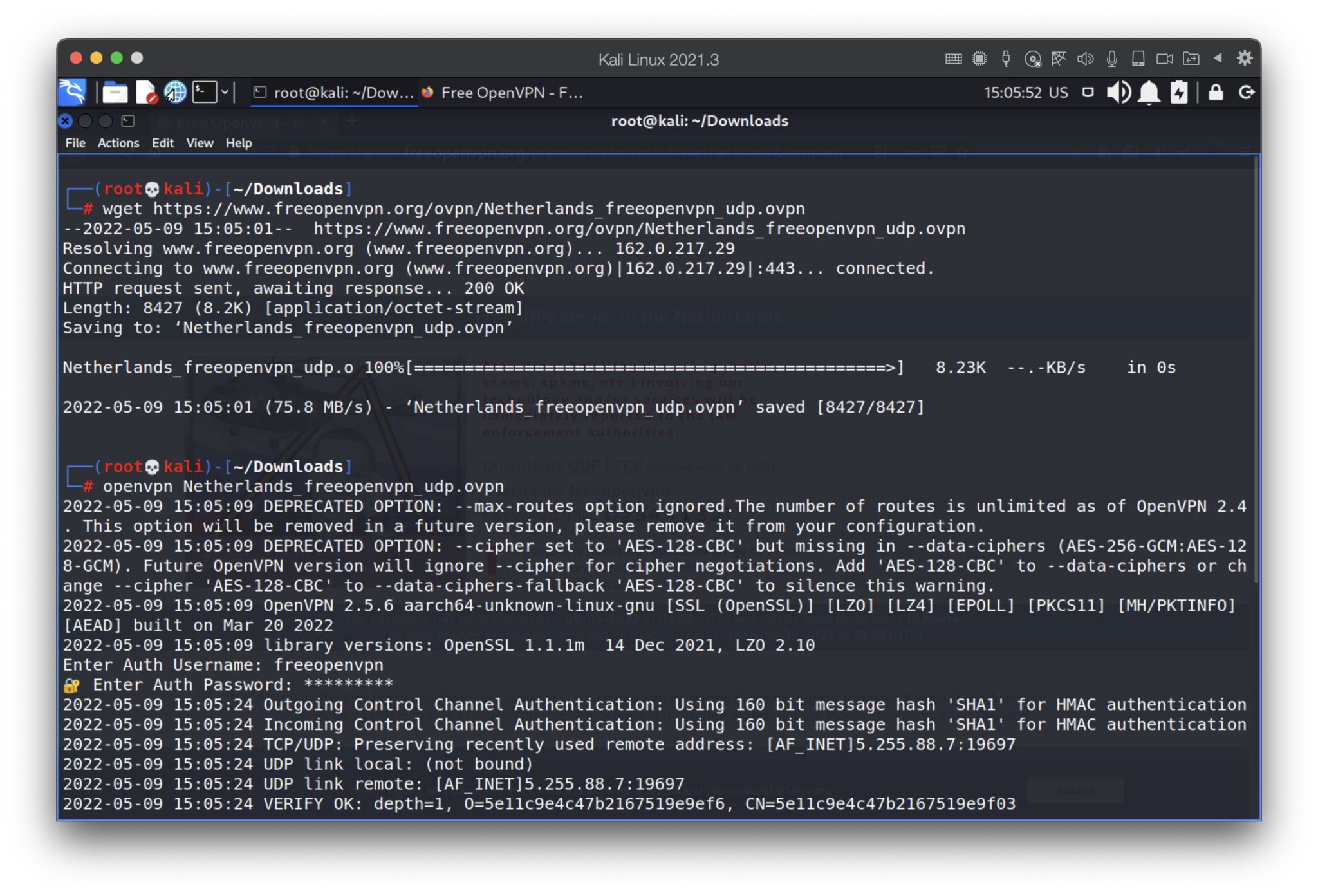
Nice. Our IP address is 192.168.242.234 and subnet mask is 24.
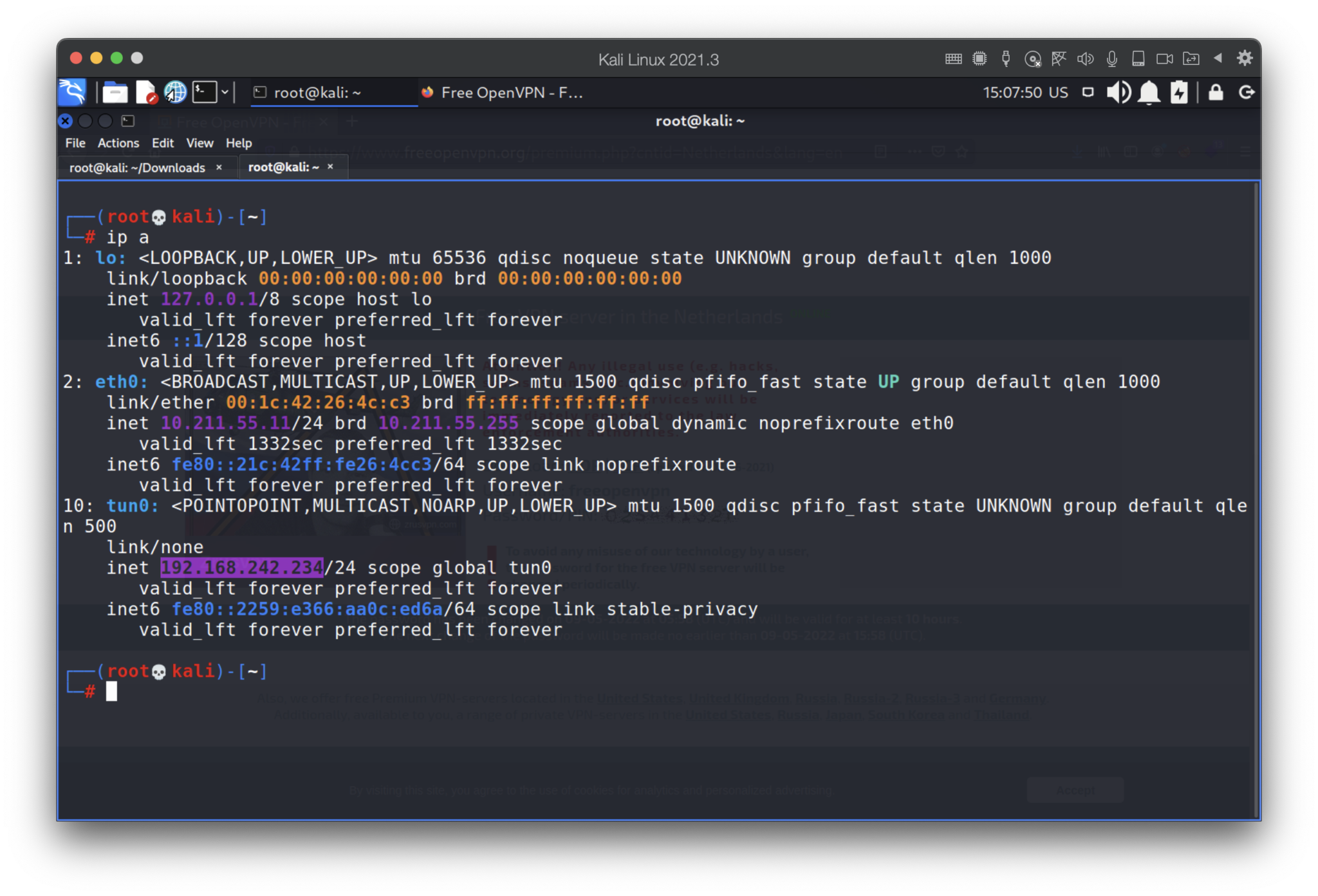
Hmmm, interesting… Why the mask is 24? Let’s try to enumerate the subnet.
