The first thing every penetration tester performs getting into a controller domain subnet is to brute force discovery of users which is called a Kerbrute attack. There are plenty of articles about that type of exploitation but in every source an author uses a preset dictionary for his purposes which is no so perfectly related to the real life. Today I will try to fill this gap and create a universal working dictionary for Kerbrute attack in the Russian AD.
- The concept
Active Directory Domain Services known as AD DS stores information about the domain’s members, including devices and users, verifies their credentials and defines their access rights.
Enumerating users aka Kerbrute attack allows you to reveal which users accounts are on the domain for further attacking and escalating the privileges.
Depending on your preference you may use any related application. I prefer using kerberos_enumusers module within Metasploit (use auxiliary/gather/kerberos_enumusers).
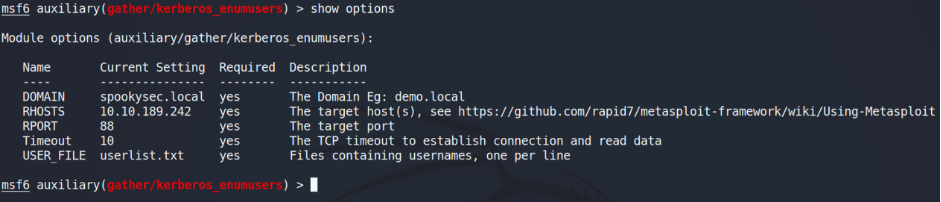
Once enumeration is completed, we can find all the domain users.
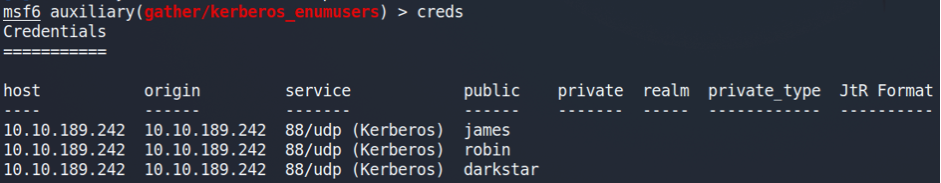
The next thing we have to do is to understand how domain administrators create users in the domain, or, to be more specific, what is the pattern for usernames.
The best practice for the corporate usernames is to combine person’s surname and the first letter of his name, for instance, in my case, iglinkin@corporate.local. Truthfully saying, the pattern depends on the company’s security policy and may also be the next: i.glinkin@corporate.local, ivanglinkin@corporate.local, glinkini@corporate.local, glinkin.i@corporate.local, glinkinivan@corporate.local or even just a second name – glinkin@corporate.local.
Let’s find out the real cases. We will start with Microsoft where using NSurname@microsoft.com (https://www.microsoft.com/en-us/research/people/jwinn/).
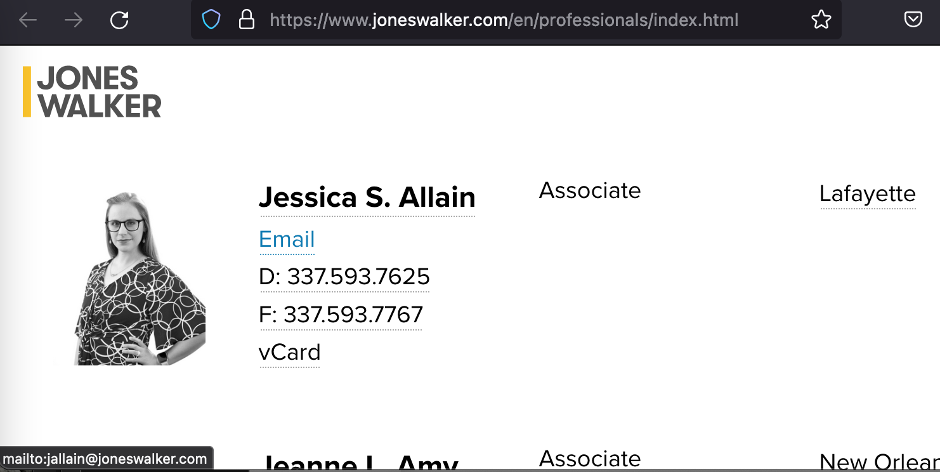
The same format for the Jones Walker company (https://www.joneswalker.com/en/professionals/index.html).
