Ethical Hacking: Easy Way to Get Into / CyberYozh with Ivan Glinkin #войти_в_it Hey everyone! 👋 I wanted to take a moment toView More
Category: Walkthrough
Linksys Velop WiFi 5 Hacking (CVE-2024-36821)
IoT Hardware Penetration testing / Hacking against Linksys Velop WiFi 5 (WHW01v1) version 1.1.13.202617 (issued on September 18, 2020) Useful links: Web-site: https://www.ivanglinkin.com/ Twitter: https://twitter.com/glinkinivanView More
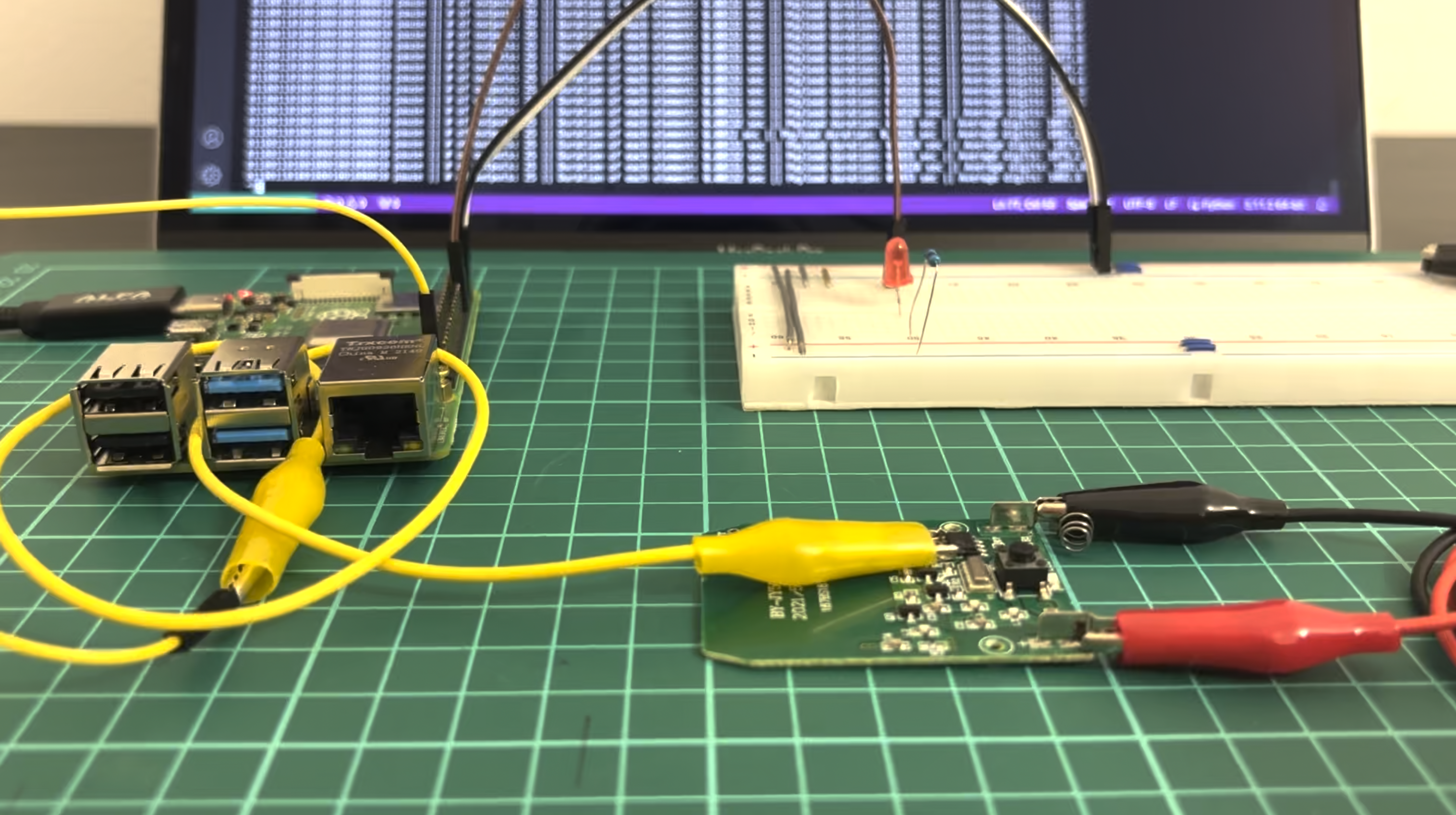
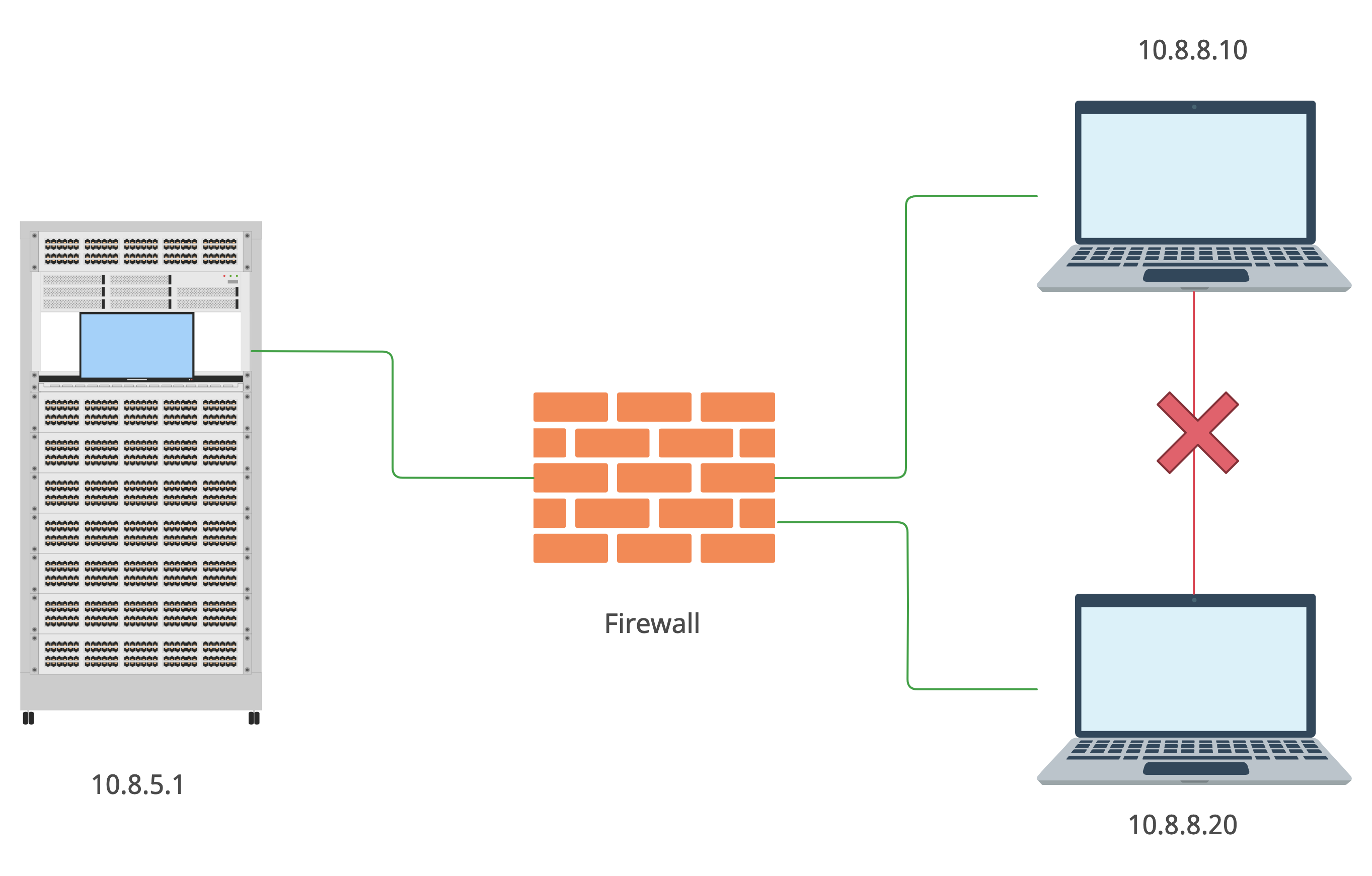
Hardware hacking: Wireless doorbell payload harvesting
Cybersecurity from the offensive perspective is not only related to web-applications and Active directory attacks. There are a lot of hacking areas beside mentioned ones:View More
HackRF as the best SDR friend for hackers
Annotation Being skilled at identifying vulnerabilities in source code, executing SQL injection attack, exploiting outdated services in well-known scripts, and even infiltrating enterprises to gainView More
Are free VPNs safe enough?
