Once you got into cybersecurity, you want to hack everything. You may be surprised but in some way it’s possible and even rewarded by the real money and called BugBounty. HackerOne is a platform where companies propose to assess their IT environment for the reward. My main aim was to get a letter of appreciation from the prestigious university and my choice fell to Cambridge and MIT, as universities which are presented on HackerOne.
- Cambridge
The University of Cambridge is a collegiate research university in Cambridge, United Kingdom. Founded in 1209, Cambridge is the second-oldest university in the English-speaking world and the world’s fourth-oldest surviving university, and one of the most prestigious academic institutions in the world. (c) Wiki
University of Cambridge has several different departments, one of which is Cambridge University Press. The last one is the oldest university press in the world and currently the second largest university press in the world.

As you may already guess, the object of my research was one of the subdomains of the Cambridge University Press website – Cambridge GO.
The portal is free to create an account so I did that immediately. Having done a little research, I decided to log out.
Having logged out, Cambridge Go website links me to https://testhub.cambridge.edu.au website (IP address is 104.17.232.89): ID requests 17736 and 17737.
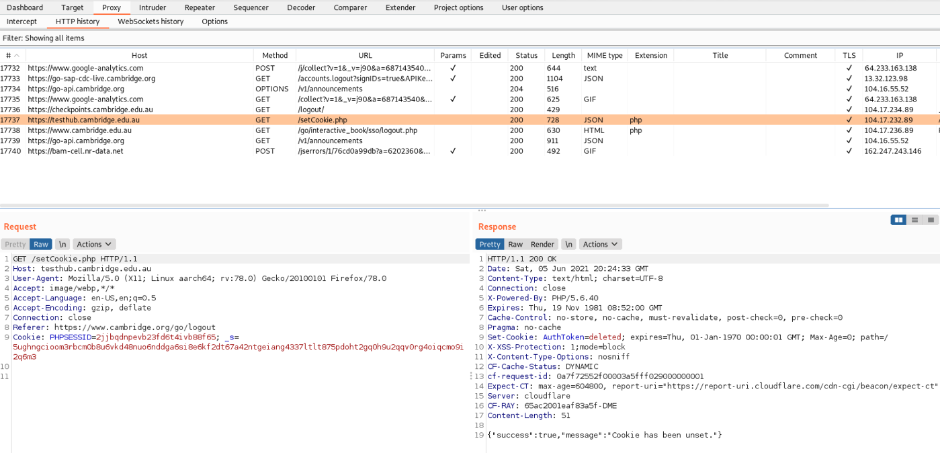
The next step is to check the found web-address.
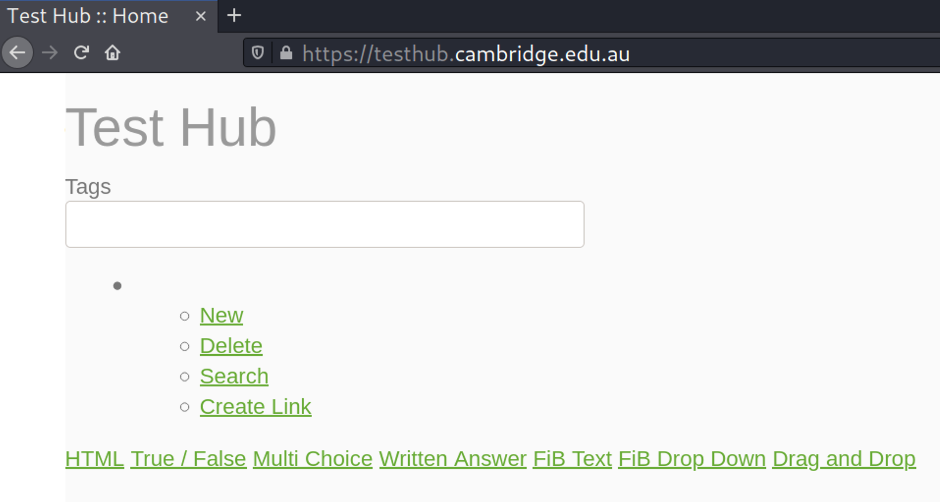
TestHub website is quite simple. All presented links are broken and link to #. Having done a research, I found the website is under the Concrete-5.6.0.2 CMS (released at Jan 24, 2013, pretty old).
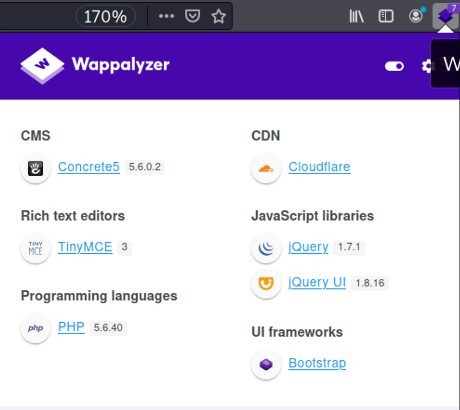
After the deep research I was able to find the hidden link to a login panel.
Followed the link I found a login page.