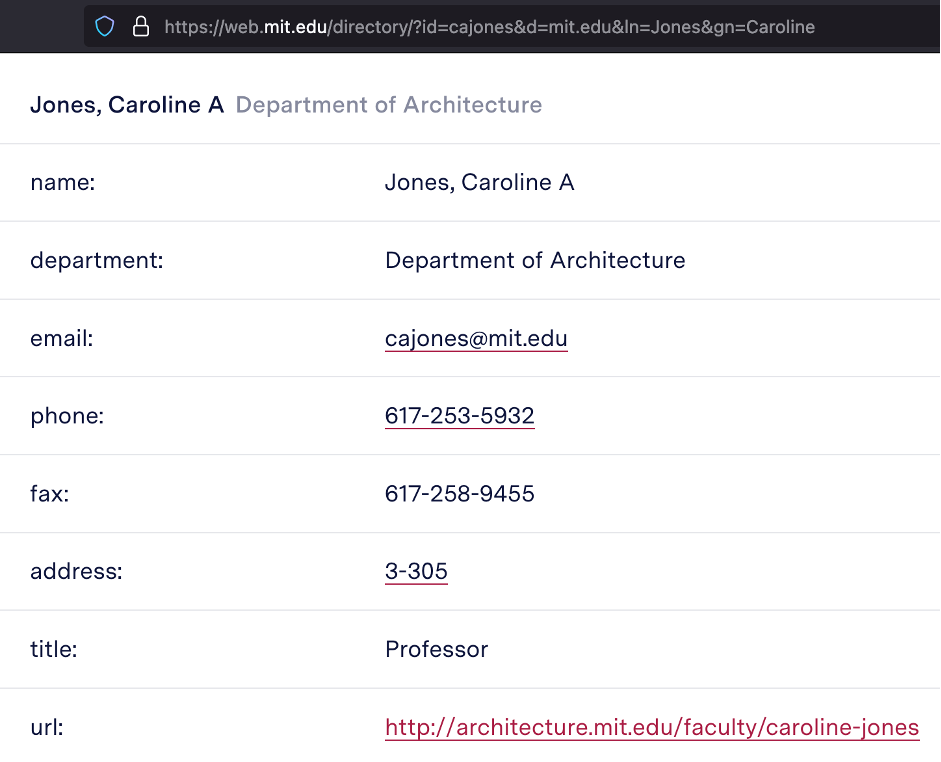
For MIT it’s even the first letters of first and given names followed by a surname – FGSurname@mit.edu. (https://web.mit.edu/directory/?id=cajones&d=mit.edu&ln=Jones&gn=Caroline).
- Harvesting
Ok, we defined the core statutes. But what’s further?
As you may see from the previous section, the surname (last name) is the main part of the corporate login. The first name is not so interesting due to the only char, so we do not even have to know the real name – we will add just a letter before or after the surname.
Consequently, the next toughest and the most important phase at the same time is we have to collect the surnames data.