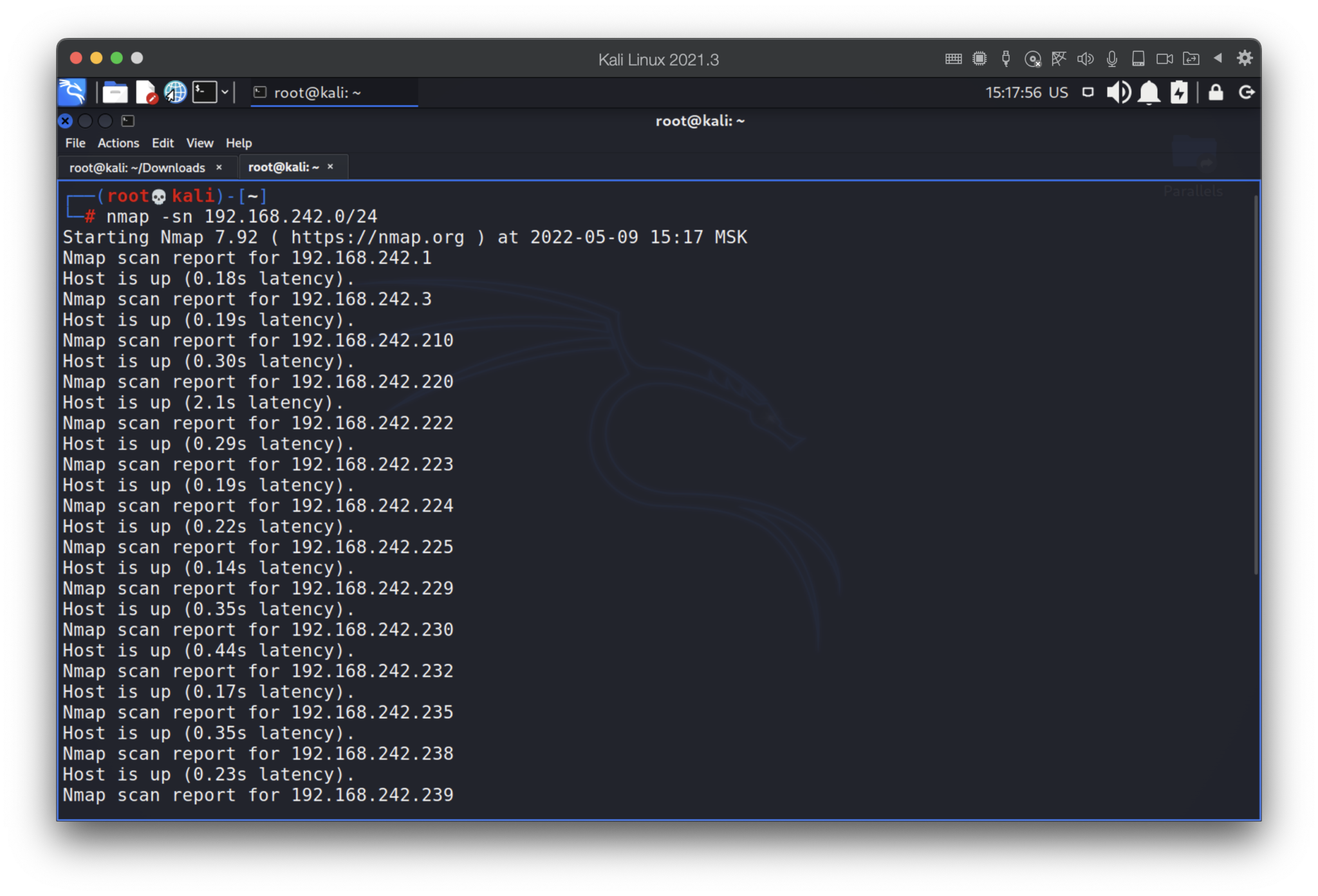
Wow, that’s really unexpected. What if some of those hosts have open ports? We will check only 80 and 445 ports.