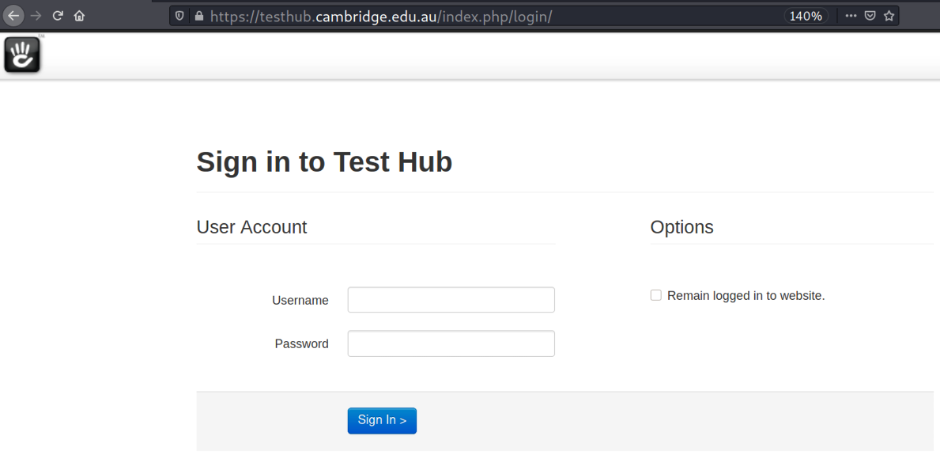
Having tried test:test as a login and a password, system responds as “Invalid username or password”.
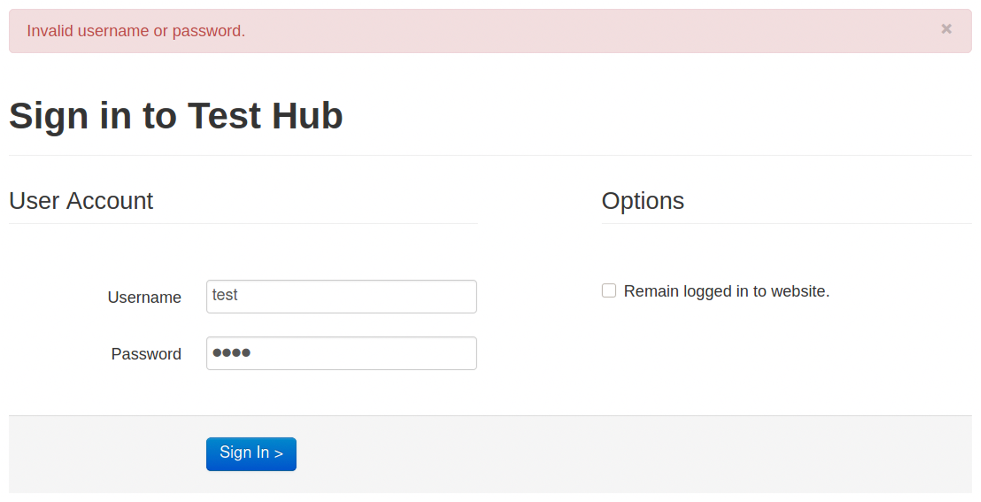
After a research default CMS credentials, I found that login is admin and the password is that was setup during the installation.
Having tried the admin:<<CENSORED>> as a login and a password (the easiest one), website relocated me to the home page – https://testhub.cambridge.edu.au/ Unfortunately, there was no visible signs pointed I’m the admin except the source code:

After a deep research and having read the CMS documentations, I was able to find the dashboard https://testhub.cambridge.edu.au/index.php/dashboard/
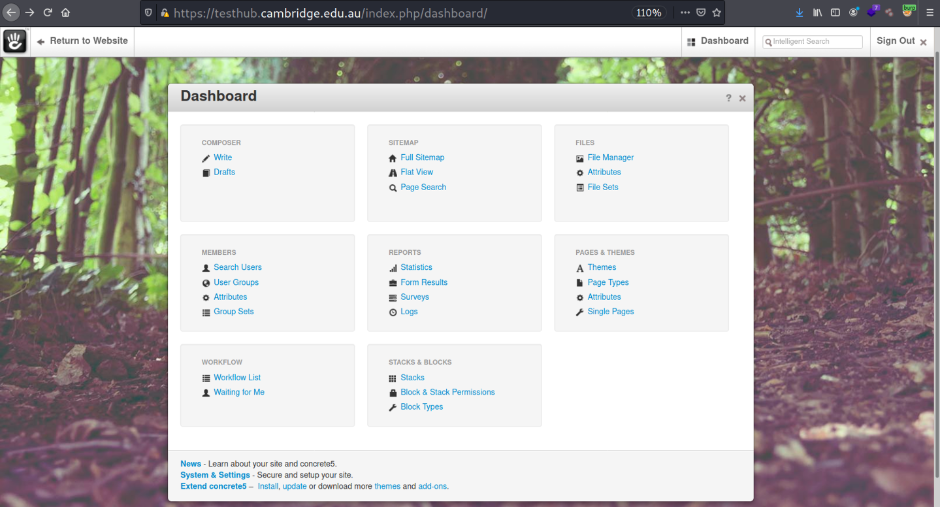
PoC: I’m the admin on the https://testhub.cambridge.edu.au/ and got the full control under the Cambridge GO API
According the logs, the last password change was on February 2016!!!
