For cyber security analysts and penetration testers dealing with mobile applications is the day-to-day activity. But if we are talking about Android applications, it’s quite straightforward due to mostly of apps are open sourced and Android OS can be simply implementing onto your virtual environment. But with iOS it’s completely opposite situation and researchers have to install cracked OS like Jailbreak on their old iPhones/iPads. Today we will try to fix that problem out and find an easiest way to analyze apps for iOS.
0. Preparation
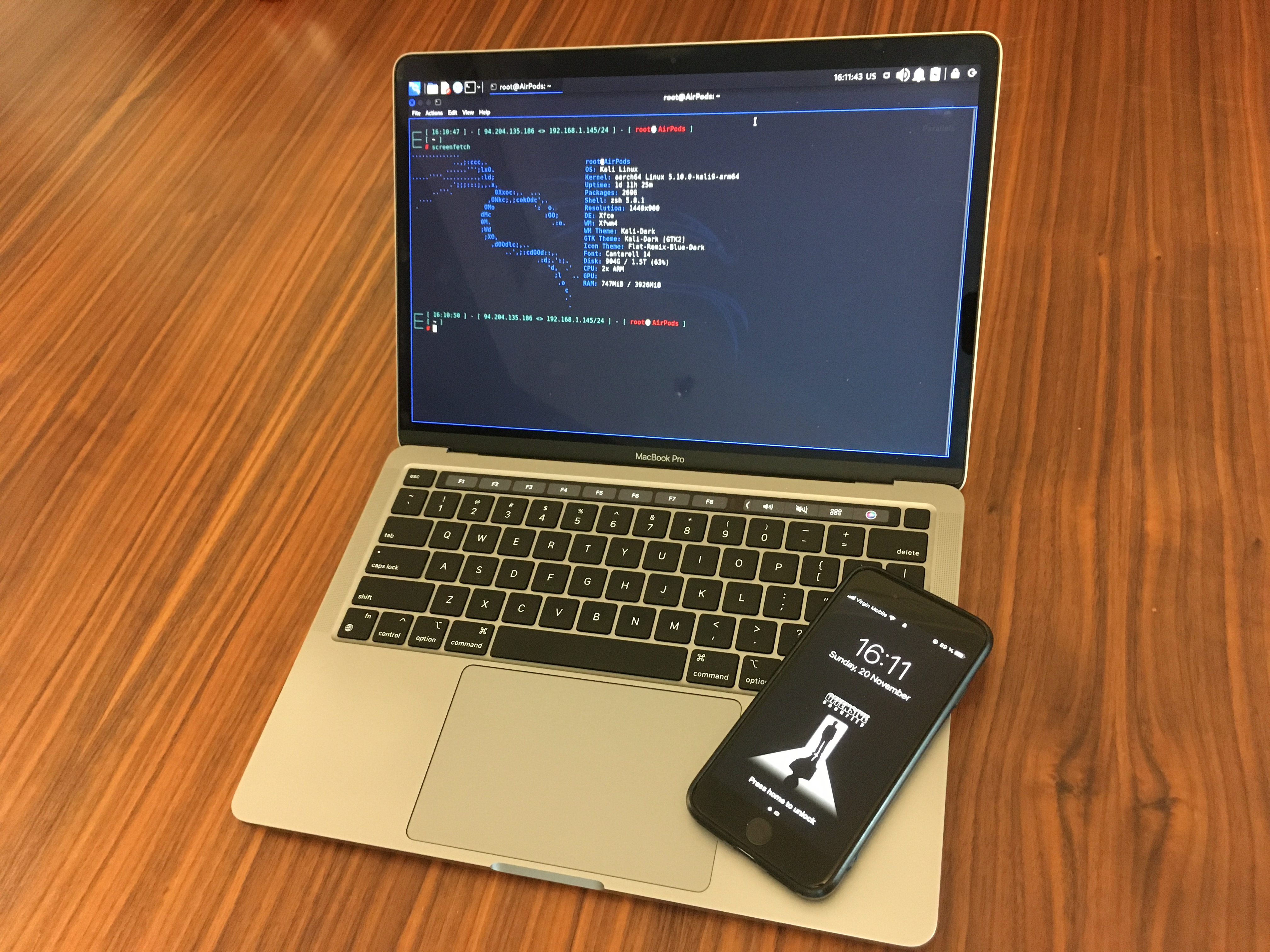
Let’s first discuss about the equipment. During my research I will use the next ones:
- MacBook Pro (you are free to use any other PC)
- Parallels (or other Virtualization system, for instance VirtualBox or VMWare)
- Kali Linux 2021.3 (yeah, I’m the oldfag 😉
- BurpSuite Community version (it’s the free one)
- iPhone SE 2 Generation (or another fully update iPhone)
Ok, we got everything we need and now it’s time to configure that properly. The main idea is to make the traffic from iPhone goes through our Kali Linux where we can intercept/sniff it for our further purposes. But even when we can do that, the encrypted packets are another issue. That’s why BurpSuite is our lifesaver, but, first things first.
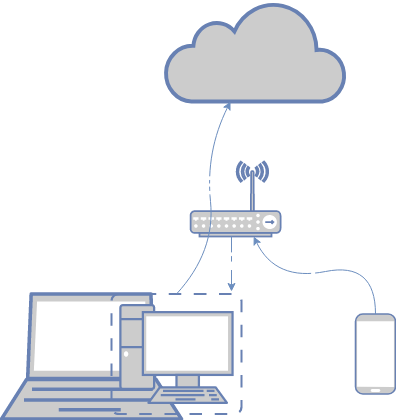
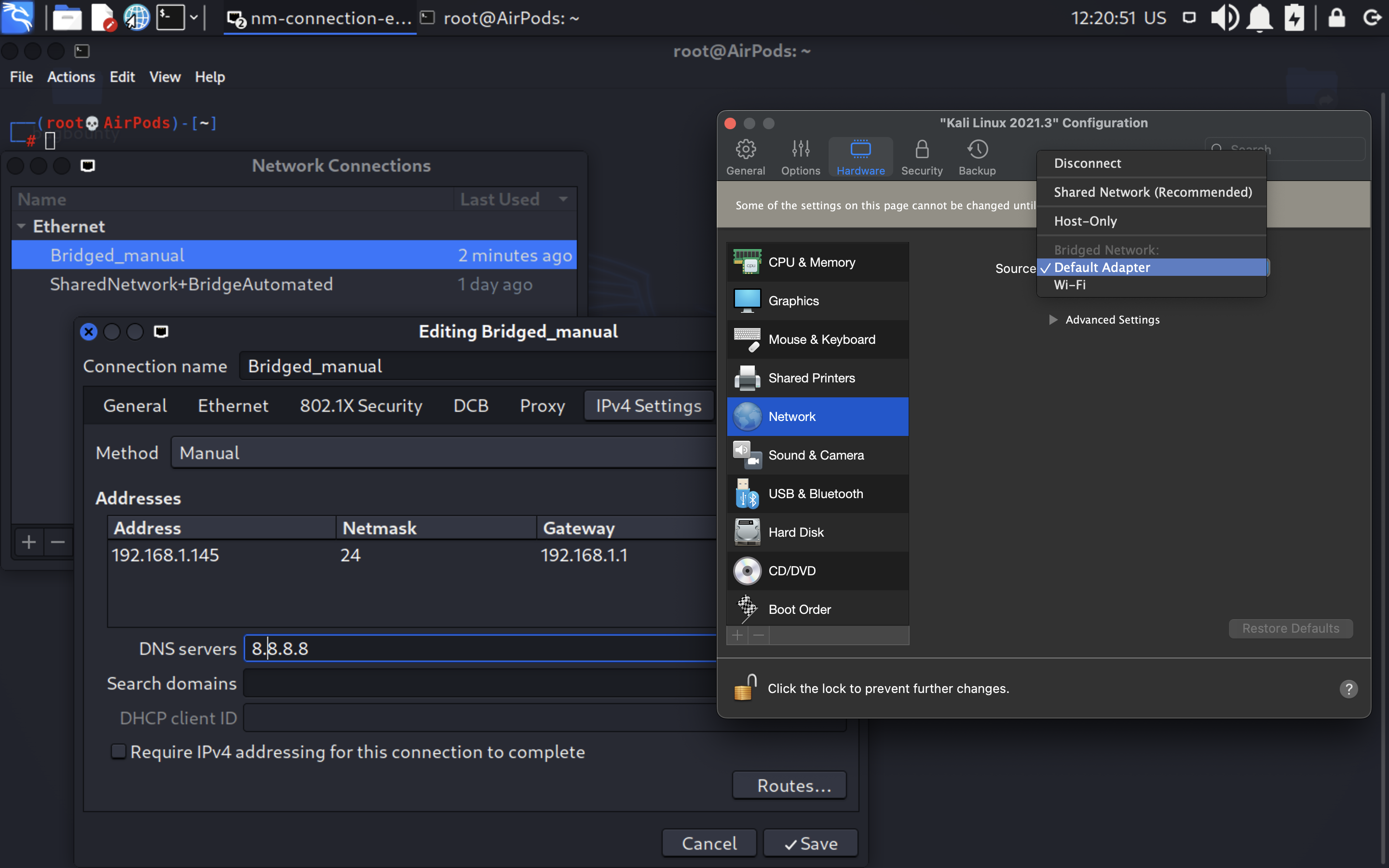
To make the route possible, first, we need to make our Kali Linux virtual machine as a dedicated host so we can interact with it from any device within the network / Wi-Fi subnet.
To do that, let’s set the NIC (network interface card) as a Bridge. In most cases your router’s DHCP service will provide all the configurations, but in my case it hasn’t worked. So, I created another network profile in Kali machine and fulfilled settings manually. By the way, that’s even better because we won’t struggle if IP changes.
Once the settings are configured, let’s check and assure it’s working.