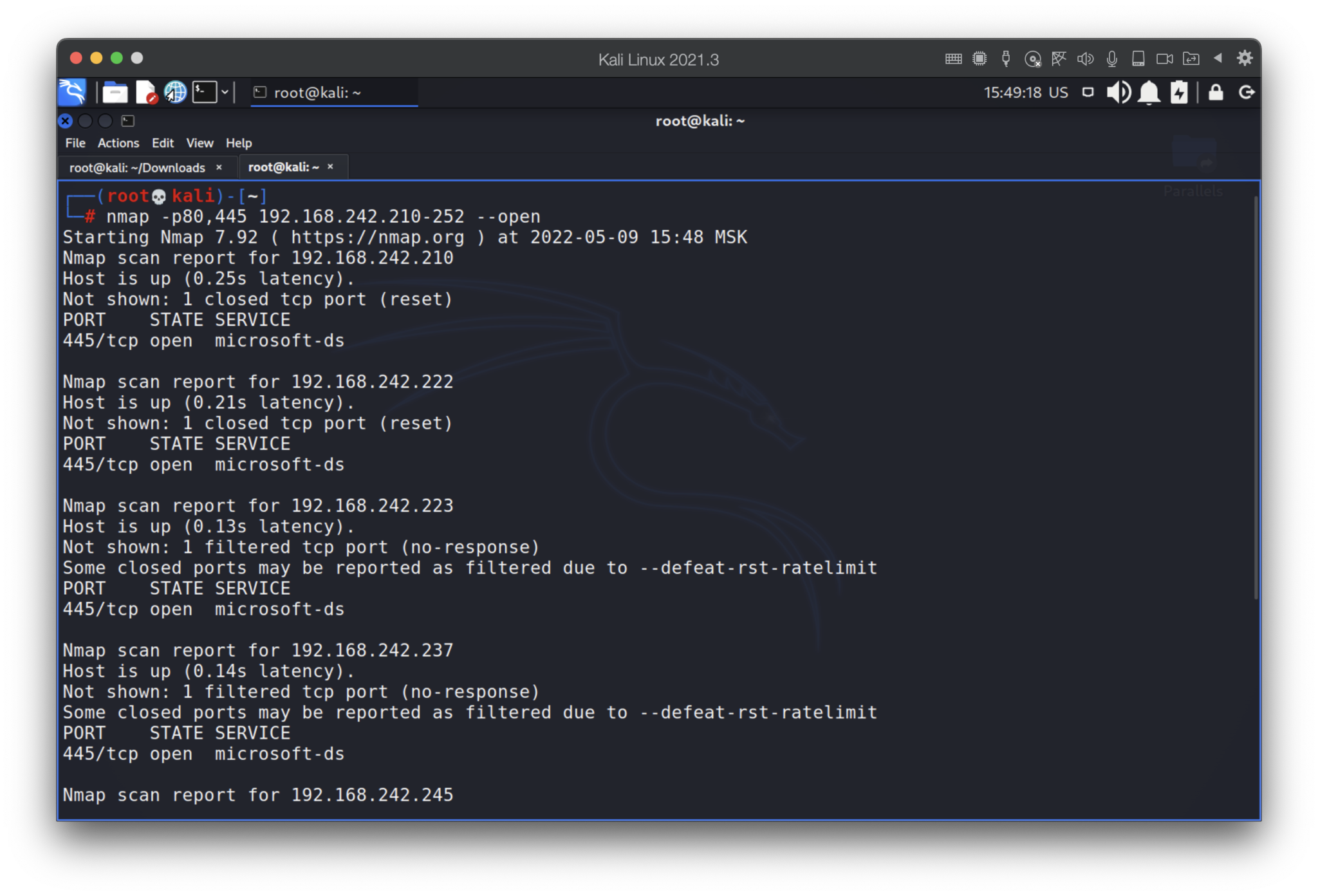
Ok, we got something. Let’s check them out.
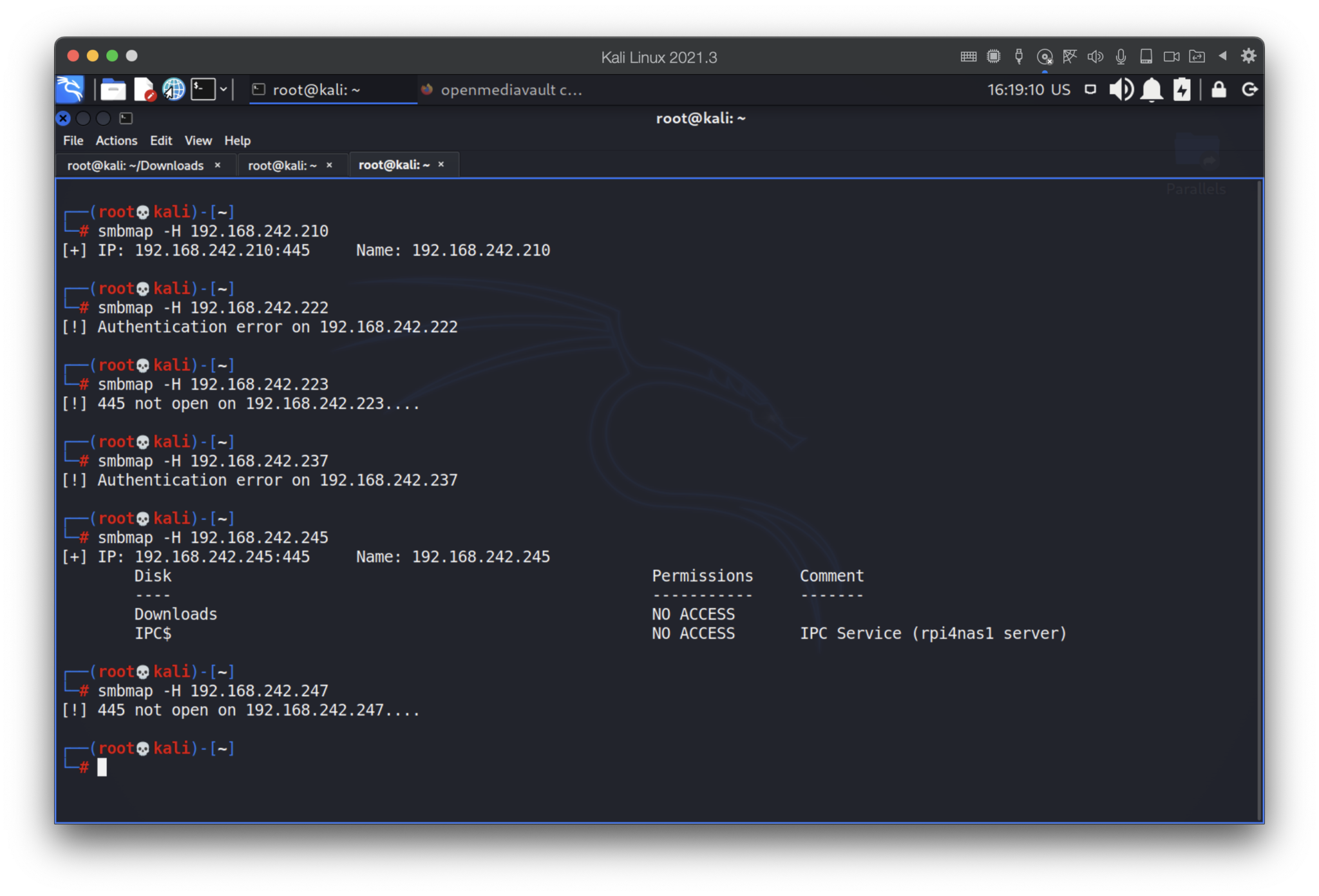
We won’t try to brute force or use default password due to that’s illegal, black hatted and just unethical. But I assume you have already realized that when you connect to the VPN, you become one of the hosts of the huge network and anyone across the globe can/may hack your system.