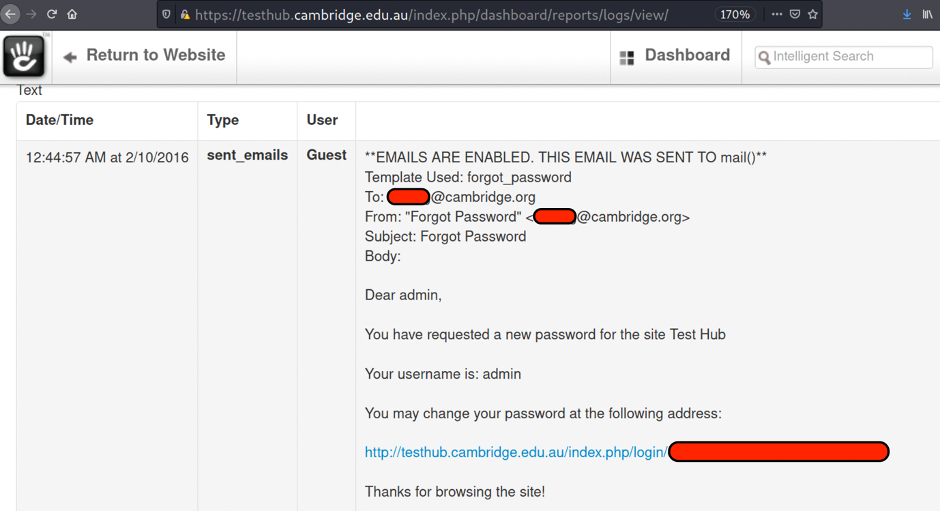
Possible way to further exploitation
One of the possible ways to get a reverse shell is the next:
- Add a PHP extension to
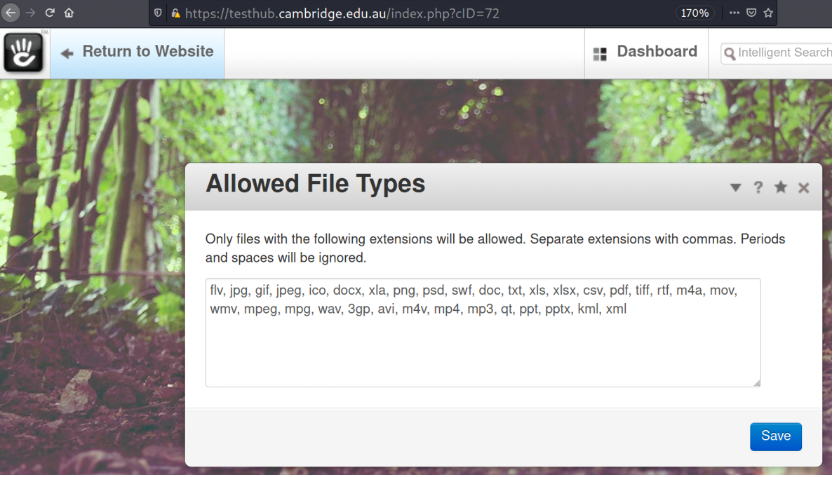
- Upload an avatar/background picture as a PHP file with a reverse shell script
- Run the uploaded page
Being an ethical hacker, the further exploitation was over!!!
- MIT (Massachusetts Institute of Technology)
Massachusetts Institute of Technology (MIT) is a private land-grant research university in Cambridge, Massachusetts. Established in 1861, MIT has since played a key role in the development of modern technology and science, ranking it among the most prestigious academic institutions in the world. (c) Wiki

Like the University of Cambridge, MIT has plenty of web-site subdomains as well. One of them became my target, but let’s consider my vulnerability assessment step by step.
The first stage of any pentest is reconnaissance and this one is not an exception. Following that way, I decided to use my own application – Fast Google Dork Scan (https://github.com/IvanGlinkin/Fast-Google-Dorks-Scan).
