From ages ago till now there are plenty of discussions regarding the best/appropriate approach of using a pentesting OS: as a main, live system, dualView More
Tag: Kali
Brief iOS apps analysis (without Jailbreak)
For cyber security analysts and penetration testers dealing with mobile applications is the day-to-day activity. But if we are talking about Android applications, it’s quiteView More
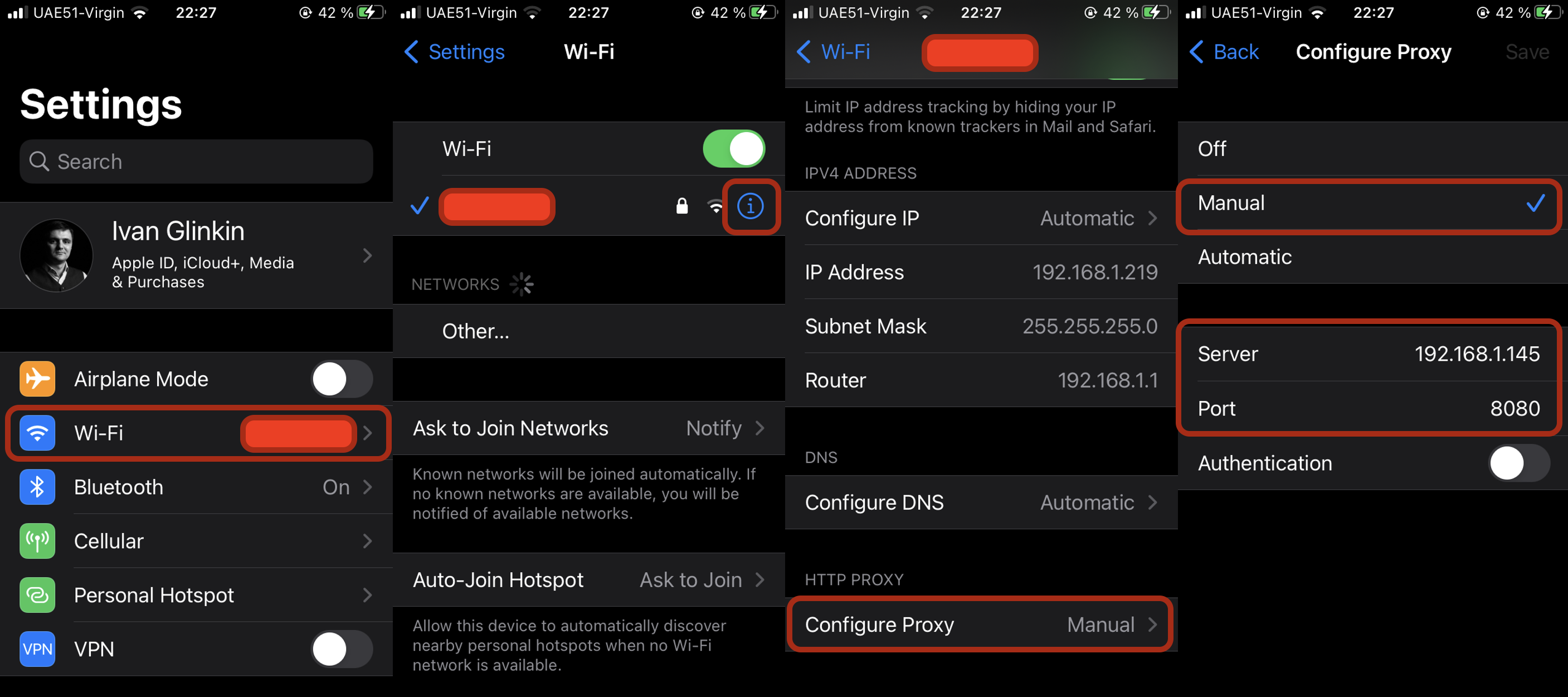
Are free VPNs safe enough?