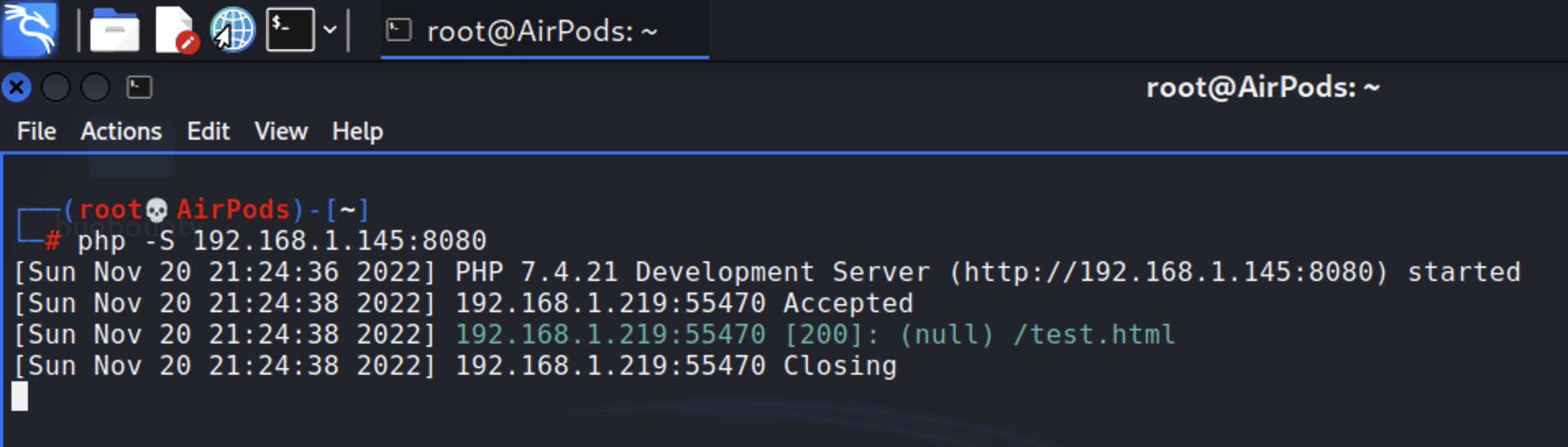

Good, we could connect directly from the phone to our virtual machine. Now it’s time to make some magic and push all the mobile’s traffic through that as well. To reach our aims we are going to use Proxy.
Let’s launch the BurpSuite. By default, BurpSuite’s proxy is configured only for localhost (127.0.0.1).
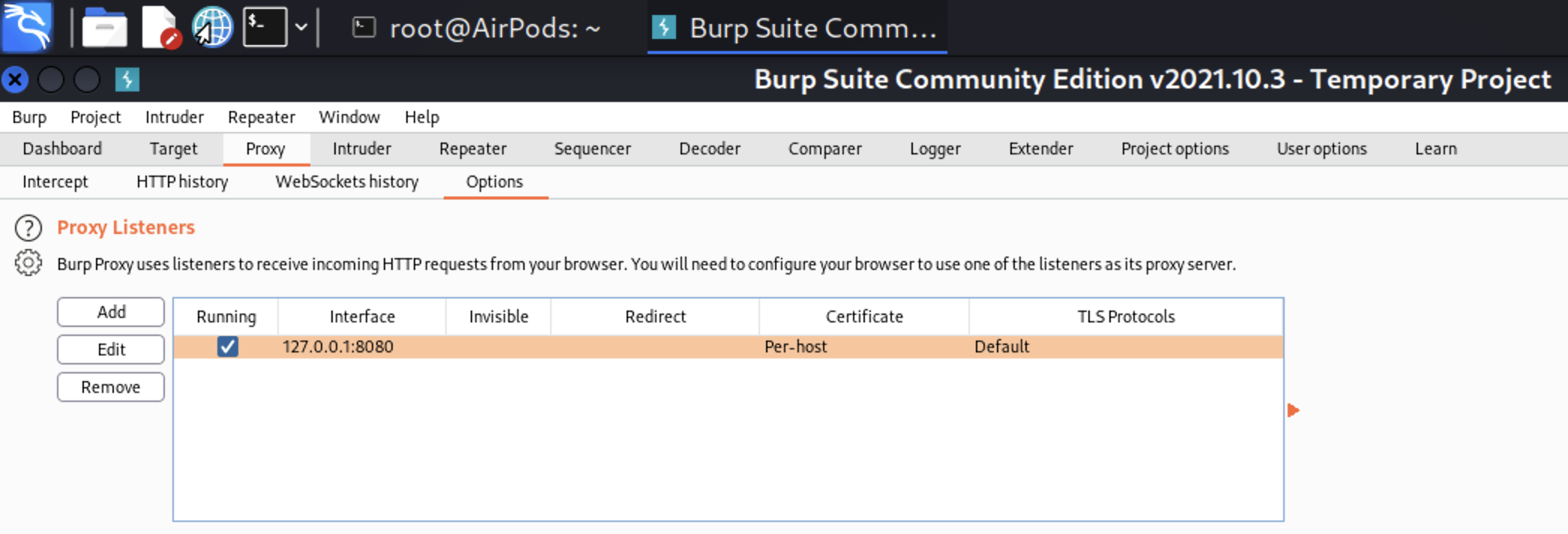
To make it reachable outside the machine, we have to change “Bind to address” options. To make that, go to “Proxy” > “Options” > “Proxy Listeners”, select the Interface and press “Edit” button. In the pop-up window select “All interfaces” and press “Ok”.

If you’ve done everything correctly, your interface should be changed to “*.8080”.
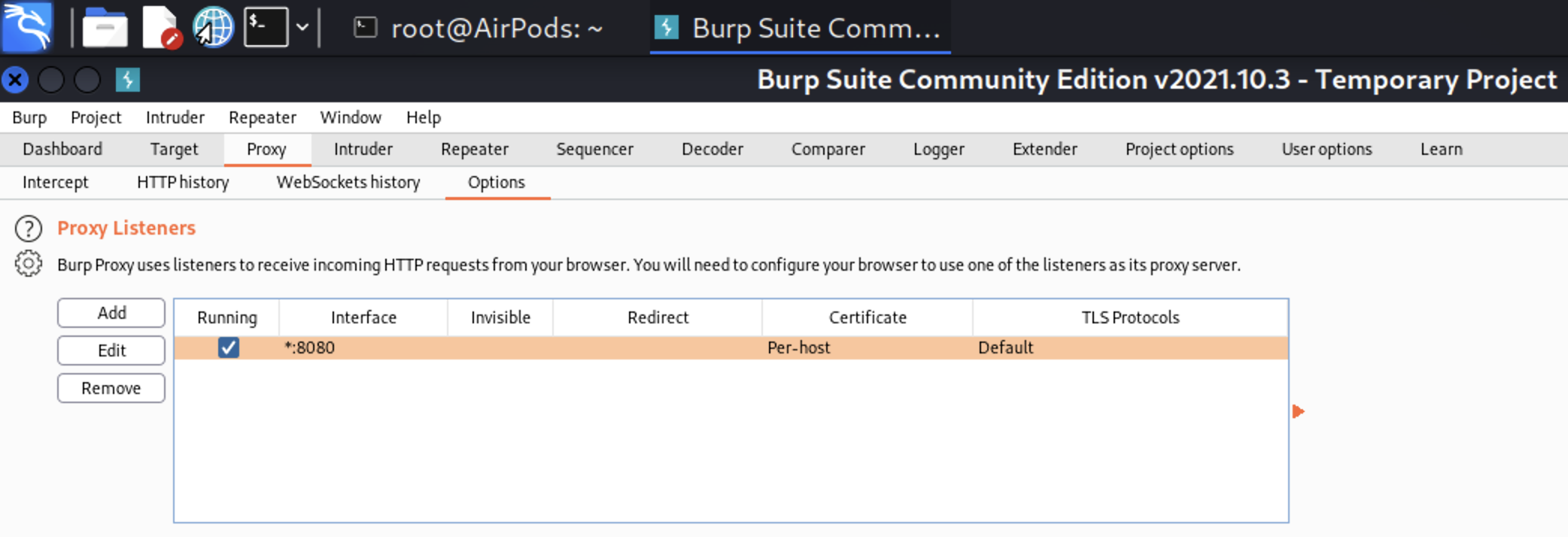
Nice. The next step is to install Burp certificate into the iPhone.