Nowadays, more and more people are using VPN (virtual private network) for different purposes. For one of them that’s a good stuff to hide theirView More
Big companies “Childhood diseases”
There is a widespread opinion as big the company is as harder to find breaches there: all the well-known vulnerabilities are fixed and mitigated, DevOpsView More
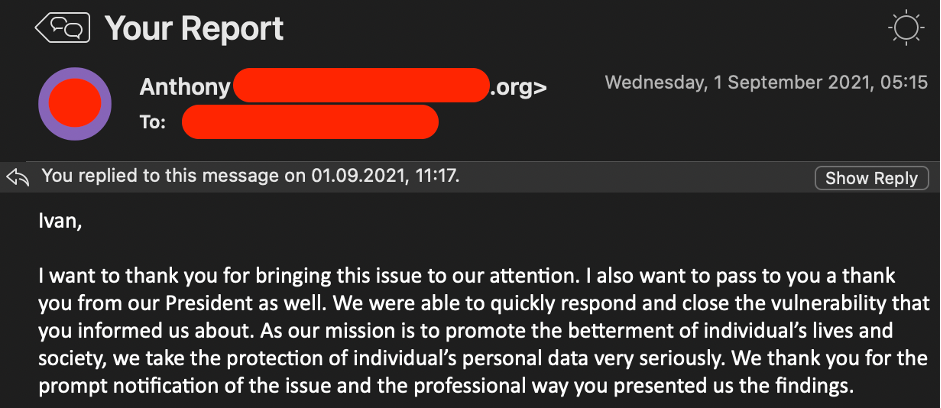
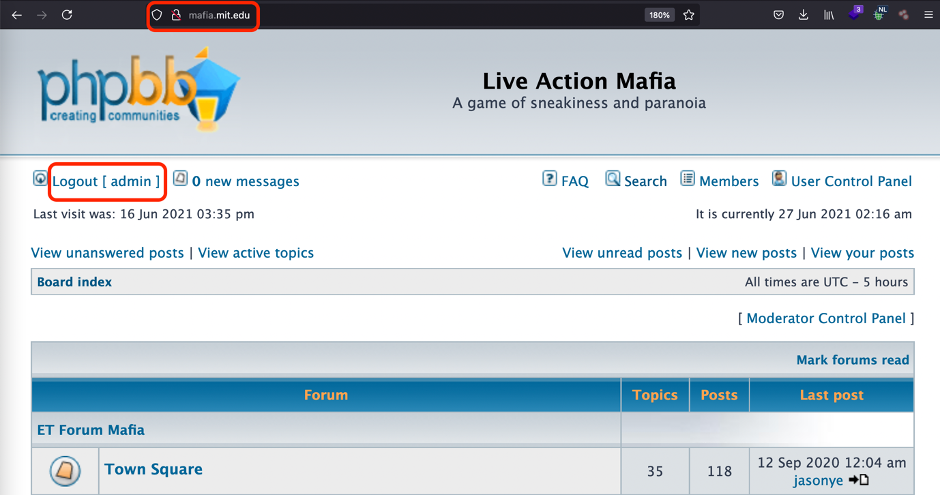
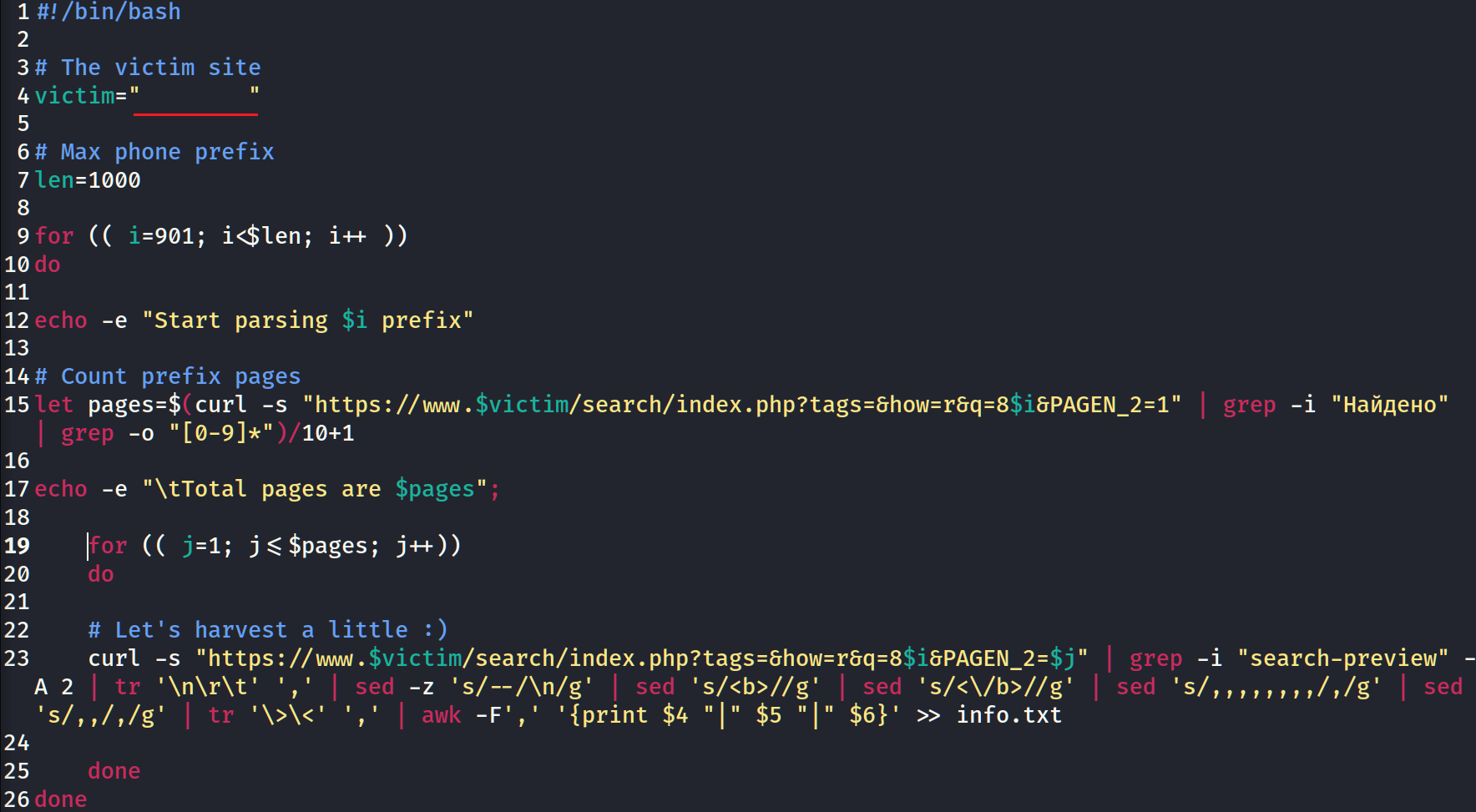