2. VPNBOOK
The next in our list is vpnbook.com service. I knew about that from Russian Linux forum Losst by the link https://losst.ru/spisok-serverov-openvpn
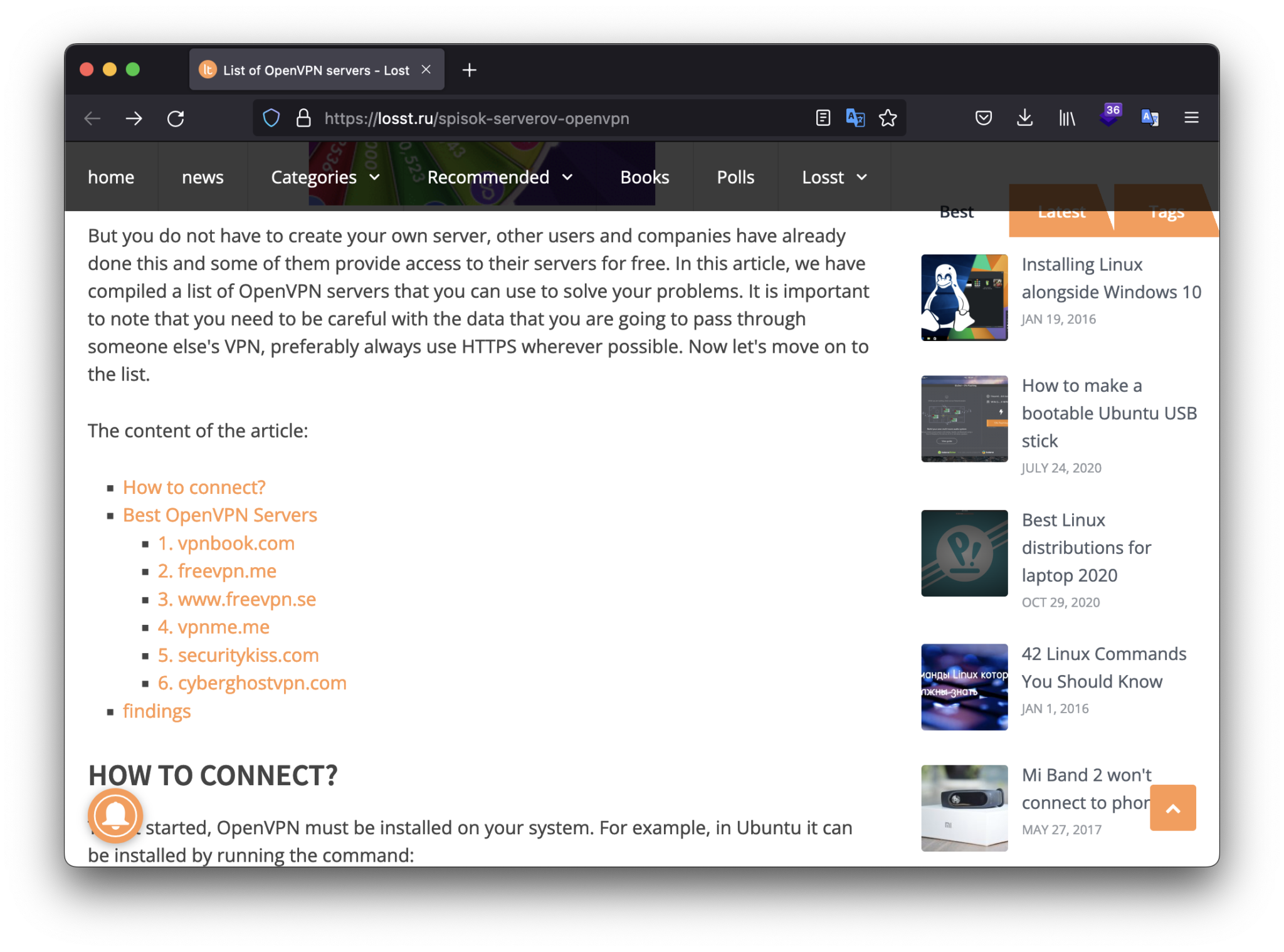
Let’s try to repeat steps from the last paragraph. Follow by the link https://www.vpnbook.com/freevpn we may find the download ovpn link and creds to establish the connection.
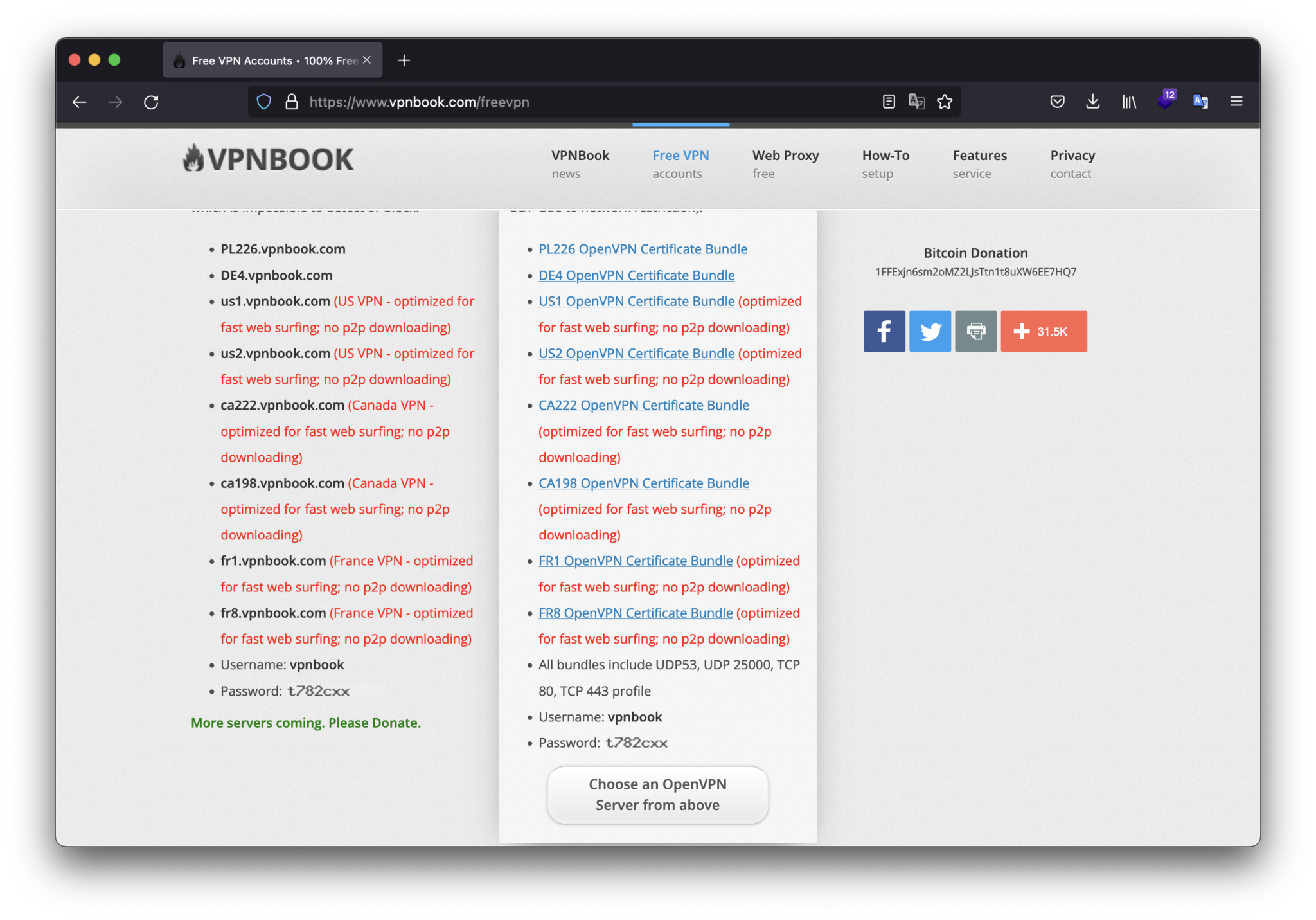
I selected “FR1 OpenVPN Certificate Bundle (optimized for fast web surfing; no p2p downloading)” setting file. To get the ovpn, we have to download the archive and unzip that.