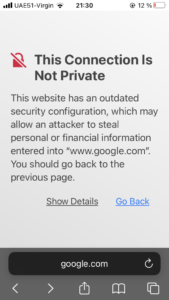
Why do we need that? First, almost 90% of the traffic is encrypted hence instead of cleartext we will see only the God knows what in our intercepted output. Second, some applications won’t work at all because of an untrusted certificate. Instead of a web-site the browser will show us something like that:
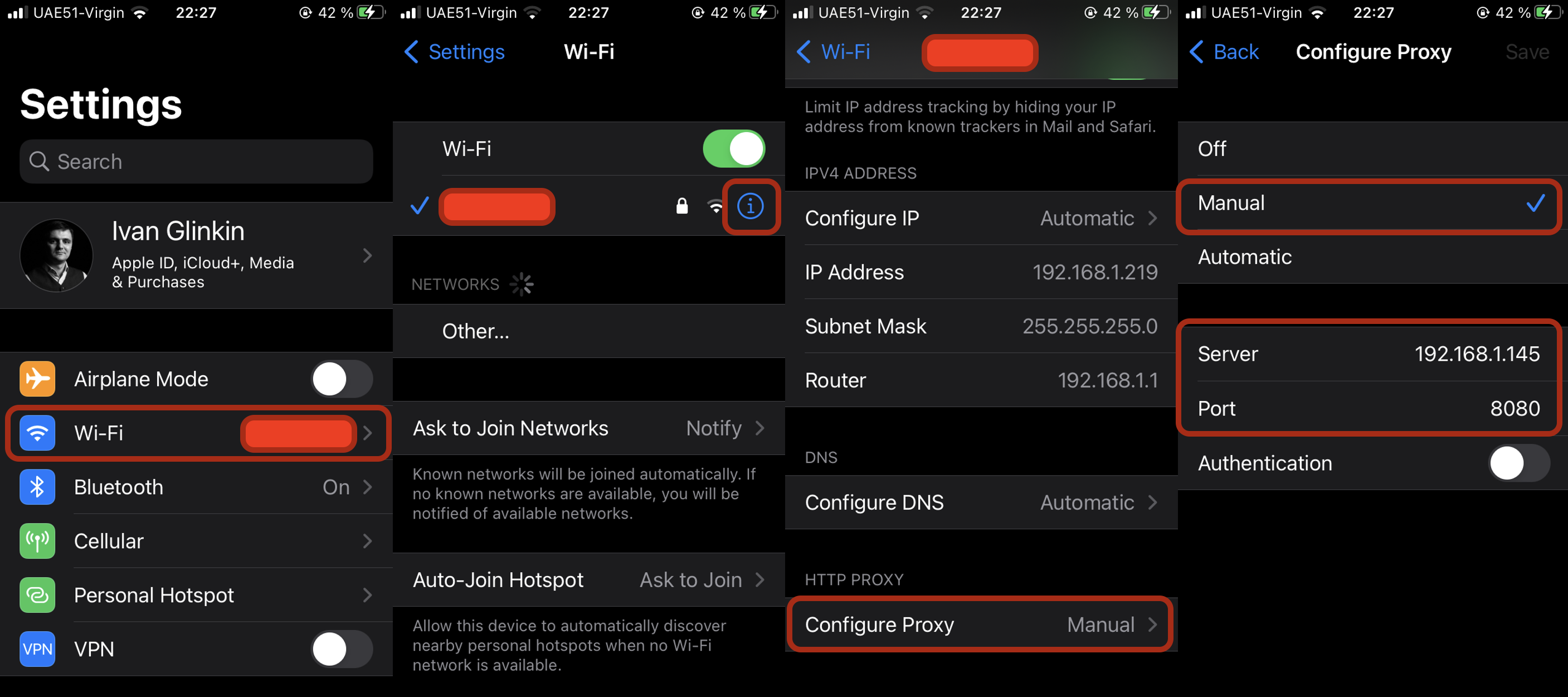
To install Burp certificate on your iPhone first you need to configure the proxy. Go to “Settings” and press the “Wi-Fi” item; then press the “Info” icon and scroll down till you reach the “Configure Proxy”. There, insert your Kali Linux IP-address and BurpSuite port; in our case it’s 192.168.1.145 and 8080 respectively.
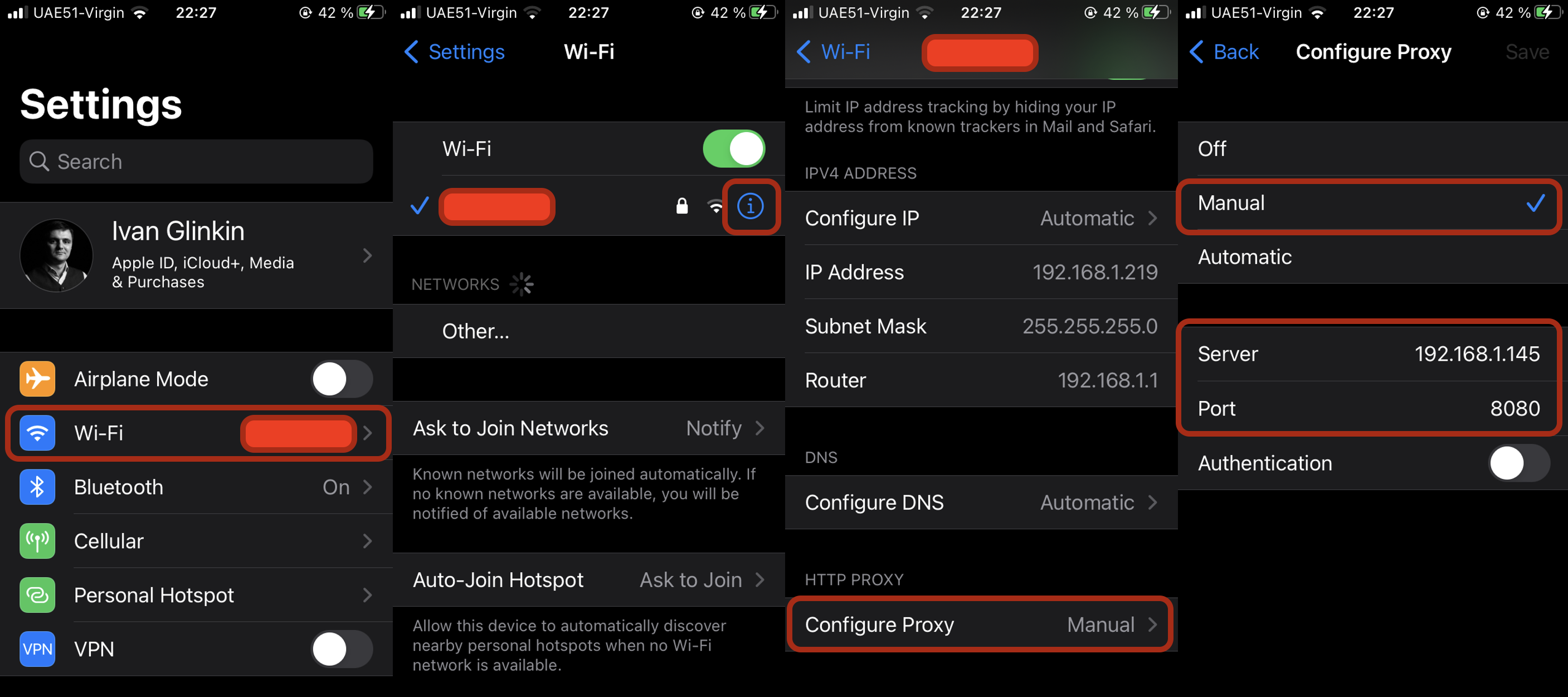
If you’ve done everything correctly, when you visit the http://burpsuite/ web-site, you will be able to download the certificate.
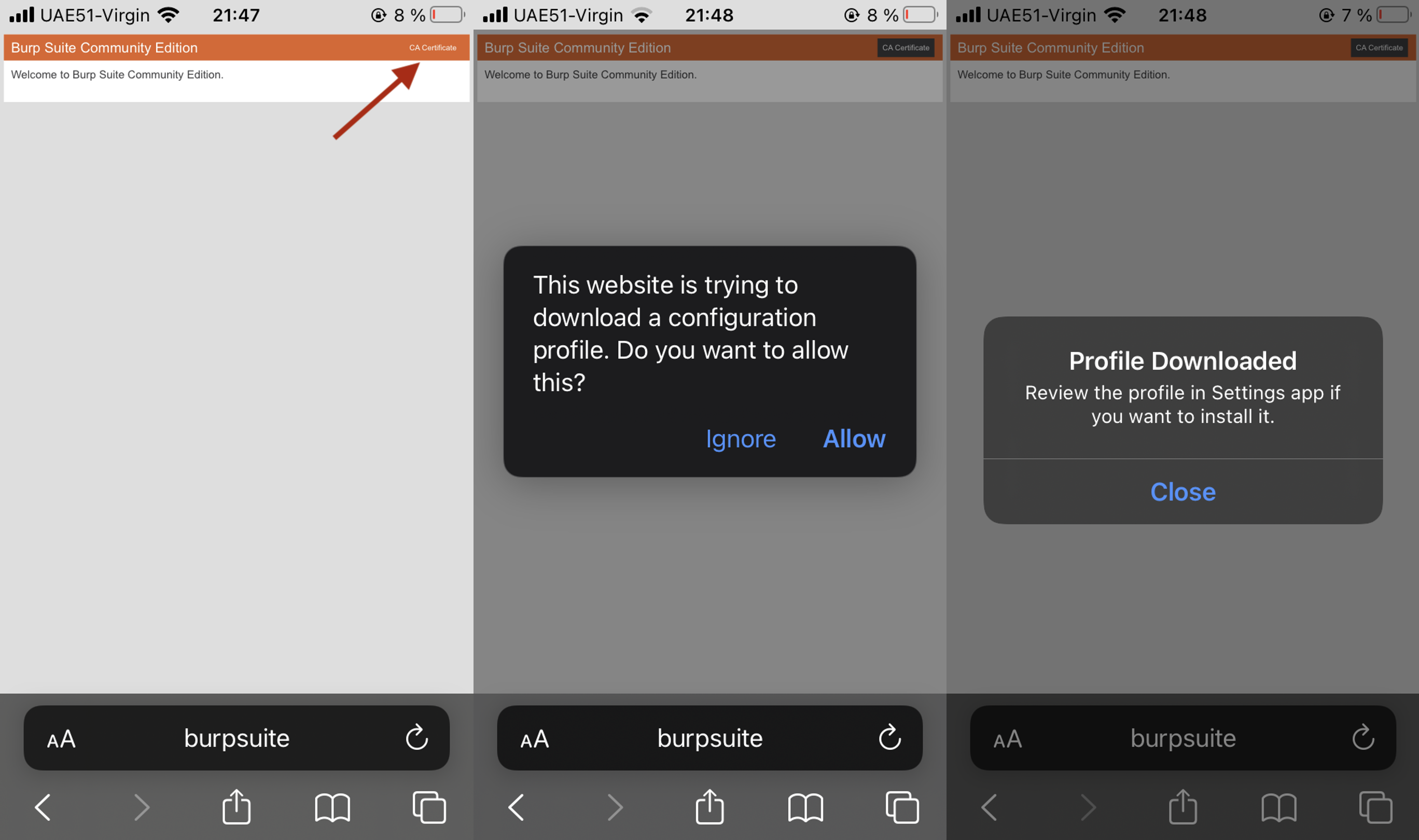
Do you think that’s all? C’mon, it’s iPhone: to set something up you have to have plenty of approvals 😉
Now, having downloaded the certificate (or Configuration profile), we have to implement it into the phone. Go to “Settings” where you can find a new appeared item “Profile Downloaded”. Follow the link press “Install” – you’ll have to enter your passcode.