“Kept bombing out in HEAT” or how I hacked Cambridge and MIT subdomains within a week and didn’t even get any thanks
Once you got into cybersecurity, you want to hack everything. You may be surprised but in some way it’s possible and even rewarded by theView More
If you play with hackers, don’t be surprised when you get hacked or TryHackMe 0-day exploit
There is always something new happens in our life: new work, new experience, new field of study, etc. And cyber security is not an exception:View More
Data leaks without hacking
Sometimes, to get personal or other private information there is no need to crack the system. Web-site owners and/or system administrators have not set policiesView More
My way to the OSCP certification
Having achieved the Offensive Security Certified Professional (hereinafter OSCP) certificate, especially in such short period, plenty of people started asking me to share my stepsView More
Bug Hunter – HackTheBox – Invite Code issues
One of my favorite deeds is optimization and automation. I’d better sit for a while thinking about an algorithm and spend some time for codeView More
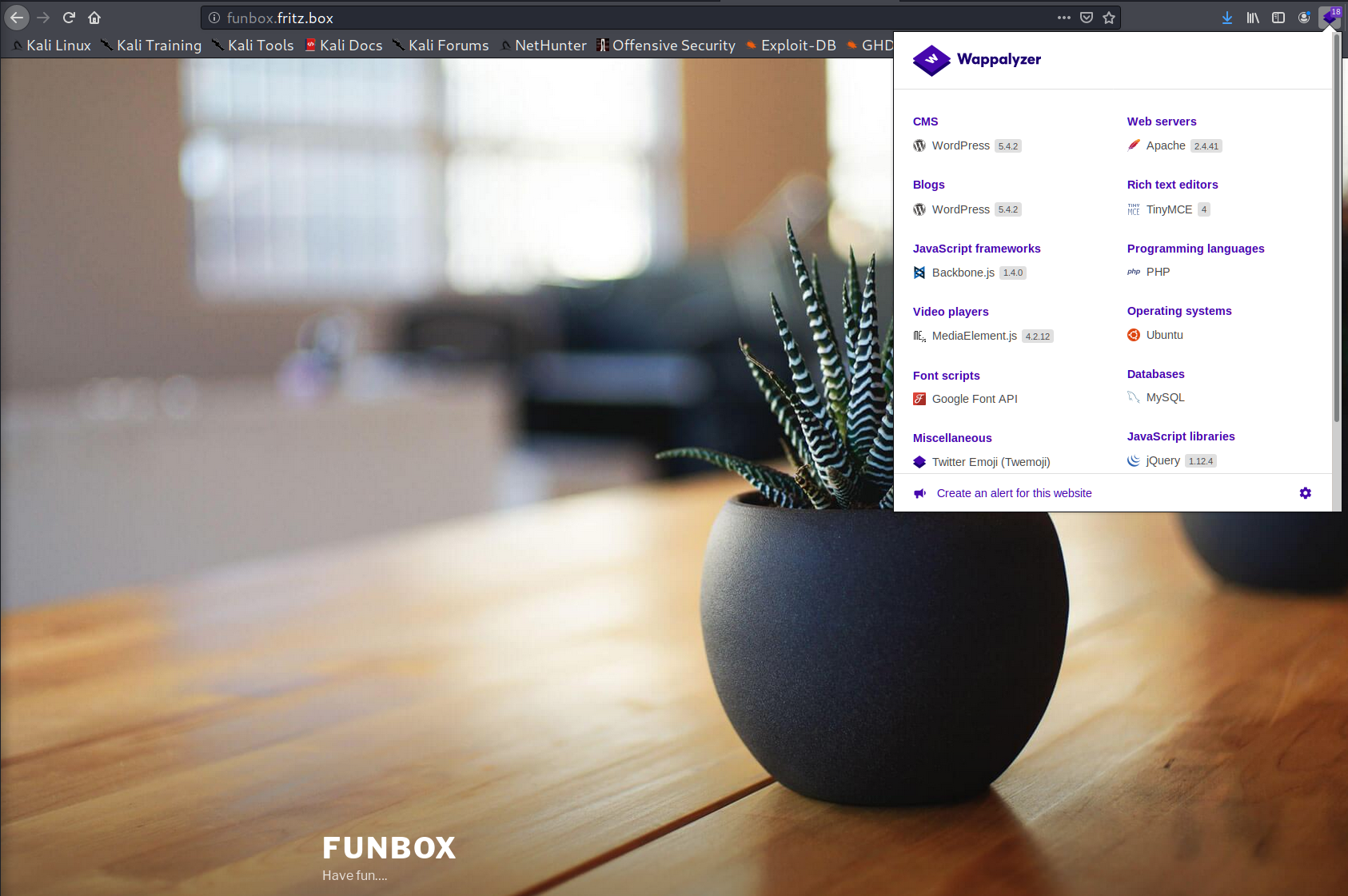
Funbox 1 walkthrough
Hello hackers. Today we are talking about another VulnHub machine – “Funbox: 1”, made by twitter@0815R2d2. It’s presented as Boot2Root and you will be ableView More
