From ages ago till now there are plenty of discussions regarding the best/appropriate approach of using a pentesting OS: as a main, live system, dualView More
Tag: docker
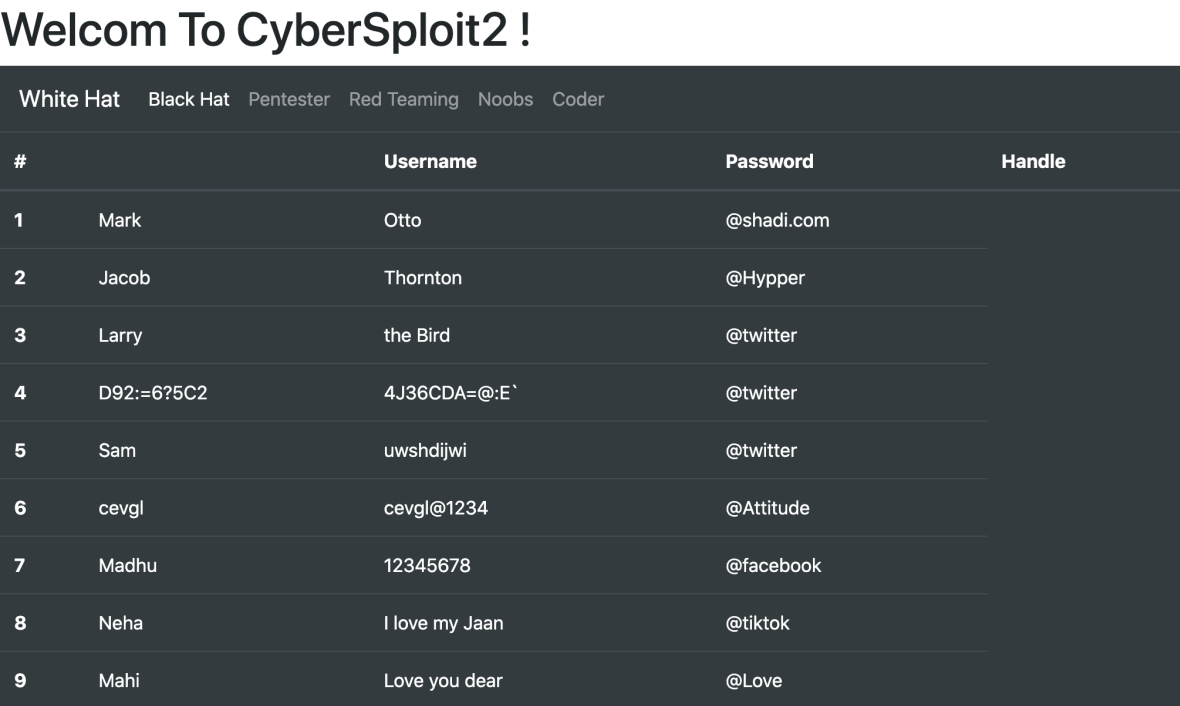
CyberSploit 2 walkthrough
Hello hackers. Today we are talking about one the latest VulnHub machines called CyberSploit: 2. It was a quite easy challenge to me which IView More