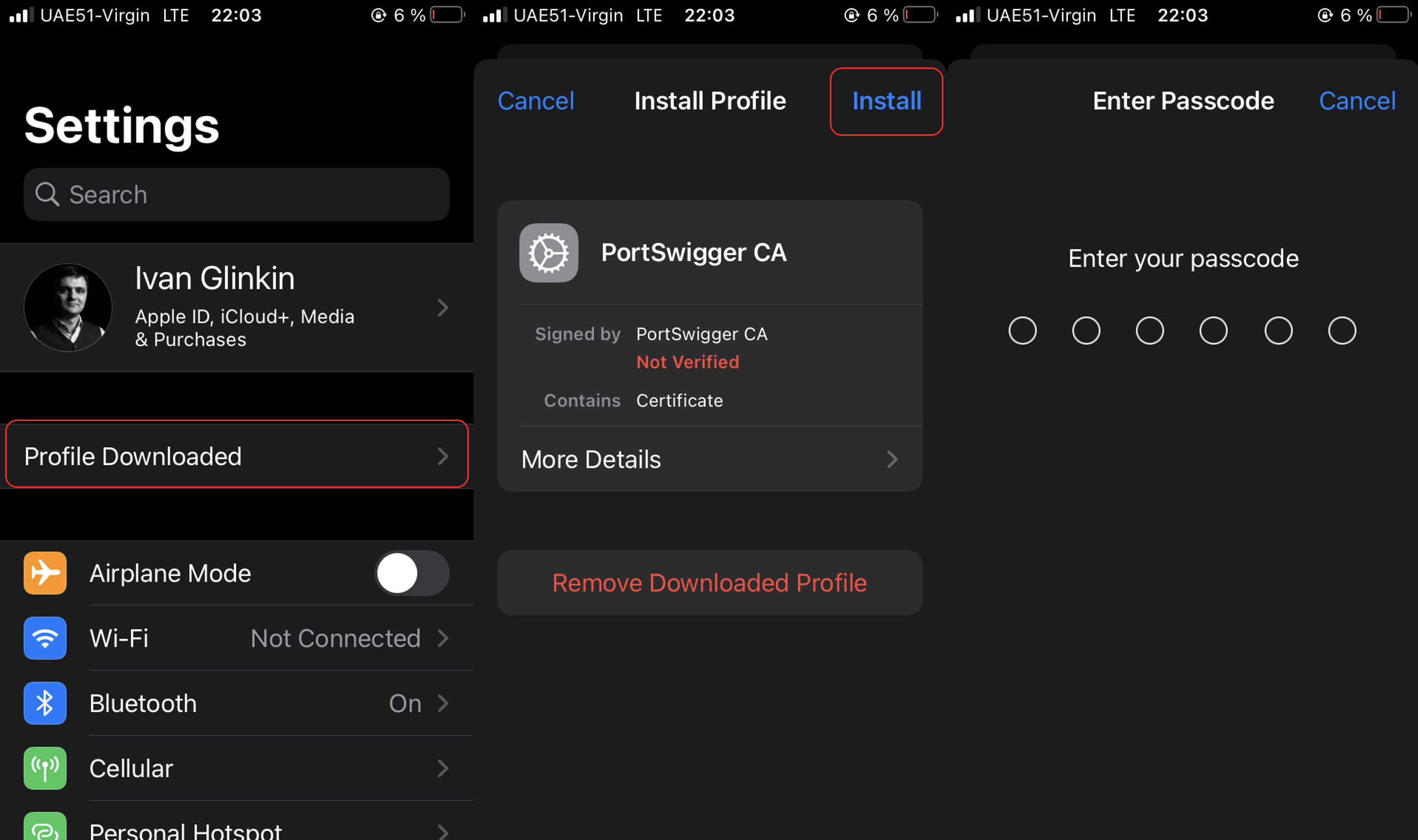
Then, as we are used to do – “Next, next, next” or “Install, Install, Done” in our case.
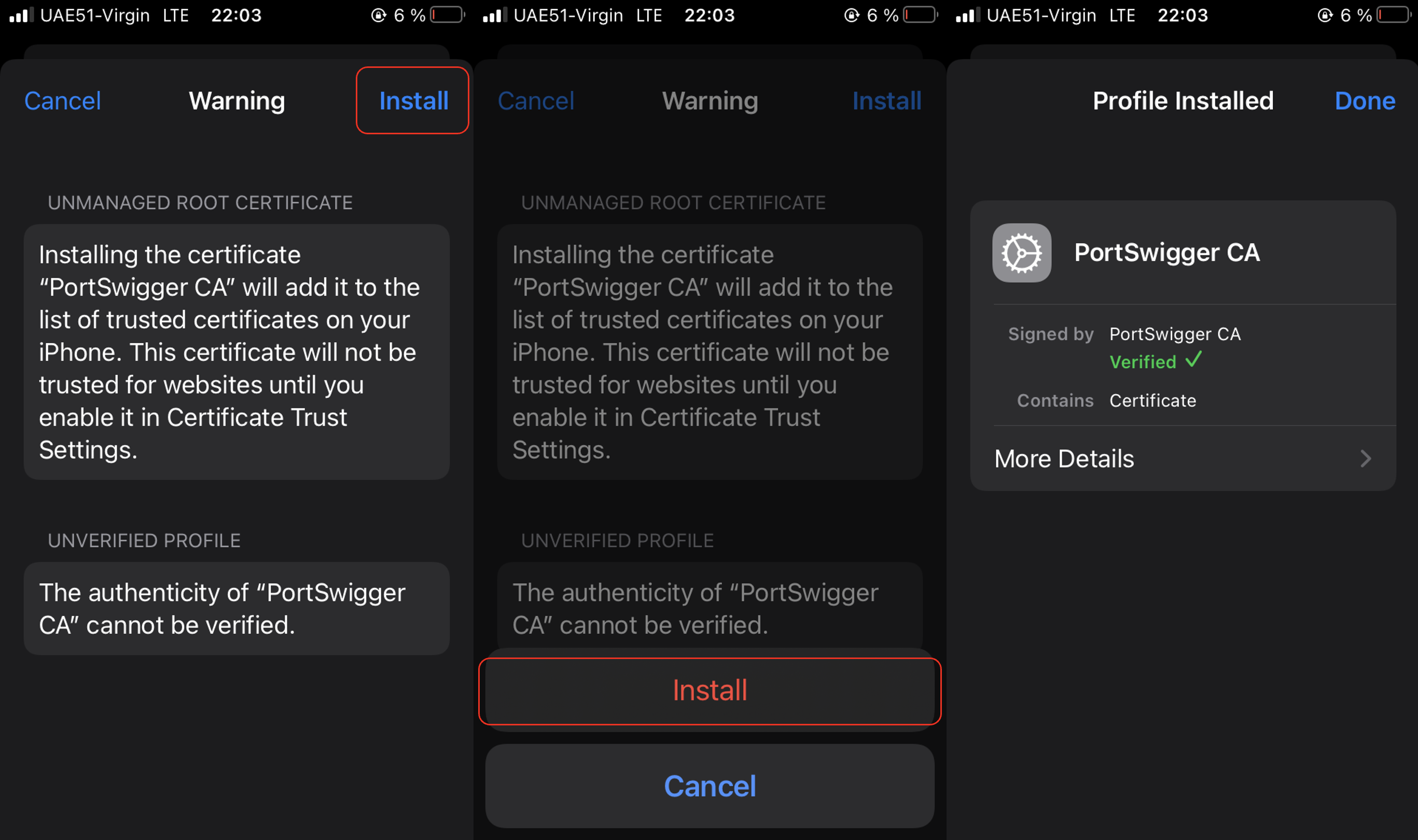
Now do you think that’s all? Not a close 😉 On the device, go to “Settings” – “General” – “About” – “Certificate Trust Settings” which is at the bottom of the page. The installed PortSwigger (BurpSuite) Root Certificate will be displayed in a section entitled “Enable Full Trust for Root Certificates.” There is a slide button next to it. Tap the slide button next to the certificate and confirm as “Continue”.