Nowadays, more and more people are using VPN (virtual private network) for different purposes. For one of them that’s a good stuff to hide theirView More
Alfa AWUS036ACH WiFi adapter install on Kali Linux
That is the single instruction how to install Alfa AWUS036ACH WiFi adapter on Kali Linux (including M1 Mac CPU). INSTALLATION (approach 1) 1. sudoView More
Install Volatility on Kali Linux (including M1 Mac CPU)
That is the single instruction how to install Volatility application on Kali Linux (including M1 Mac CPU). INSTALLATION #!/bin/bashsudo apt-get updatesudo apt install -y python2.7sudoView More
If you play with hackers, don’t be surprised when you get hacked or TryHackMe 0-day exploit
There is always something new happens in our life: new work, new experience, new field of study, etc. And cyber security is not an exception:View More
How to cheat on a Cyber Security exam
Cheating is unfair, wrong and, in particular cases, strictly prohibited by the law. It may cause you lose your friends, family, achievements, work and whatever.View More
My way to the OSCP certification
Having achieved the Offensive Security Certified Professional (hereinafter OSCP) certificate, especially in such short period, plenty of people started asking me to share my stepsView More
Useful bashrc configuration file
Hello Linux users! When I’m doing my job I’m trying to set my working place as efficient and useful as it’s possible. Bash terminal isView More
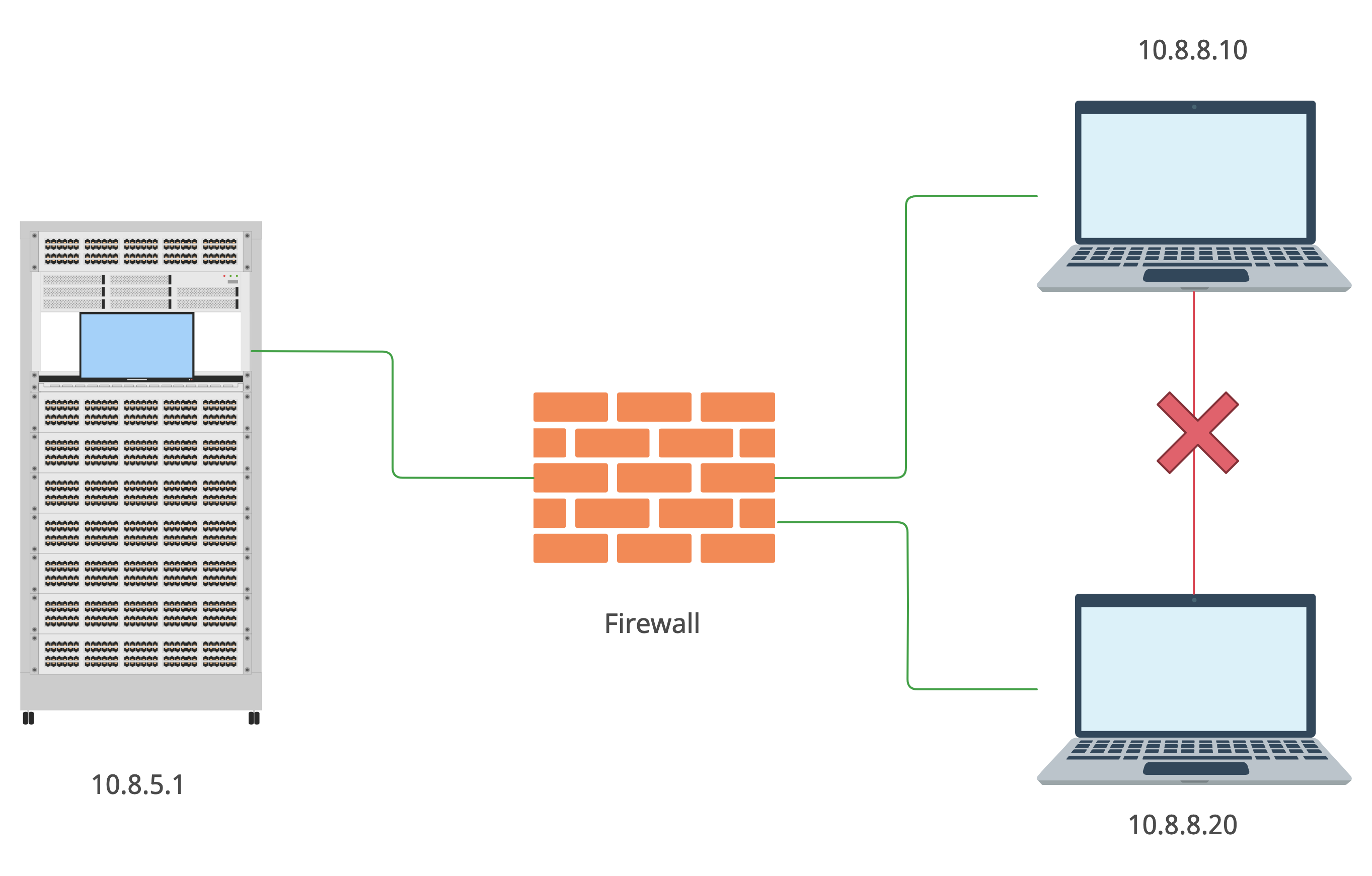
It’s all about RDP (hacking 3389 port)
Hello hackers! Today we are talking about one of the famous and loved by Windows sysadmins remote managing stuff – Remote Desktop Protocol. We willView More