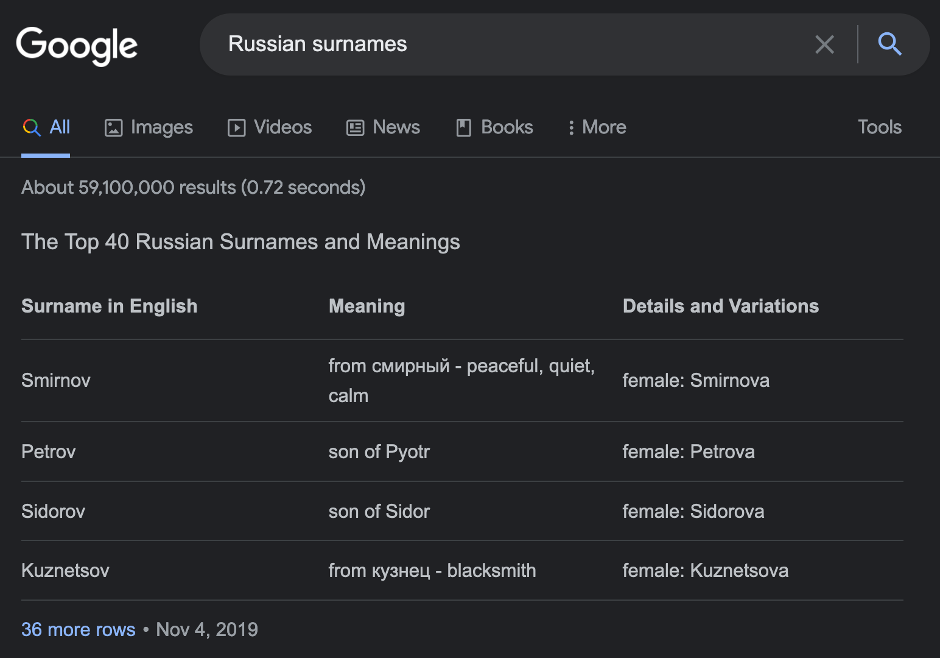
It’s an Internet age so let’s google a little – “Russian surnames”.
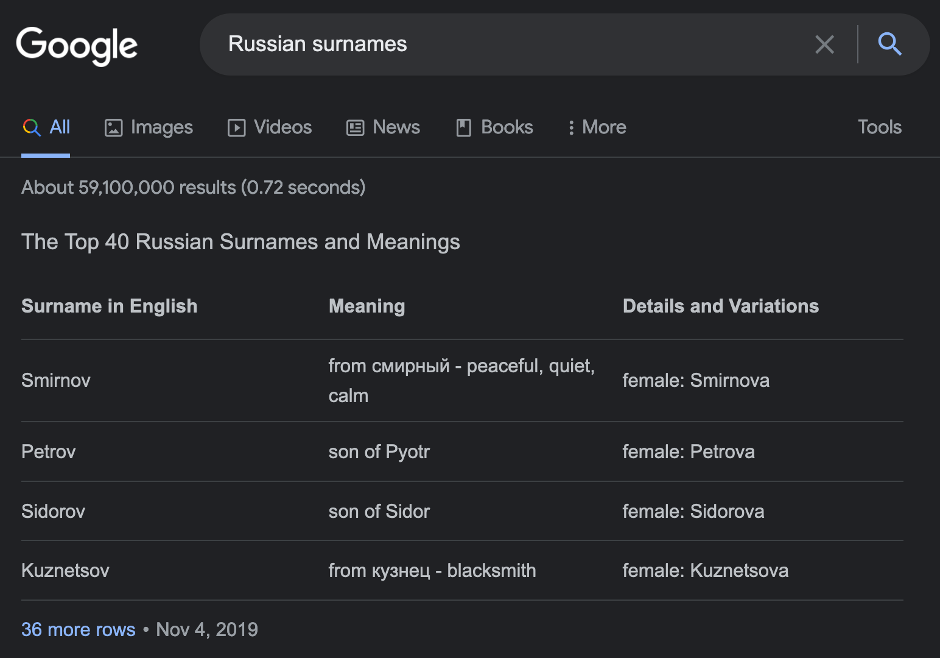
40 surnames – not so much especially when there are more than 200k different surnames in Russia. But when you dig a little bit deeper you may find several crucial moments.
The first is that all of the Russian surnames’ lists in … Russian. So, the first issue we faced is we have to transliterate the last names into English because of Active Directory does not understand any other languages except the last one.