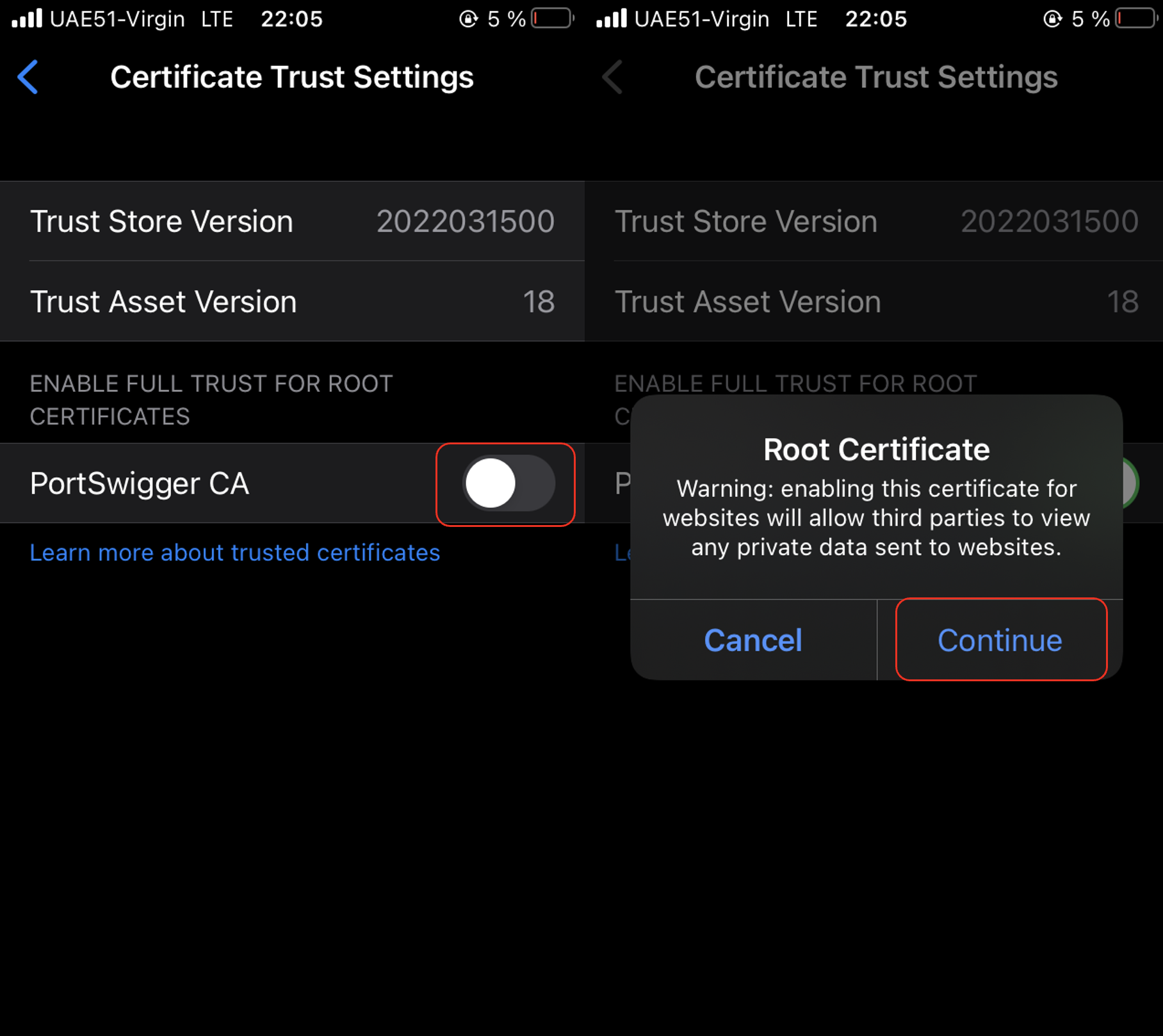
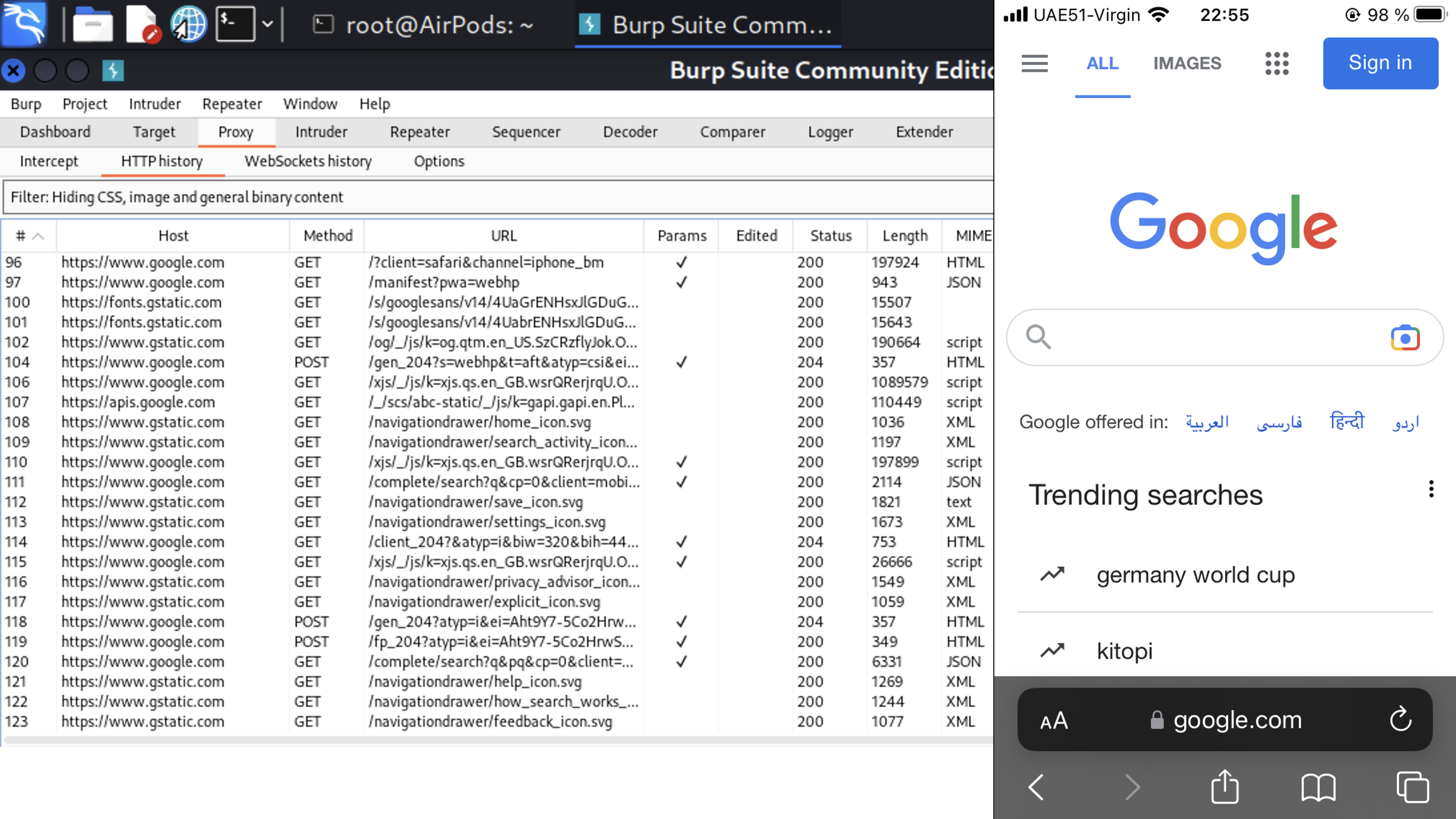
The third time, do you think that’s all? … Yes, that was the last step 🙂 Let’s check if it’s working as intended. Let’s visit the Google site from the iPhone and check our BurpSuite.
- Research – McDonalds
Just to be clear – we are not going to perform any VAPT or other activities, which may reveal vulnerabilities and/or misconfigurations in apps. The main aim for today is to give you a high-level understanding how most of the iOS apps work. If we are clear, let’s go.
I would like to start from McDonalds application. I guess, everyone has it within your phone 🙂 Let’s launch the app and see traffic.
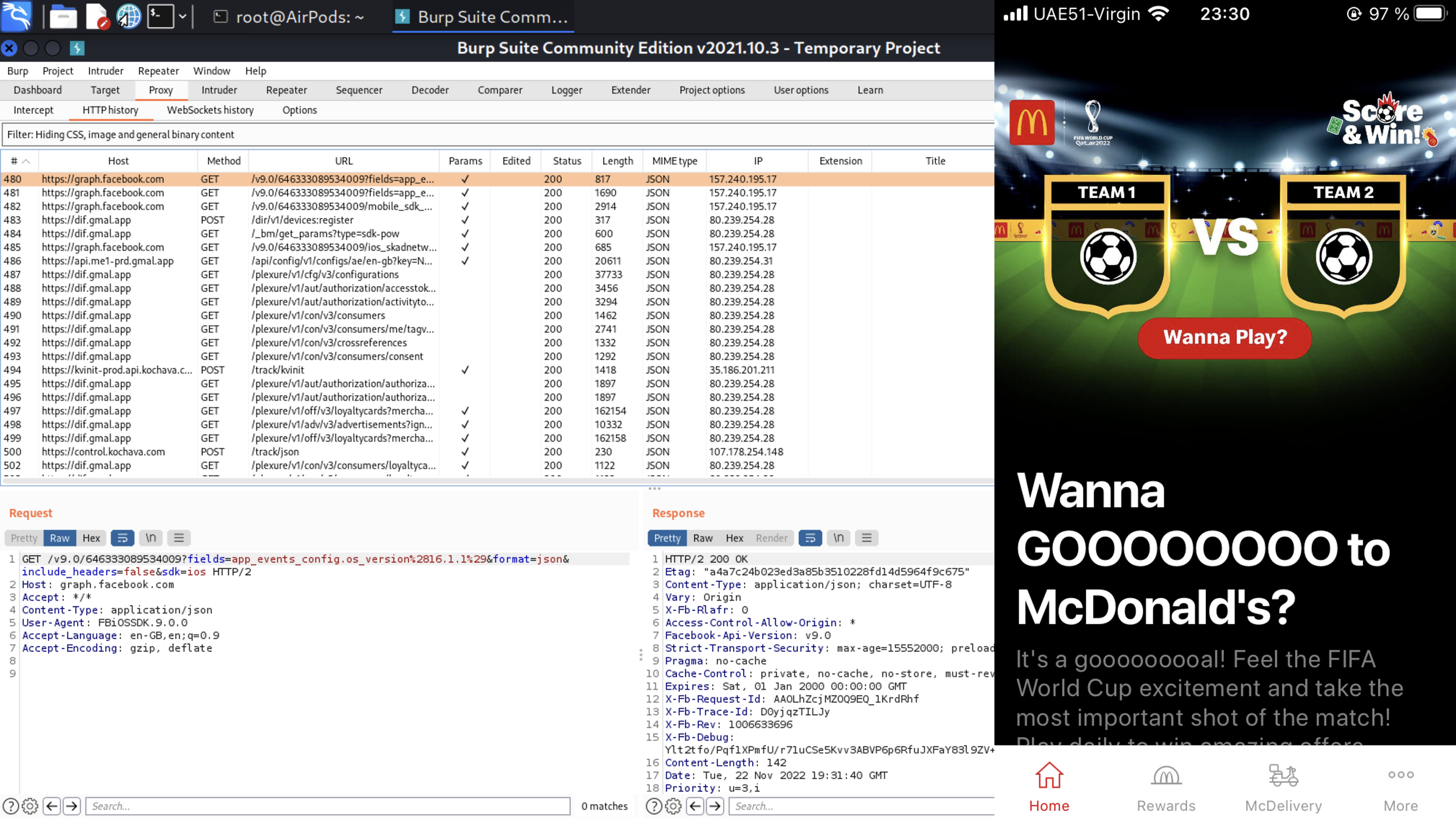
You know, that is a little bit odd, because the first site the McDonalds application is requesting instead of their own web-site is … Facebook. Hm. What else? As you can see the app is requesting control.kochava.com web-site and transfer plenty of information about our device.