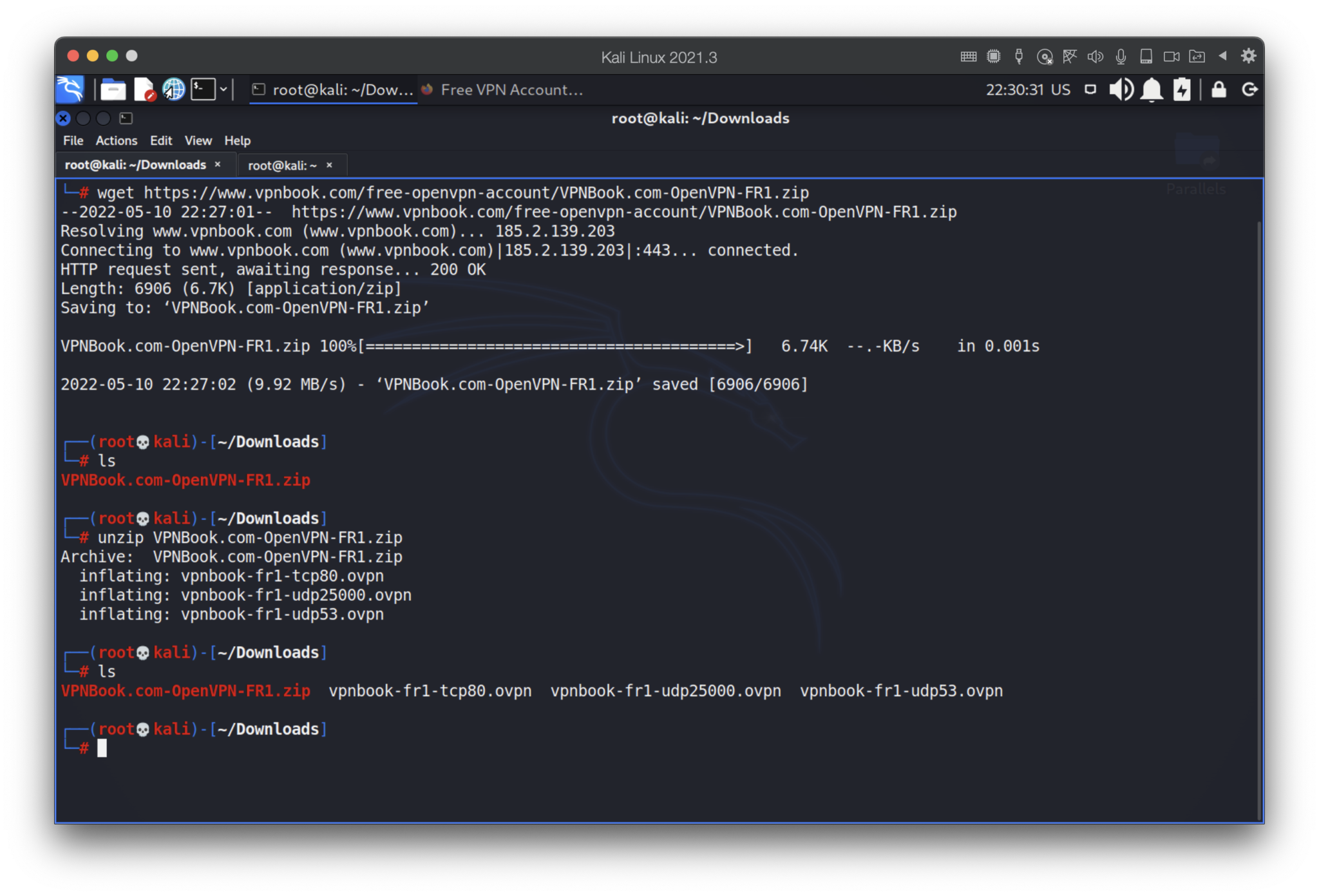
Let’s launch the vpnbook-fr1-udp53.ovpn file by entering its login and password.