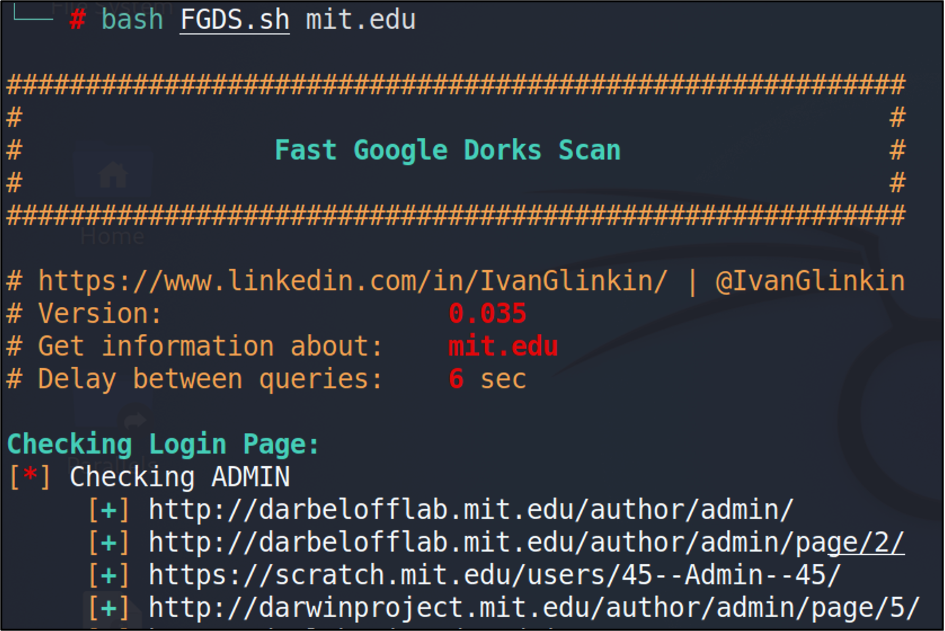
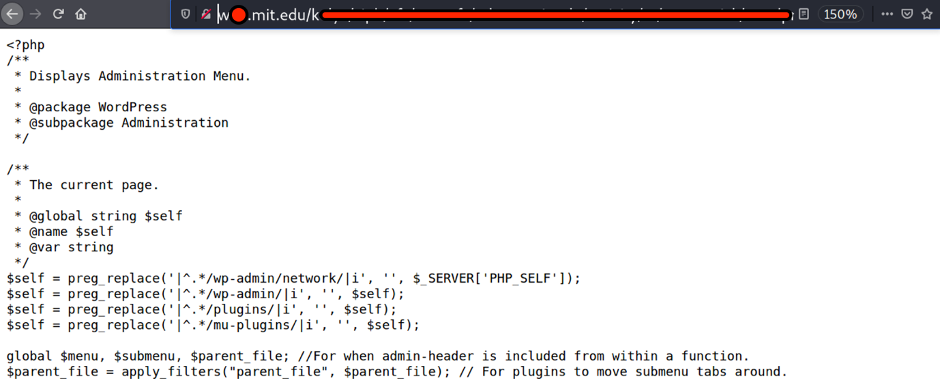
Fast Google Dork Scanner did a great job and presented a huge report. During the research process I was able to find at least one crucial link – https://w*****.mit.edu/k*****.php
Having checked it I found a PHP file which I was able to read
Further investigation revealed that I may see all the files within the directory, for instance
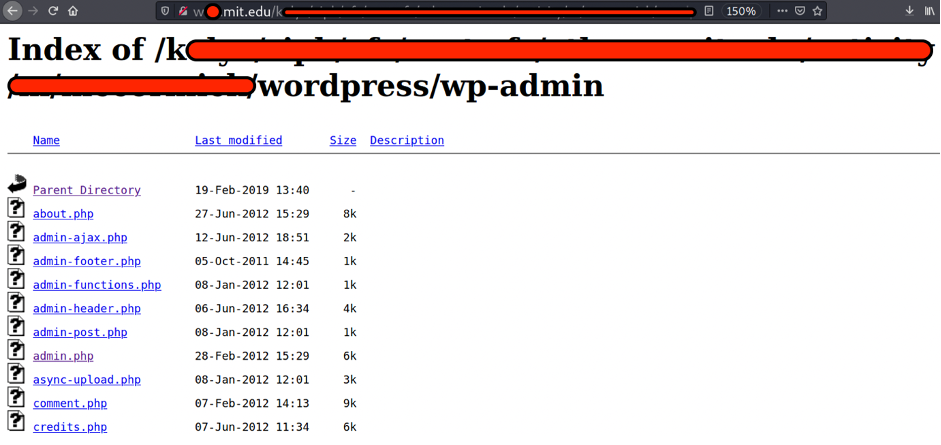
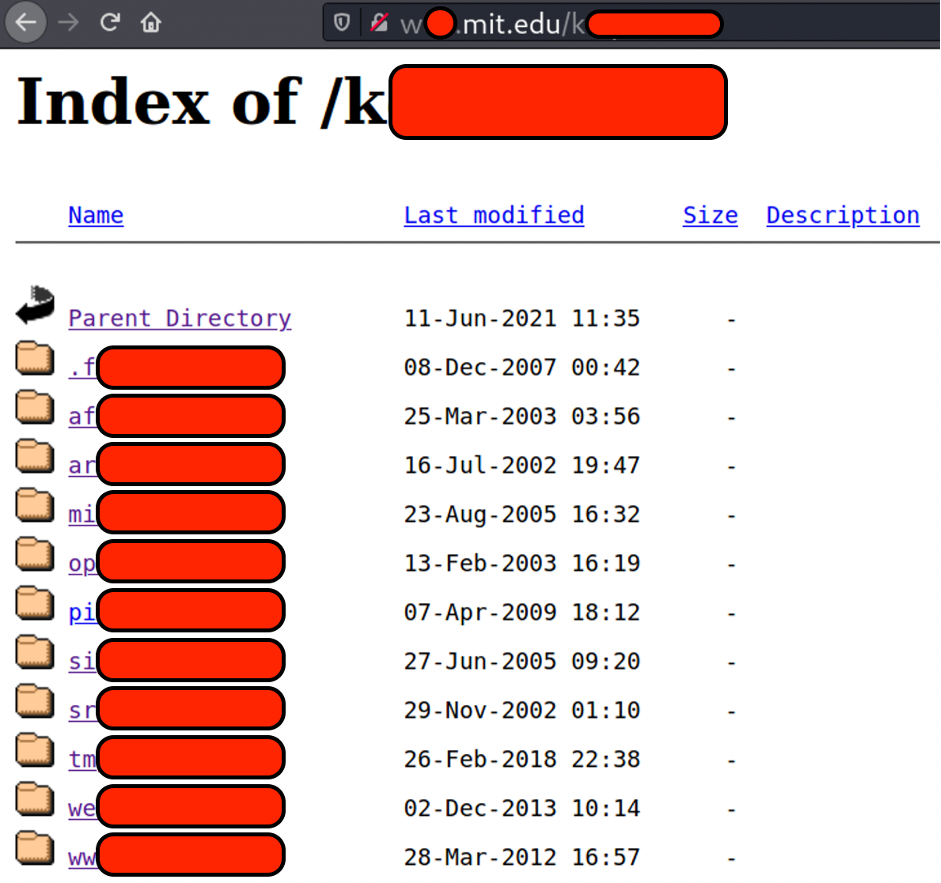
Seems like I found a global MIT institute storage, consists of plenty of sensitive files, readable by unauthenticated user. That was an incredible found.