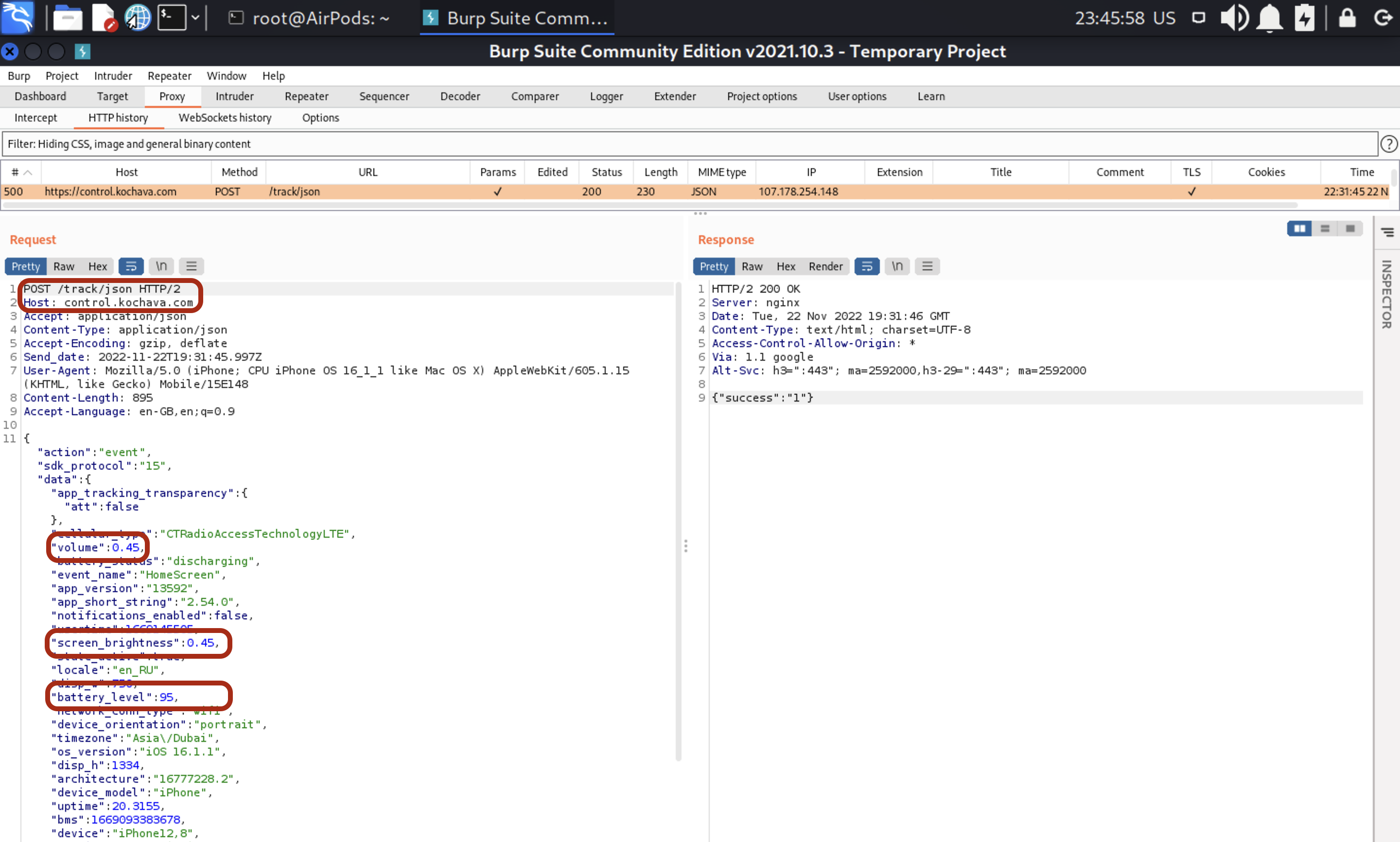
Ok, I can understand why they are using my display height and width, mobile device and its version and other related stuff. Yeah, it’s all about user interface and how to better fit with customer’s needs. But why on earth they need my volume, battery level and screen brightness? Actually, I don’t know the proper answer for this particular question.
By the way, who is kochava? Let’s just follow the link and make a little research.
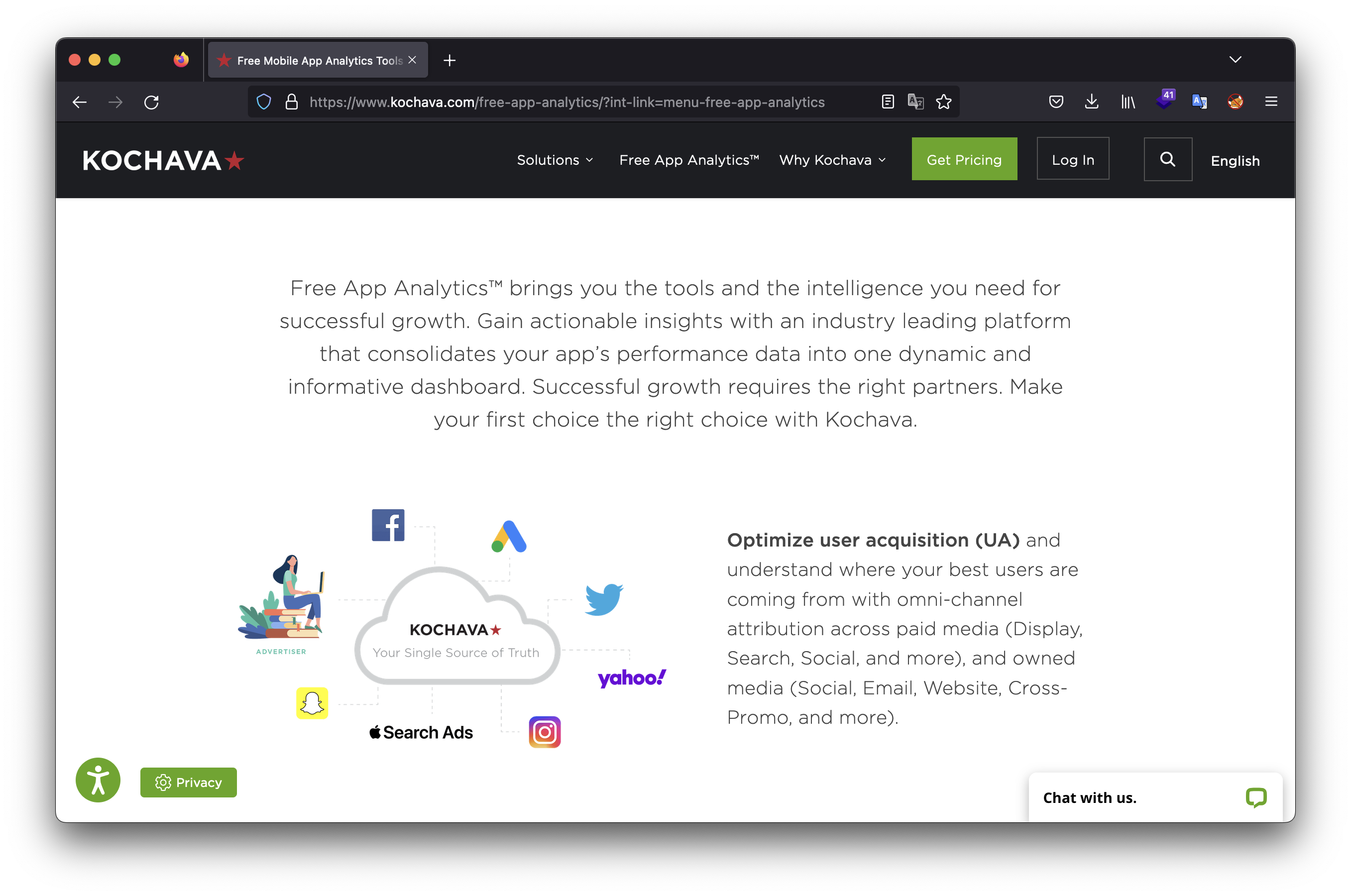
Understood. Thank you, McDonalds, now I know where my data is going to.
To be honest, nothing more interesting from that app. Frankly speaking, it’s just a web-browser, which even has its own user-agent – GMALi/2.54.0.13592, hence, the communication is by HTTPS protocol. So, if you have OWASP knowledge and web application PT skills, analyzing McDonalds application is not something unusual.
- Research – Skype
What is the next one? Let’s talk about Skype. Based on my iPhone settings I always keep all of my applications up to day. So, the testing version is 8.90.0.407.