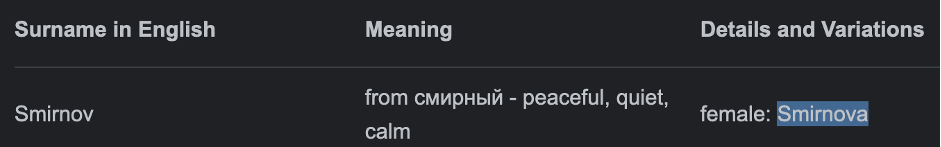
The second problem is the spelling of the Russian female surname. As you may see in many cases (not all) there is an additional “A” at the end. Just for example and to be clear, Smirnov is a man’s last name, Smirnova – woman’s. In that case, the full amount of the Russian surnames is about 310 000. Impressive, isn’t it?
It’s harvesting time. Having browsed the Internet, I have found the interesting source – https://woords.su/full-name/russian-surnames. It contains almost all Russian surnames. Let’s look at it.
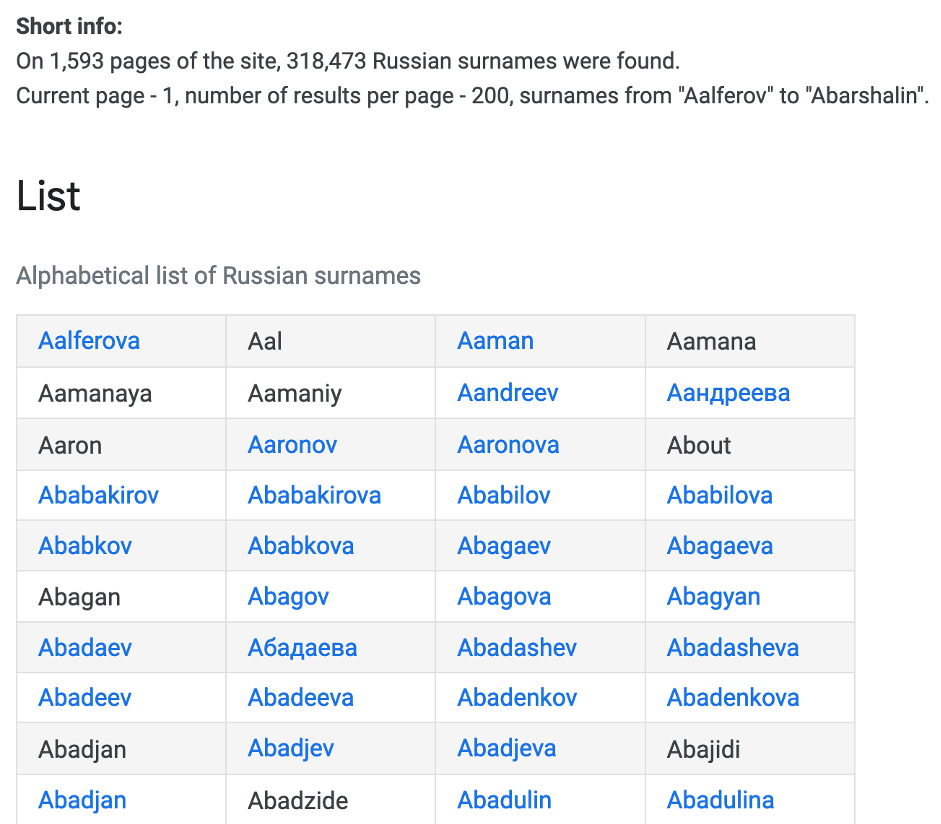
Unfortunately, all of the surnames are in Russian (Google translate addon helped us). But the good news is there are female’s last names too so we do not have to perform additional transformation.
Ok, let’s get all of the surnames at first.