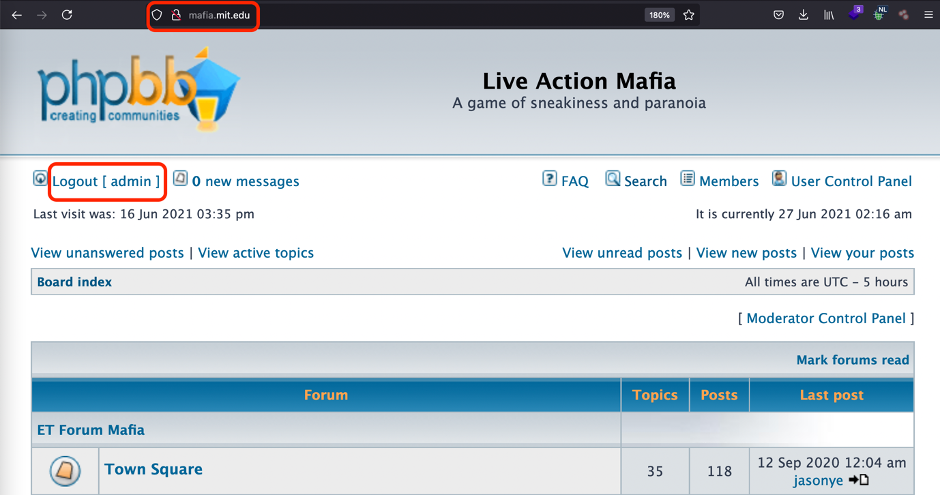
Let’s dig a little big deeper and try to find some valid credentials. Followed the link http://w*****.mit.edu/k*****/mafia/dbdump/ we may find mafia web-site (http://mafia.mit.edu/) database dumps
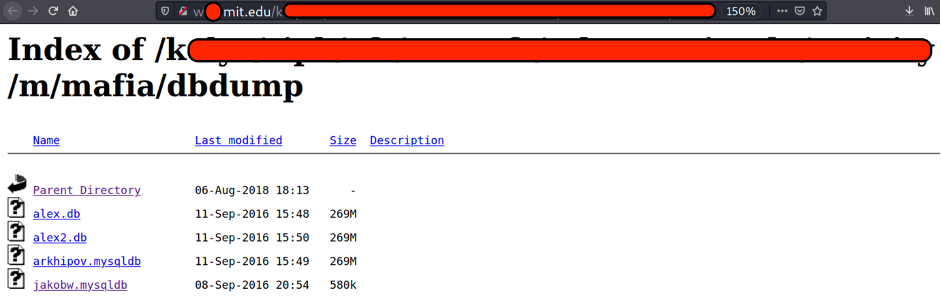
269 Megabyte!!! Not bad!!! Having download the DB, I found at least 1905 rows of user profiles including username/nickname, email, password hash, the last IP visited the site and so on.
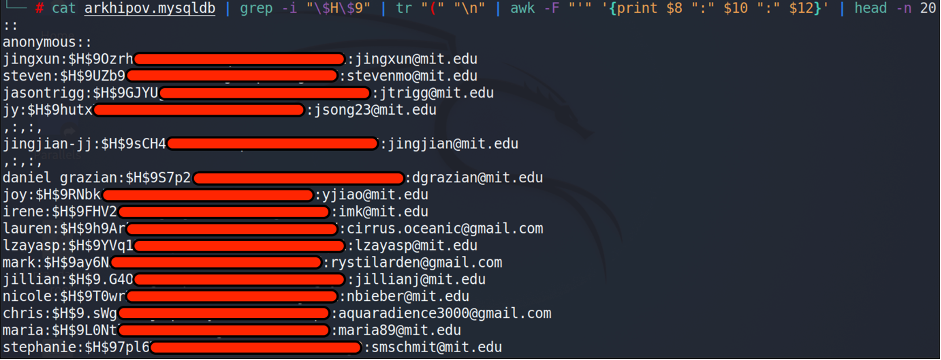
Pretty good leaks of MIT passwords, isn’t it? Good enough, but I felt I was in the middle of the something huge.