Having opened the app, let’s look at the BurpSuite. Wow, I guess we have another web-browser 😉
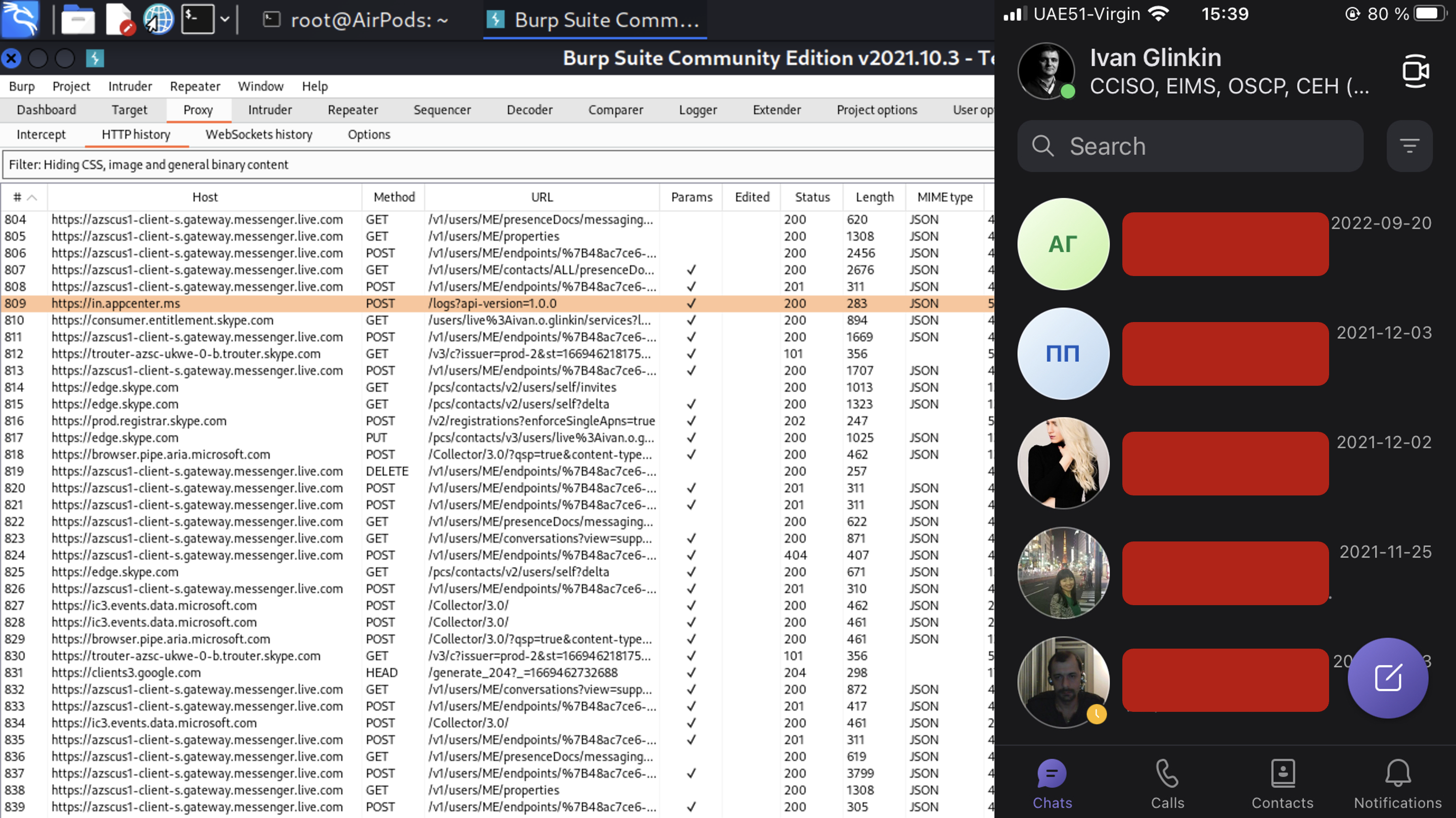
And of course, who doesn’t like my data? 🙂
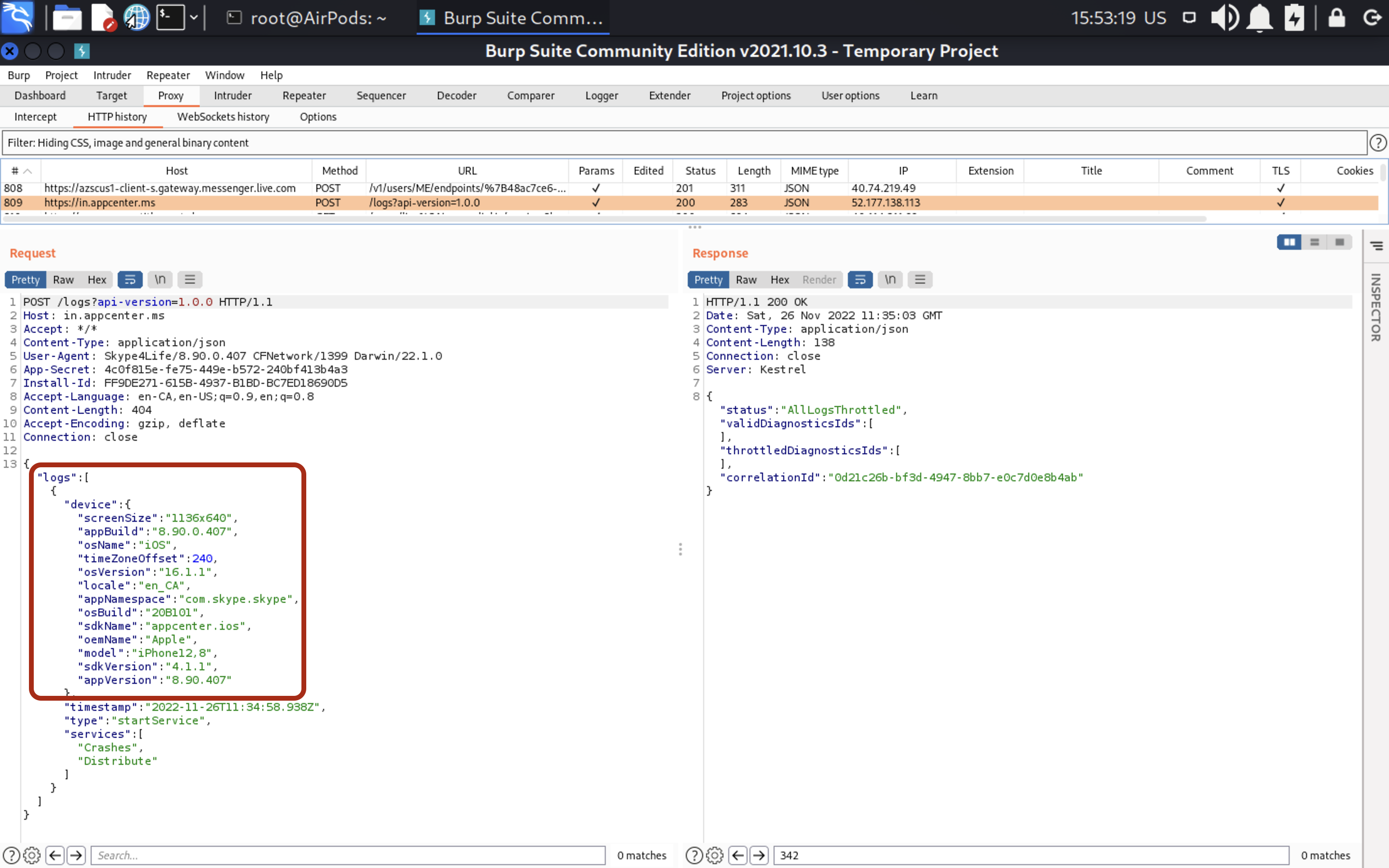
To find out who are using Skype as well, the last one has access to my contacts. Then, Skype is requesting server edge.skype.com to find the matches. BUT!!! Skype is encoding/hashing phone numbers before requesting 🙂 So, even if someone is performing MITM attack against you, the criminal won’t know your contacts. Good one, Microsoft 🙂
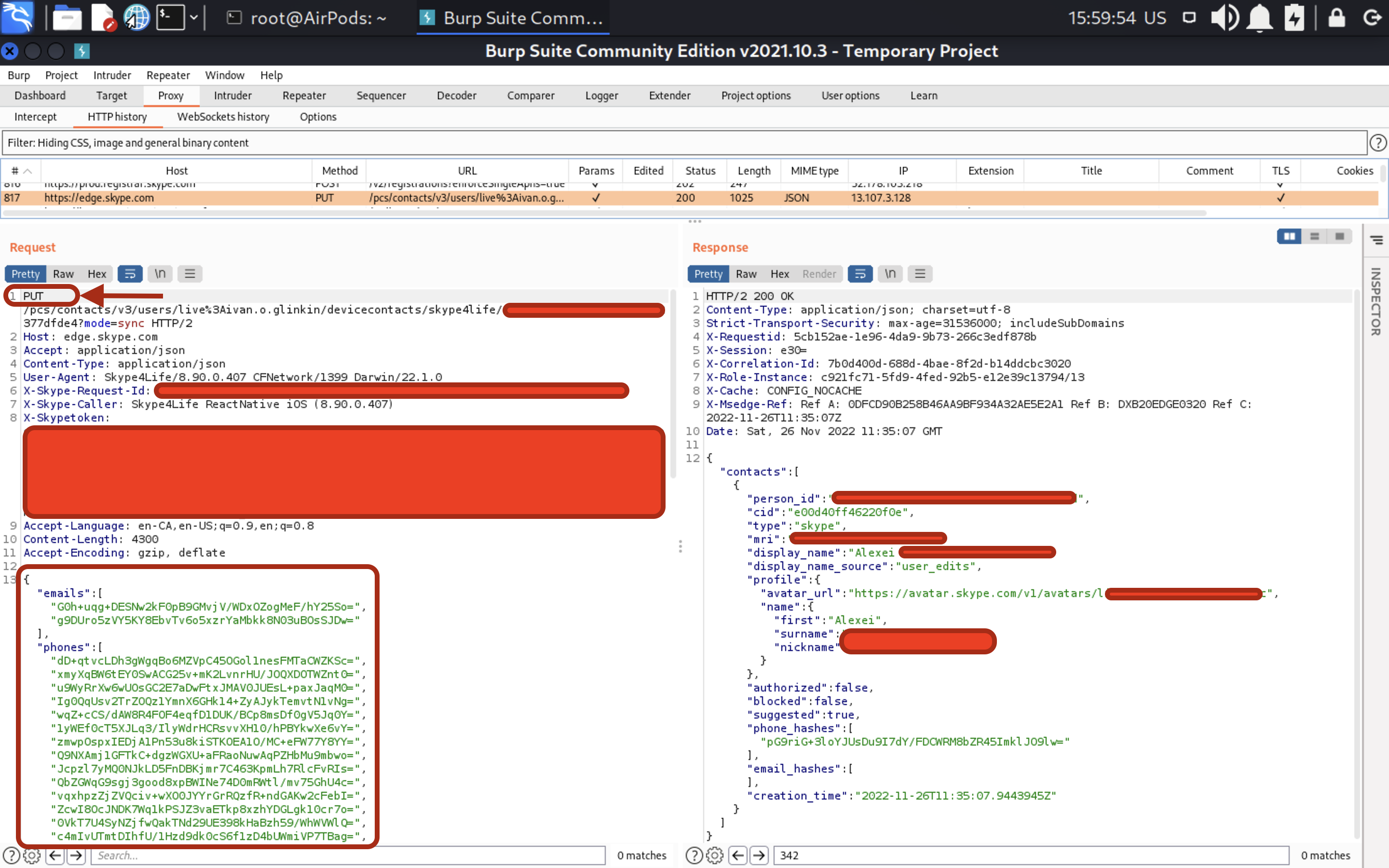
But what about encoding messages? Are communications safe enough? Can we trust Skype and be sure about the privacy? Let’s check.