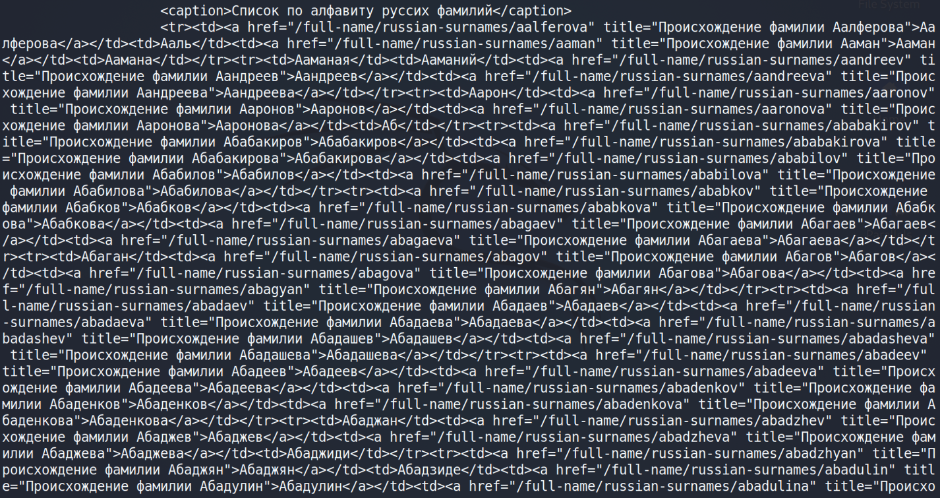
Wow, that’s quite tough to read, but we have to. Let’s implement a little bash magic.
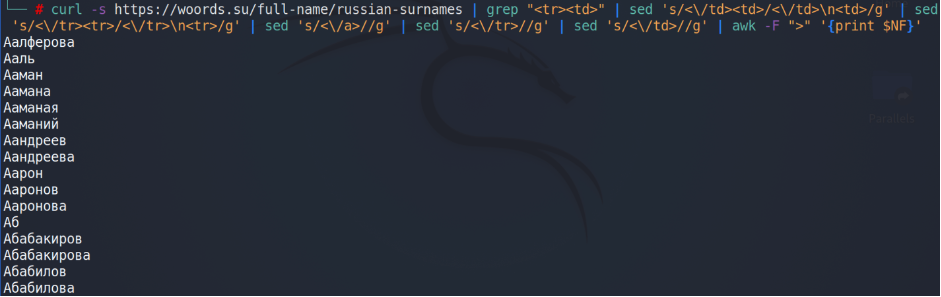
Excellent. The last thing we have to do is to go to each page, get the information and write it down to the file. Overall, we have 1593 pages, the link is https://woords.su/full-name/russian-surnames/page-1593.
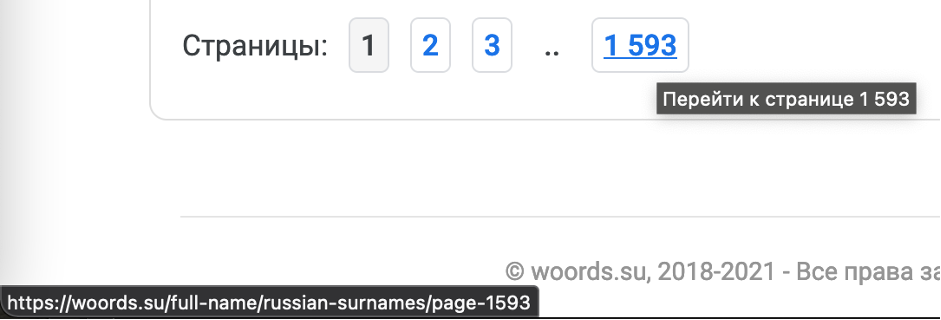
Let’s modify our previous script to get all of the surnames.
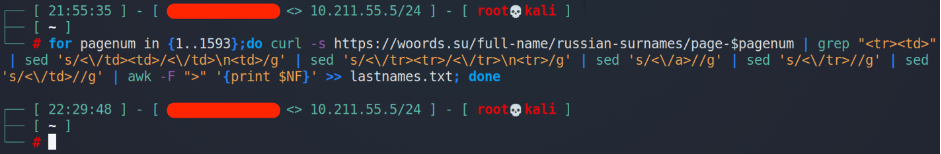
It took 34 minutes and 13 seconds to parse all of the surnames. Let’s check what we’ve got.