Let’s enumerate a little more and go to
http://w*****.mit.edu/k*****/mafia/Scripts/turbogears/mafia-site/
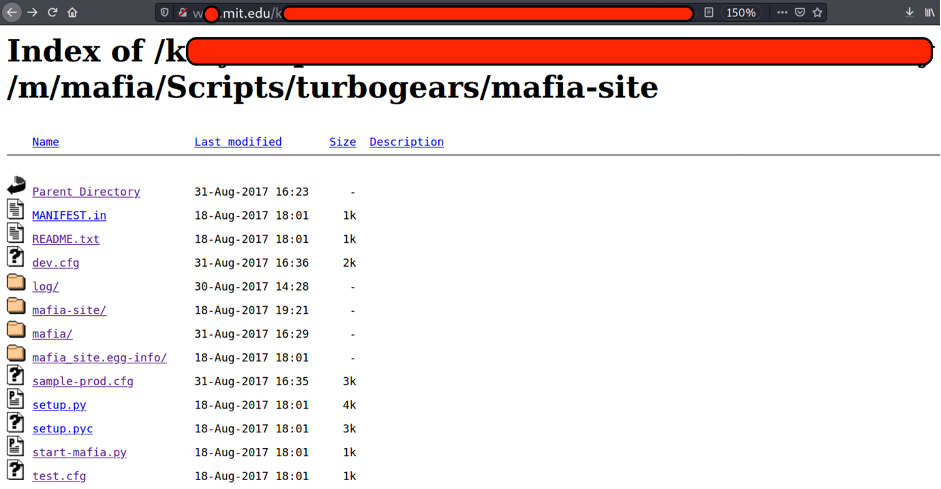
As you may see there are several files. The most important file to us is dev.cfg. Let’s open it
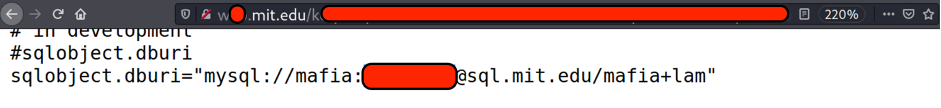
As you may guess I’ve succeeded to find MsSQL database credentials. Let’s try them out. Fortunately, there is the phpMyAdmin dashboard so I used it.
And I successfully logged in.
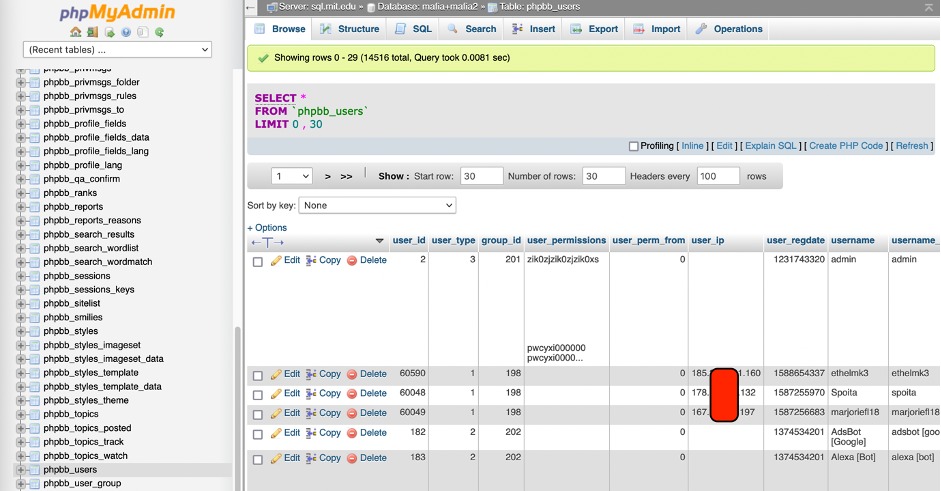
Then I decided to find, how many users had registered since 2017 and it was 14516. May you imagine, 14516 rows with username, MIT email and password hash? I assume, that may be a really huge leak.
As a final step, known the web-site admin hash, I decided to brute force it. And it took… 2 seconds.
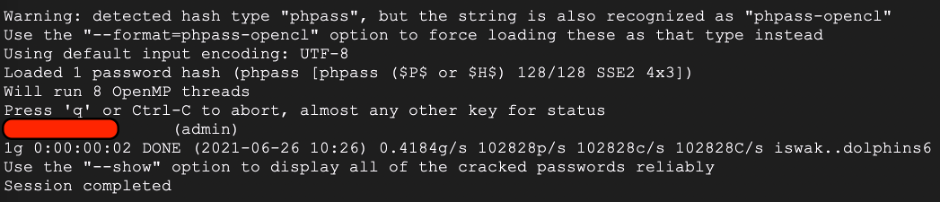
Let’s check it out.