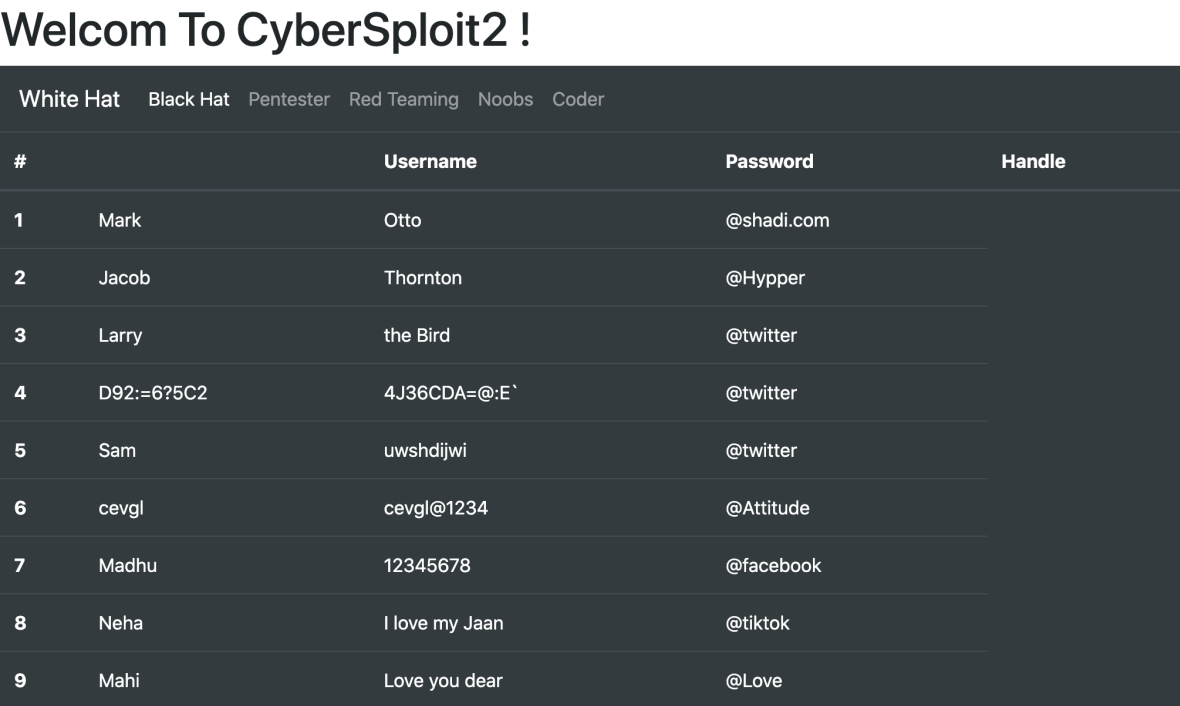
CyberSploit 2 walkthrough
Hello hackers. Today we are talking about one the latest VulnHub machines called CyberSploit: 2. It was a quite easy challenge to me which IView More
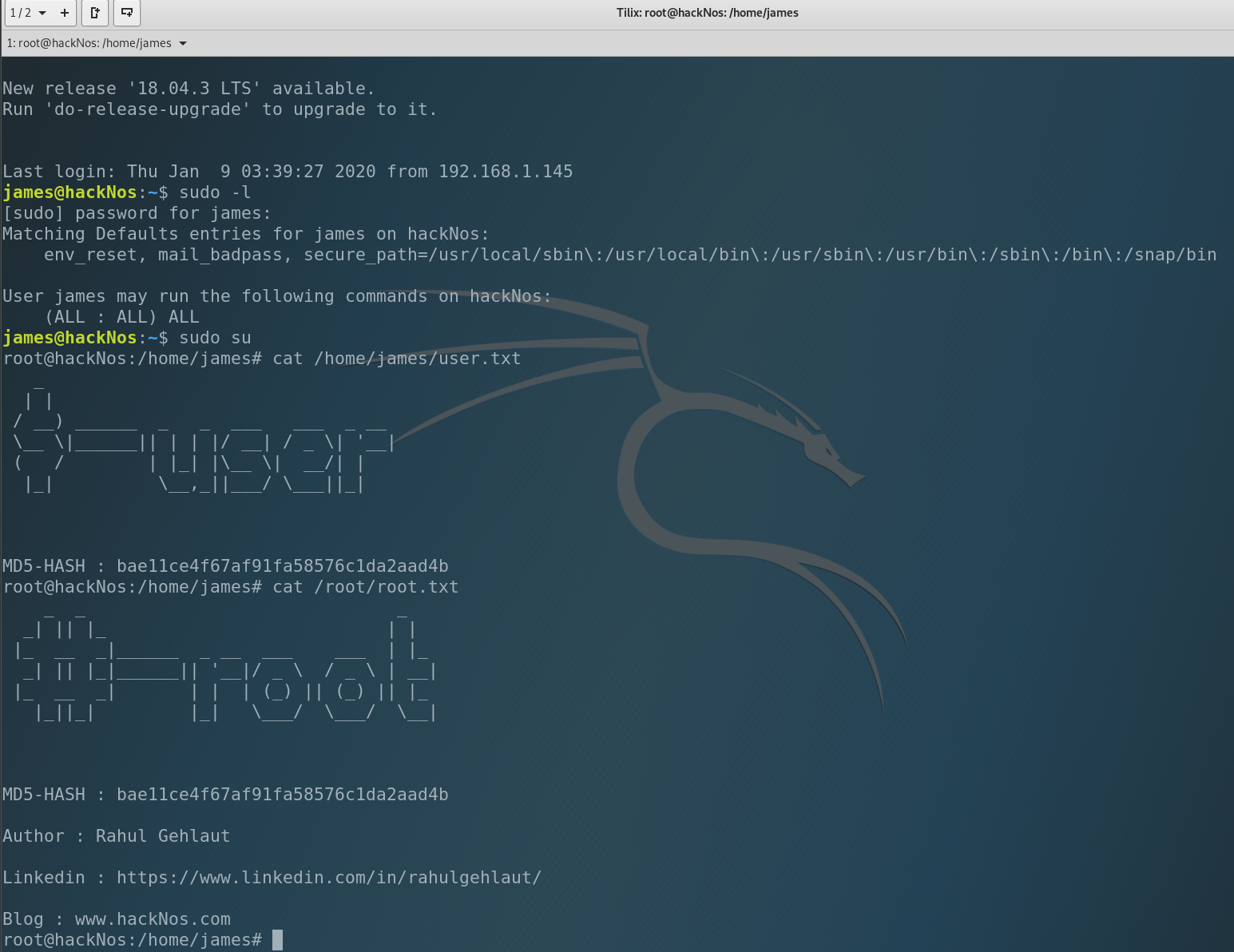
Os-hackNos 1 walkthrough
Hello there! Today we will try to get root of the VulnHub machine named hackNos: Os-hackNos. Let’s see the description. It’s easy to intermediate difficultyView More