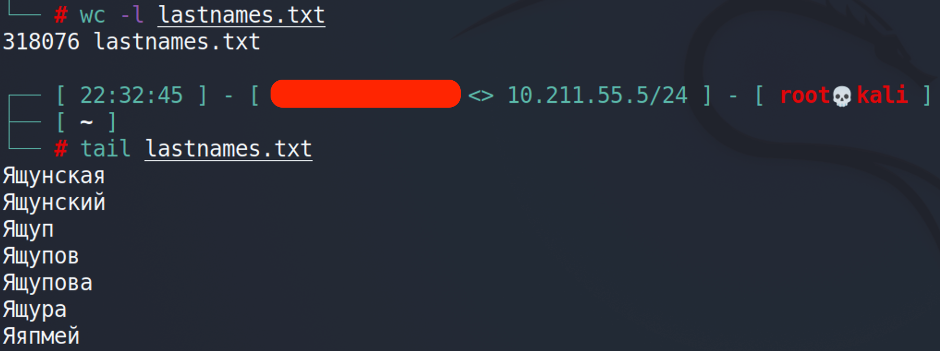
318076 last names. Pretty one harvest. What’s next?
- Transliteration
The next stuff we have to do is to transliterate gotten surnames from Russian into English. We have at least 2 possible ways: to write our own script or find related mechanism in the internet. I preferred to follow the second way and found a great web-site – https://translit.cc/
All we have to do is just copy/past our dictionary, click the button and wait for a while.
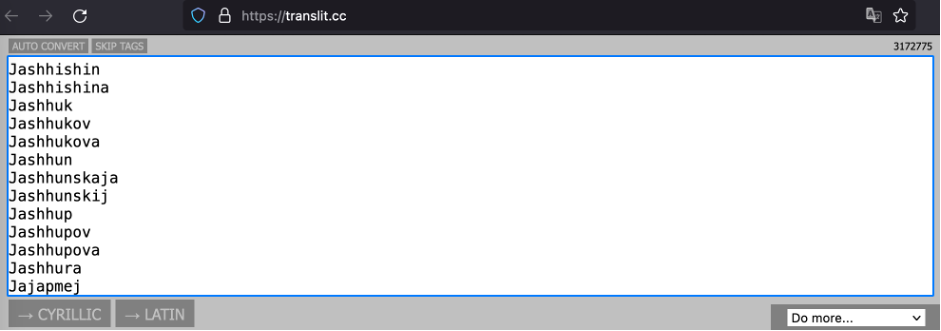
We got it. Now let’s save it into the new file.
That’s quite inconvenient to use uppercase so the next step is transforming all the letters into lowercase.
I have already had my own dictionary which consists of more than 30k surnames collected by the real AD pentests. So, the last thing we should do is to combine them into the one big file.
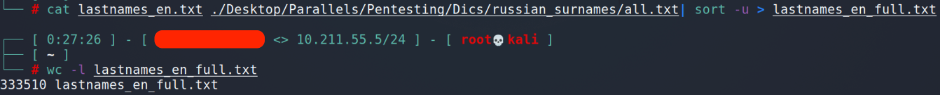
- Customizing
Ok, we have a huge dictionary with more than 333,5k surnames. Is it enough to start testing the AD? In some cases – yes, but generally – no.
As I mentioned earlier, the most famous pattern for the corporate username in the world is FLastname aka iglinkin@corporate.local. In that case we have to add a name letter before our surnames.
First of all, let’s generate a simple dictionary with the letters. We may even create that manually.