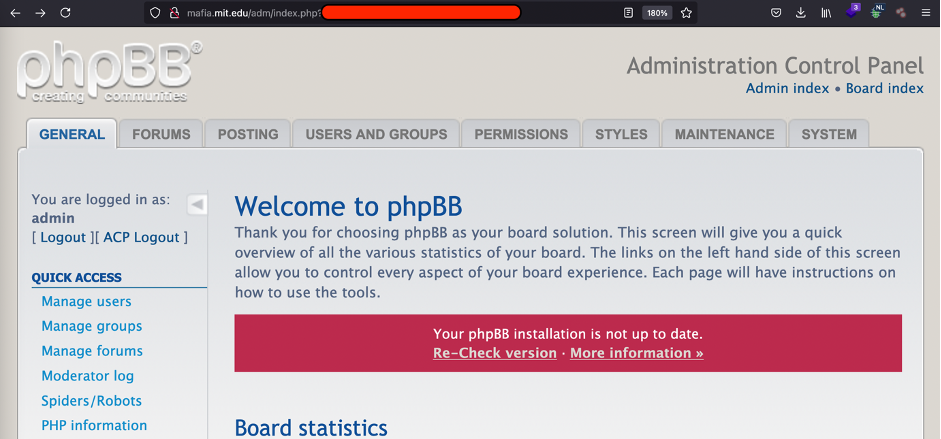
PoC: I’ve got the full control over the http://mafia.mit.edu/ web-site.
There are plenty of ways how to get reverse shell from phpBB forum, but, being an ethical hacker, the further investigation was over.
- Bug bounty without a bounty
And the most interesting part: what bounty did I get? I got to show you some emails.
Cambridge incident was reported on June 06, 2021.
Have not got a reply, I sent another letter from my second email next day (in case my first letter may be sorted as spam). Computer Security Team resolved my report in 2 days (change the admin password) but the was no any feedback (even by email). Having waited for a week I decided to write another letter.
And they finally replied…
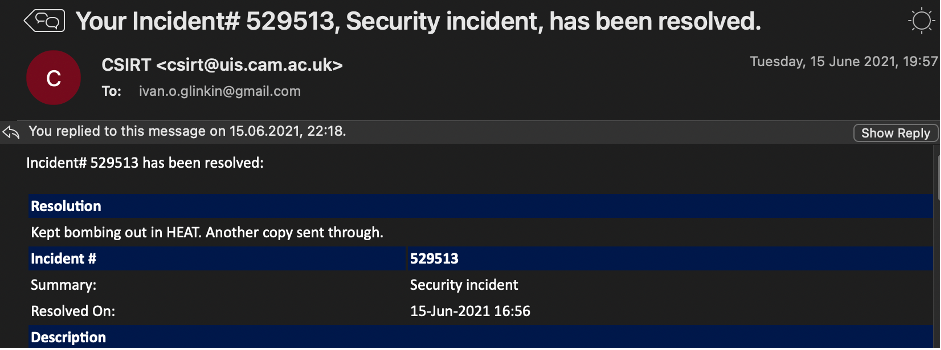
That’s all (there was my report in the middle of the letter). Have you ever received emails like that from the one of the oldest and prestigious university? I have and I proud of that (sarcasm).
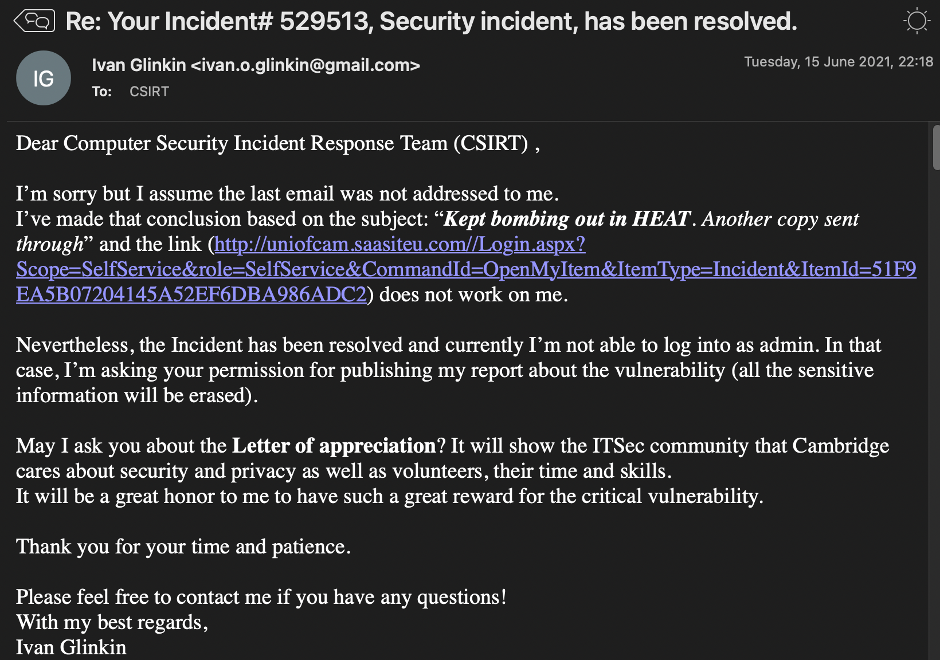
I’ve replied to them correctly but there is still no answer and I think it never will.
Next one. MIT Incident was reported on June 15, 2021.