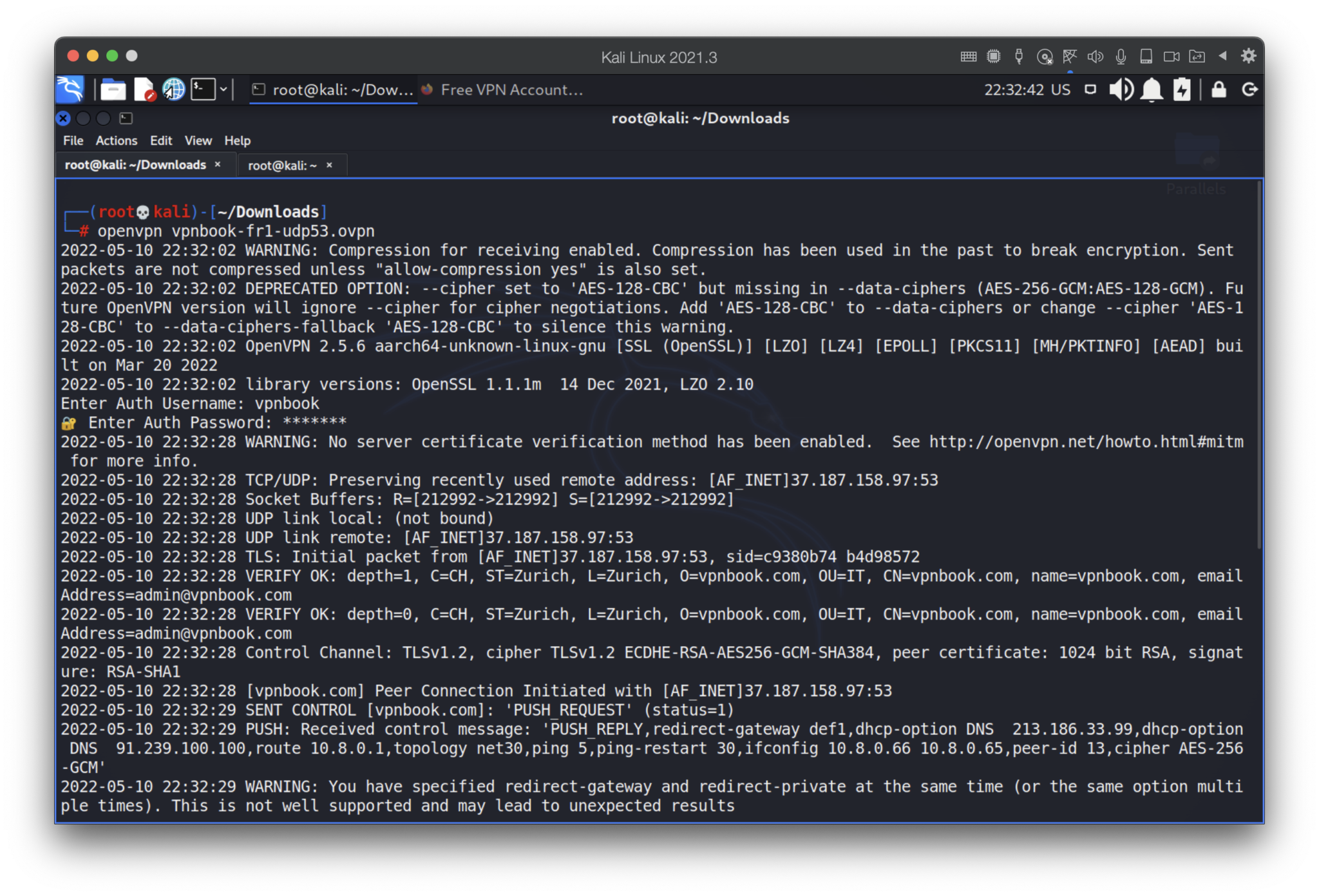
The next step is to find out our network settings provided by DHCP server.
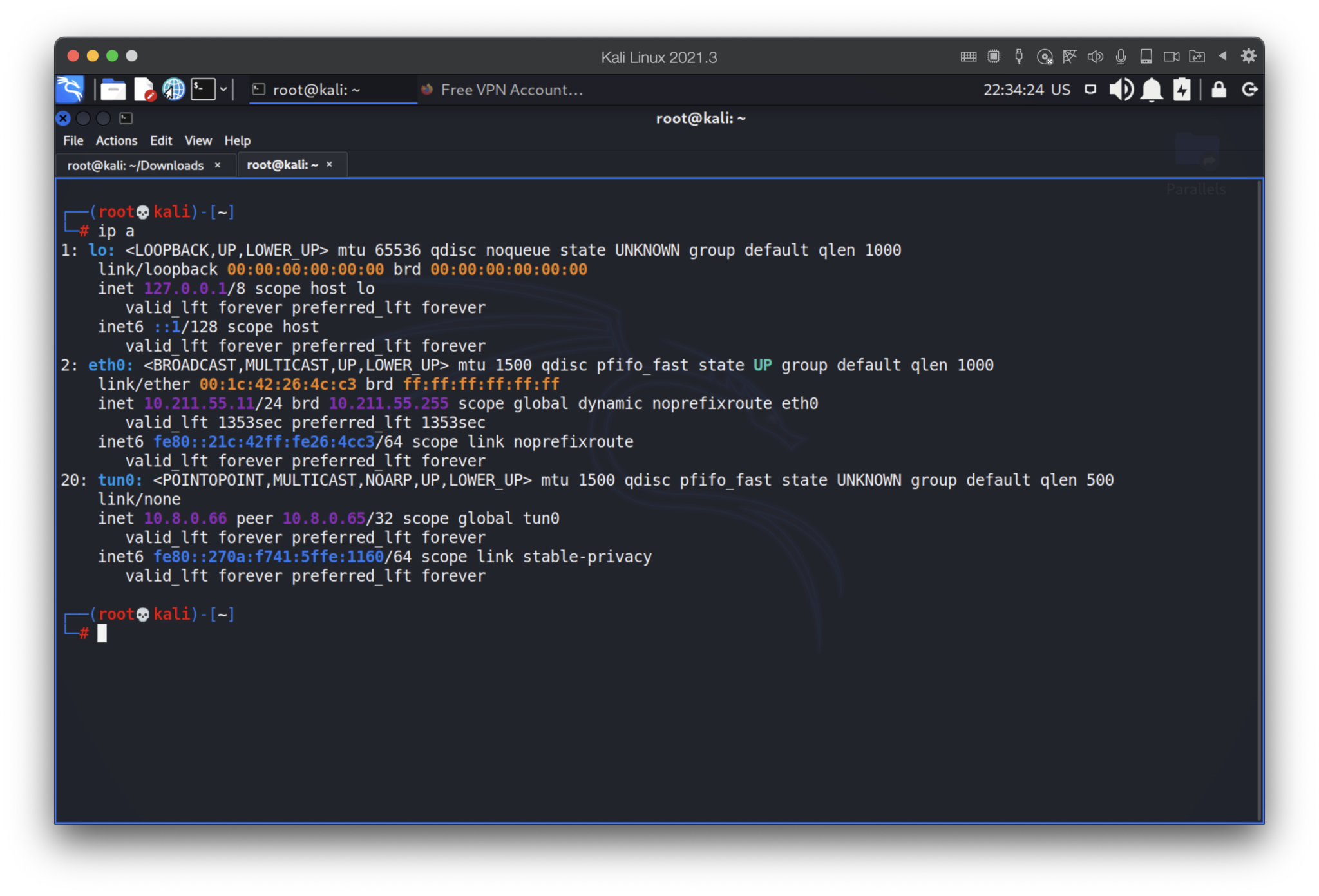
Now we have 10.8.0.66 IP address, but…subnet mask is 32. What does that mean? Generally speaking, /32 means that the network has only a single IPv4 address and all traffic will go directly between the device with that IPv4 address and the default gateway. The device would not be able to communicate with other devices on the network. (c) https://superuser.com/questions/1473252/what-does-it-mean-to-have-a-subnet-mask-32
Ok, the settings are restricted and we won’t be able to reach other hosts. Or can we? The best solution to find this out is just to try to scan the 24 subnet. Let’s do that.