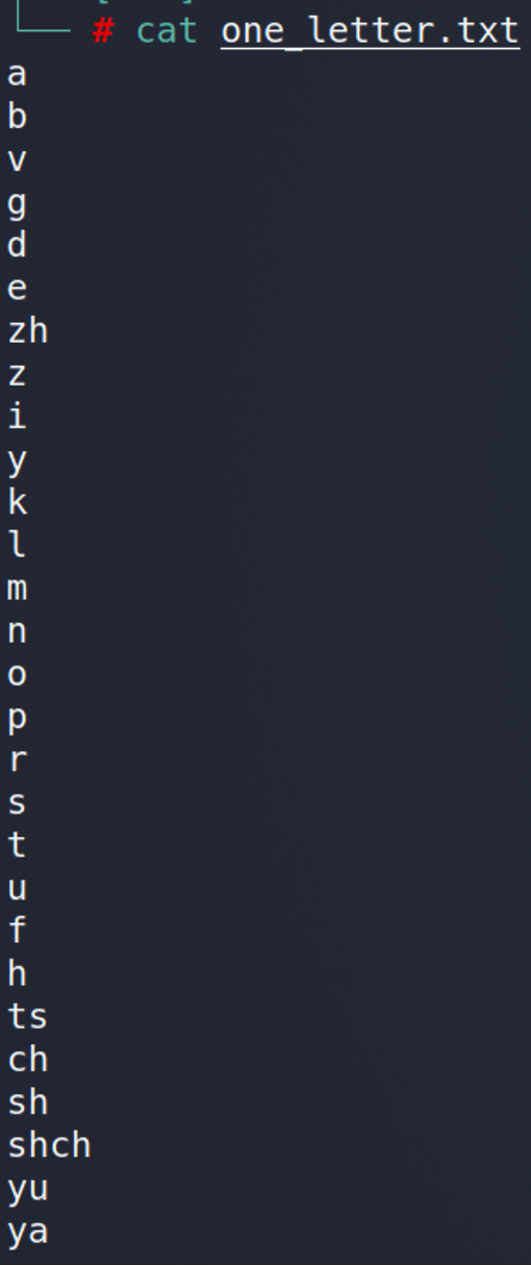
Do not be surprised about the sequence 🙂 It’s Russian alphabet transliterated into English.
The next step is adding each letter before each surname – what can be easier?
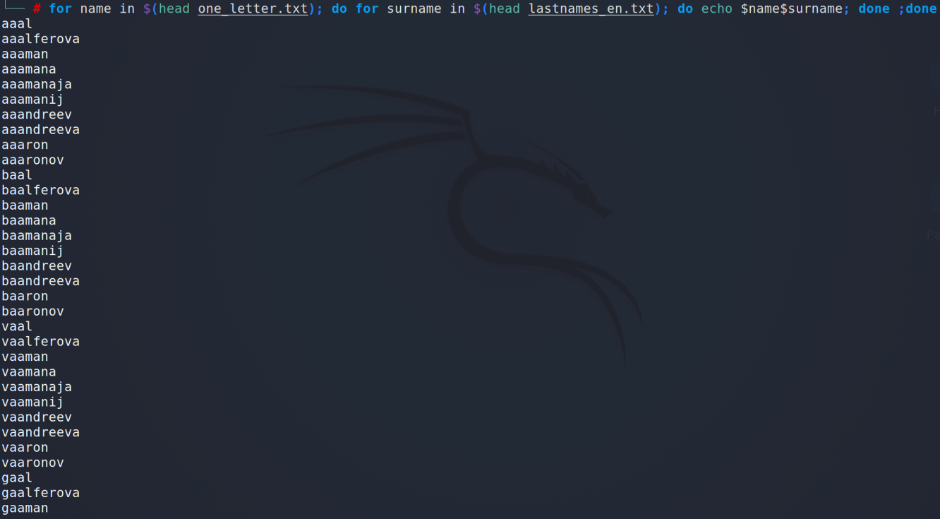
The full usernames list will consist of 9 004 770 logins. Can you imagine that?
Similarly, you may create your own dictionary for the particular purpose.
- Afterword
Using that universal dictionary you may create plenty of penetration testing attacks, including, but not limited:
- Kerbrute attack;
- Email password spray attack;
- Email spam attack (please, do not do it 🙂
- If the company has a specific email configuration, you may perform an email enumeration (when you got a respond that the email could not reach the server or something like that).
For your convenience, I created a new branch in my GitHub account – https://github.com/IvanGlinkin/Dics-for-Russian-AD. There is the full Russian surnames dictionary with more than 333,5k lines used in the current article and another related and useful lists. You are free to get and use them for your legal particular purposes (not for criminal aims) as well as adding additional surnames absented in the list.