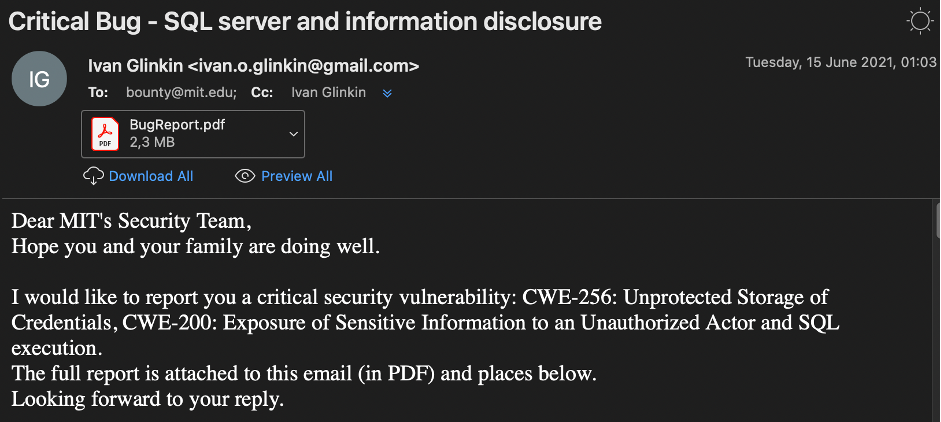
They answered to me quite quick – in 14 hours (and also keep in mind the time shift).
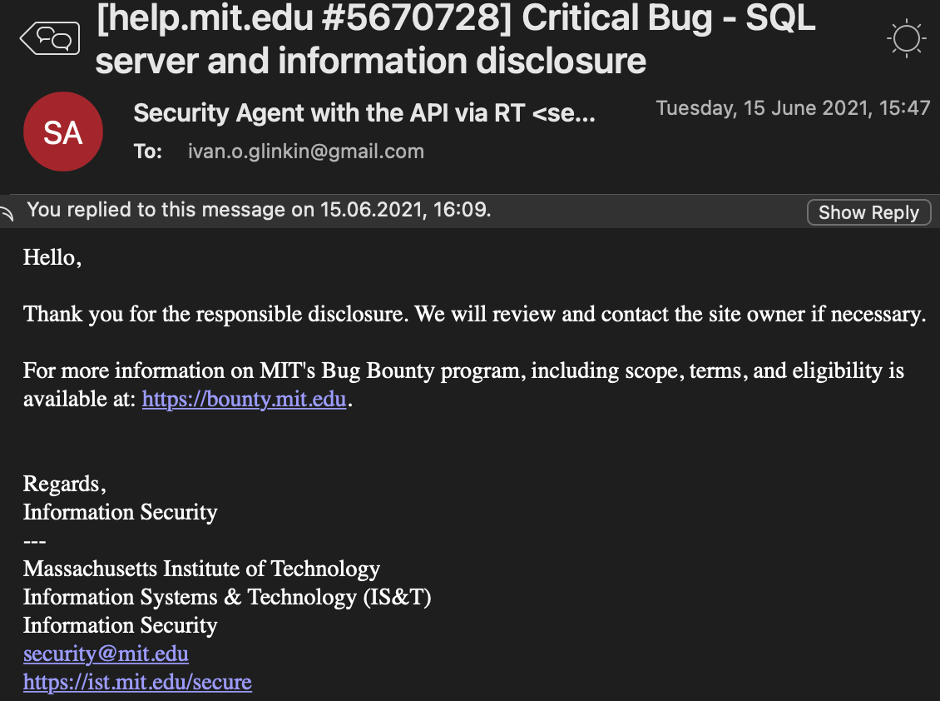
The plain auto-answer. But at least they thanked me for the responsible disclosure. I really appreciate that.
As I mentioned earlier my purpose was to get a letter of appreciation, so I sent a confirmation email.
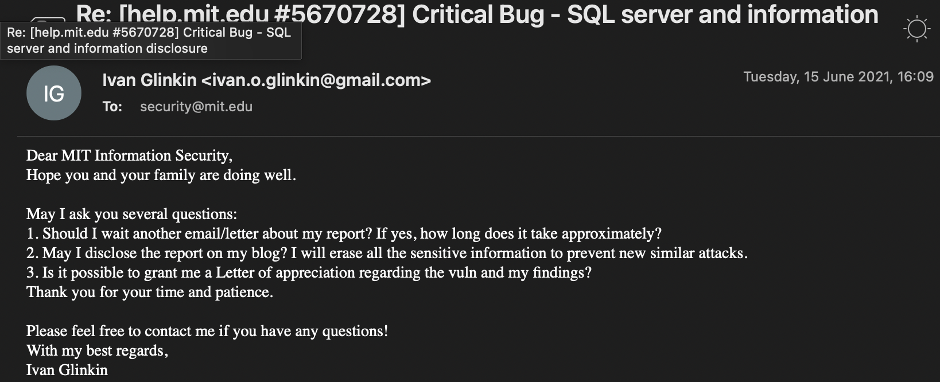
Similar to University of Cambridge, I’m still looking forward to the reply as well.
- Conclusion
Well, let’s summarize. I succeeded to get full control over the Cambridge and MIT web-site subdomains. I found a leak of ~2K and possible leak of ~14K rows of usernames, emails and password hashes.
I assume there were 2 critical vulnerabilities and I’m glad I’ve been able to proof my ability to hack such huge companies.
Speaking of letters of appreciation… who needs them? 😉