I’ll write a message to my colleague – Denis Karzakov, via the Skype app. The message is: “Hello Denis. Testing Skype messages encoding”.
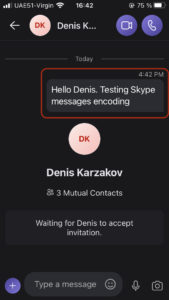
Now, let’s check the BurpSuite.
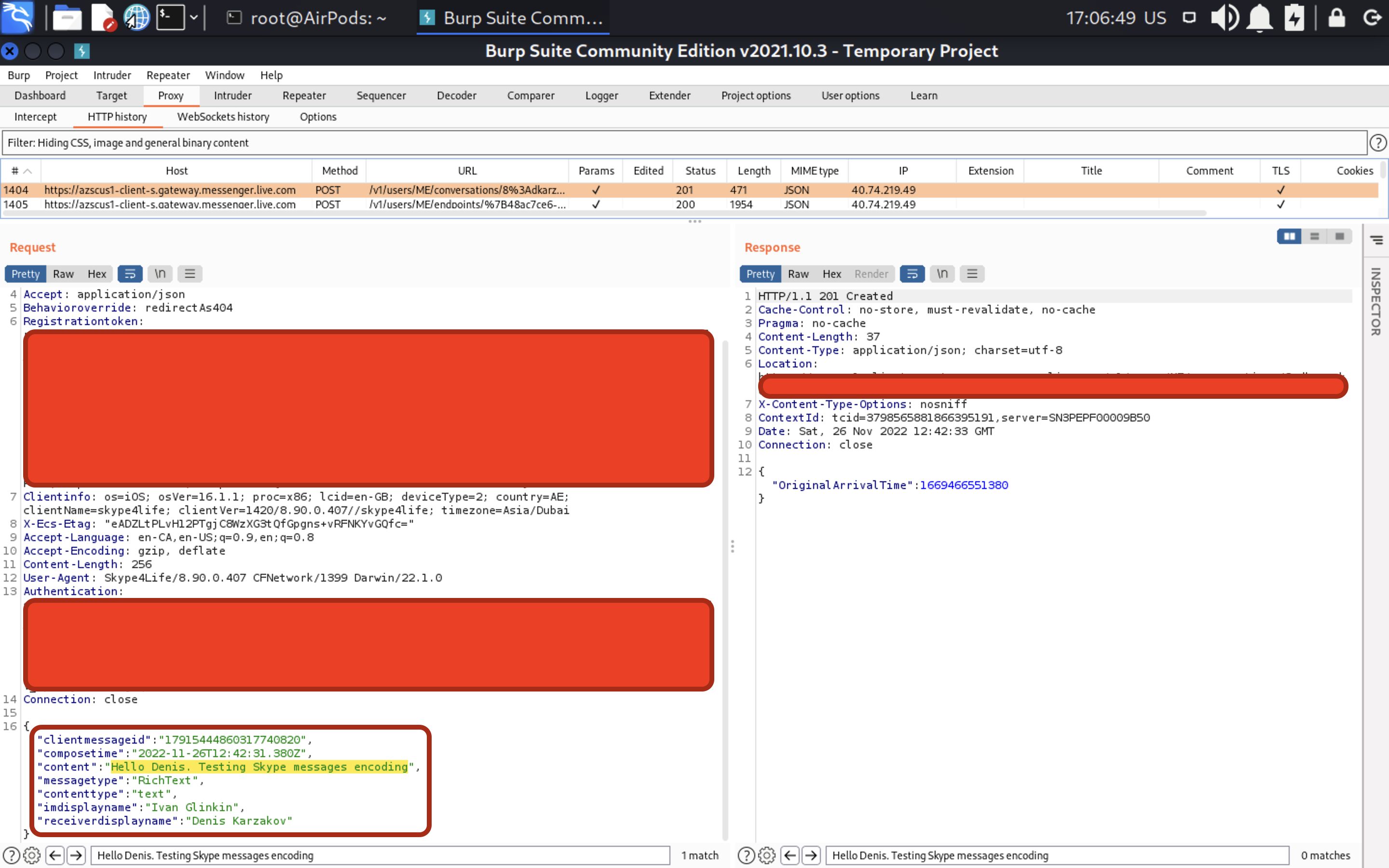
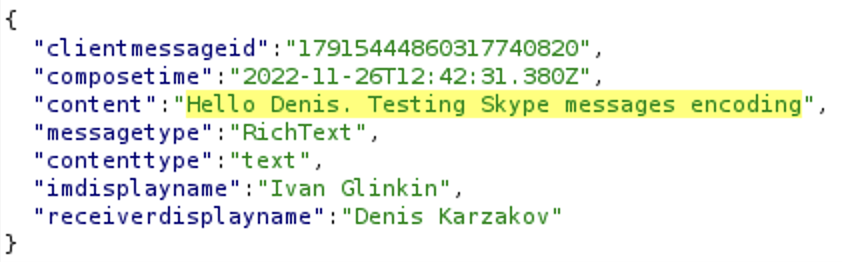
What the heck? Seems like Skype does not use end-to-end encryption yet. I won’t comment any further. Cyber security professionals have already understood 😉 So… if you are able to perform MITM attack against Skype user during your VAPT projects, you are more than lucky to read his/her messages.
- Research – Teams
And the last one for today – Teams. I won’t write more because the algorithm is the same. As for Teams, I’m using the 4.20.1 version.
Let’s write a message to my friend and look into the BurpSuite.
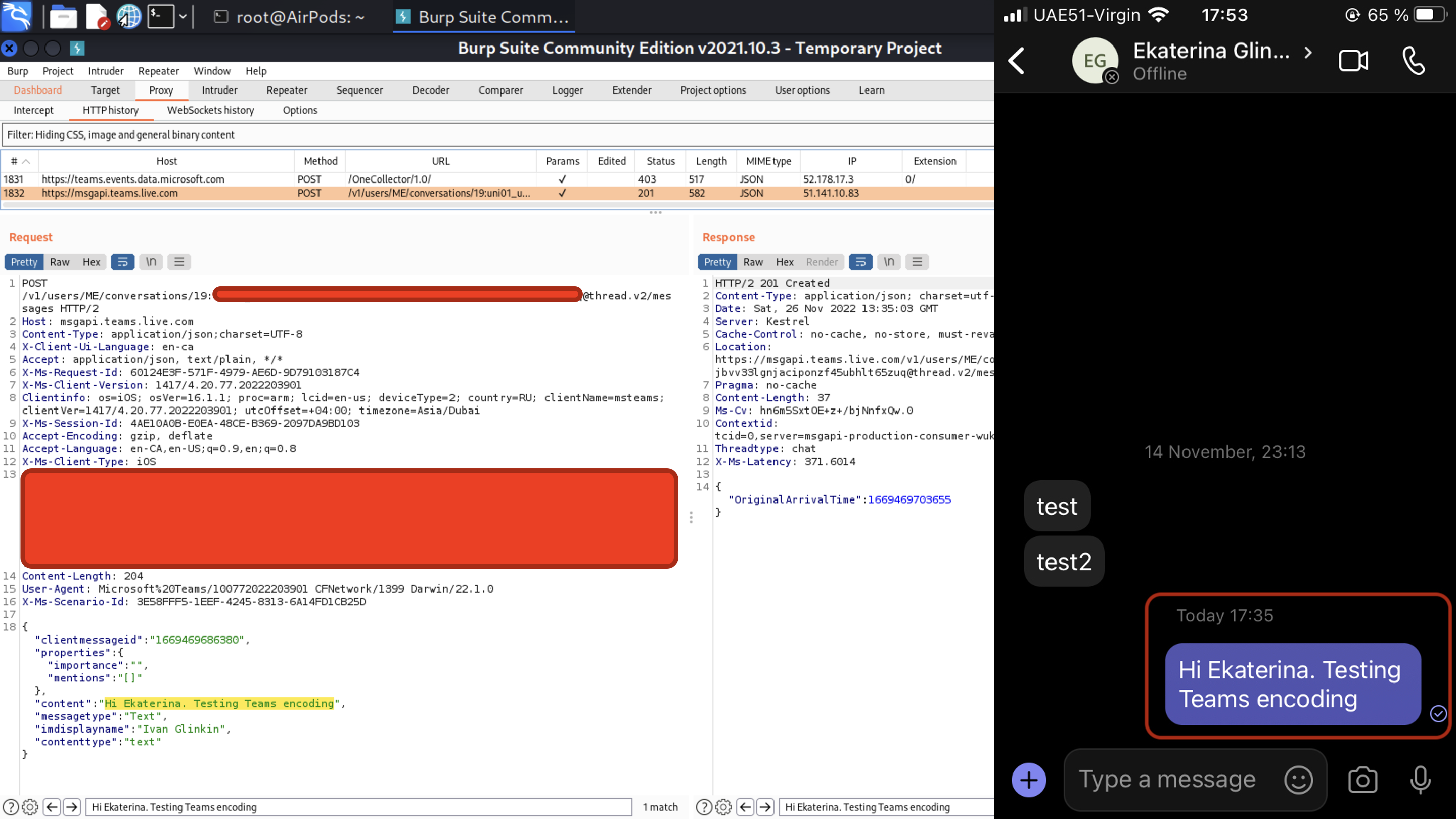
The same result. Where is the end-to-end encryption, Microsoft? I guess that question will be without answer for a long time.
- Afterword
As you can see, analyzing iOS applications is not so tough as it seems to be. You just have to set up your equipment properly and make some magic 😉 Enjoy and stay safe.