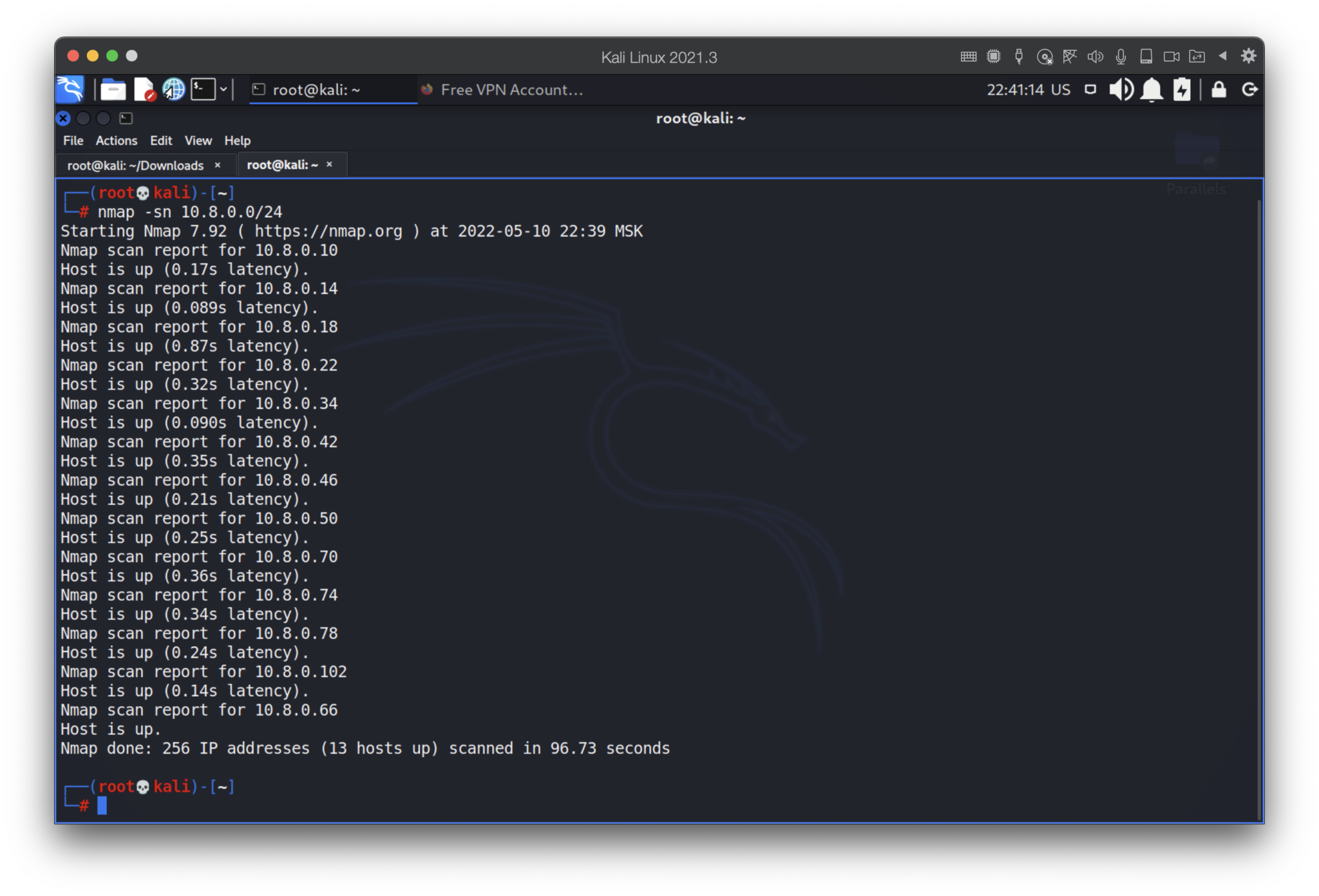
What the heck??? How is that possible? What about the IT theory, restricted settings and other smart stuffs? Never mind, we are hackers and don’t believe in what we see, because one of the technics to hide is to change the titles and banners.
Now, the port scanning…
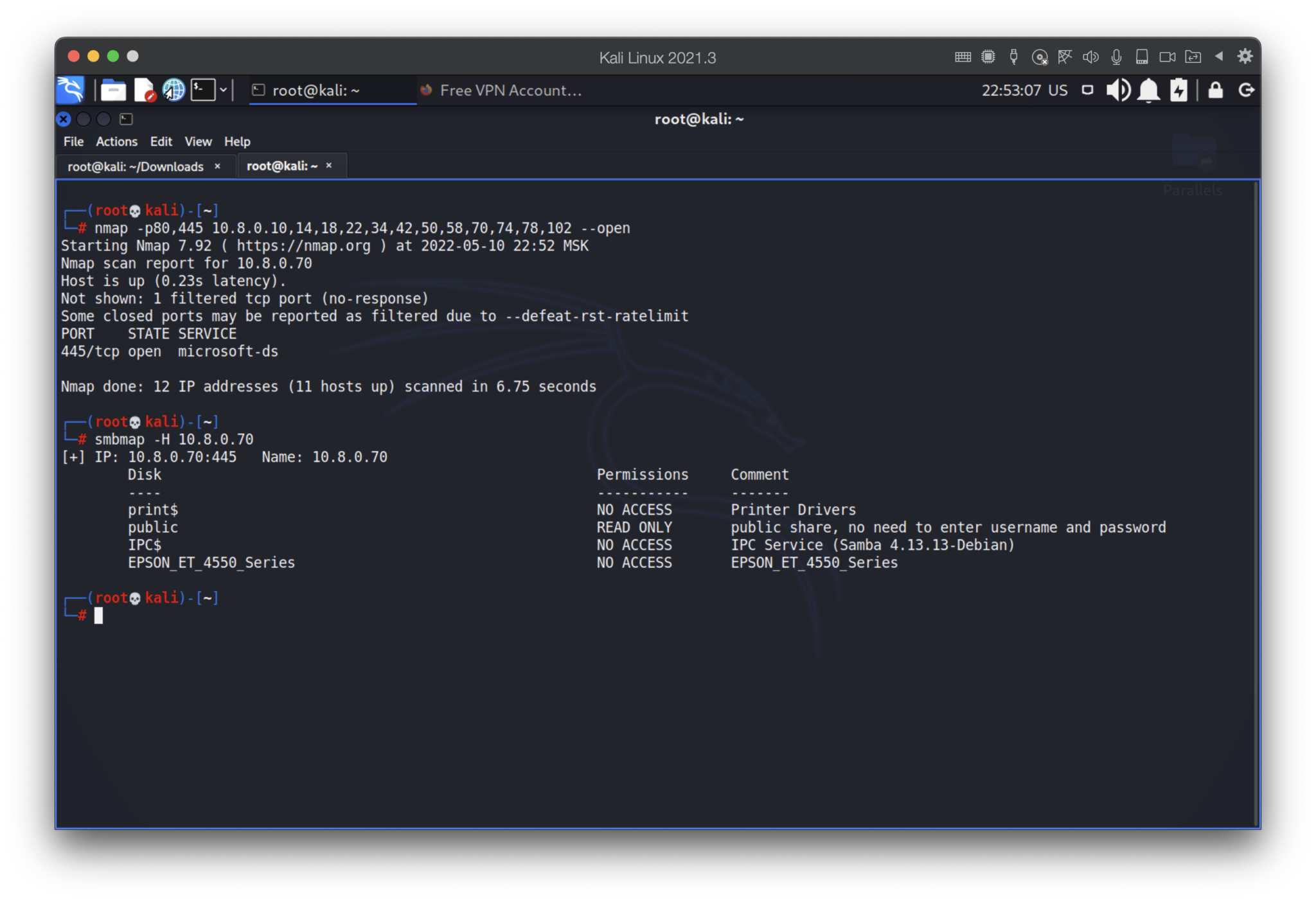
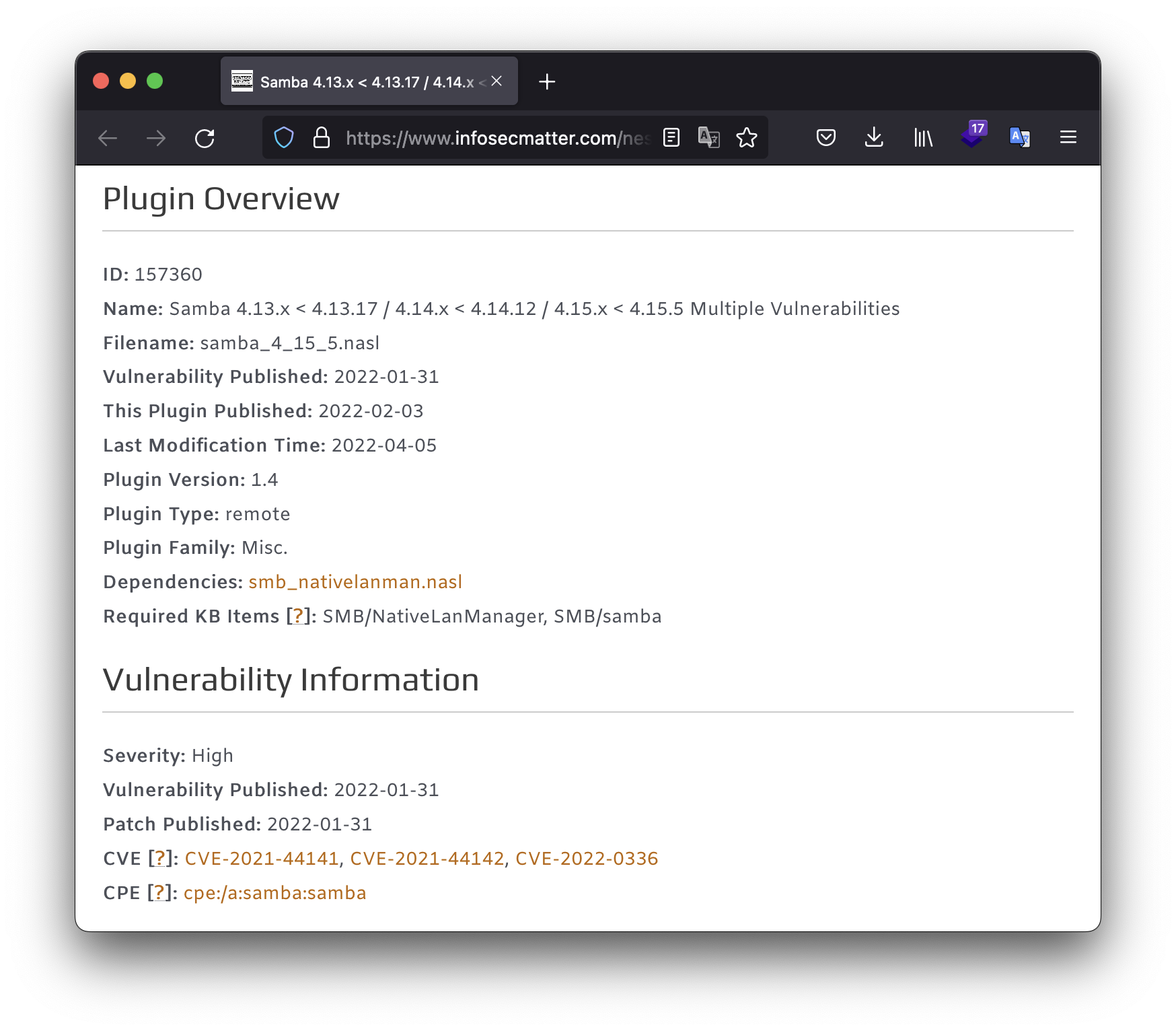
Perfect as always: we found a public share with read only access (no need to enter username and password). Moreover, it has Samba 4.13.13 which has, by the Mitra report, high severity vulnerability, named CVE-2021-44141, CVE-2021-44142 and CVE-2022-0336.
You’ve already knows we are ethical hackers so we won’t go further.
3. Remediation
My main aim is not to shame the particular web-site or their services (sorry, if I offended you), but to notify people and prevent criminal activities against them.
We have considered only 2 most famous free OpenVPN services. But there are many other with at least the same issue: after connection you become the part of the “big family” with a big red banner “Hack me if you can”.
But, if you are brave enough to use free OpenVPN services, here are some advices:
- Use it only from the virtual machine
- As a NIC use shared or host-only network
- Disable shared folders
- Turn off all unnecessary ports
- Disable ping response
- Update your apps and OS
Stay safe!